Information Security Policies & Procedures A Practitioner's Reference, 2nd Ed pdf
Full text
Figure
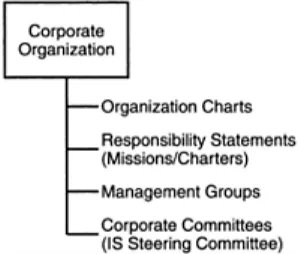

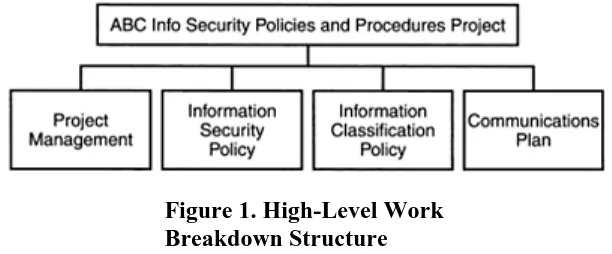
Outline
Related documents
2EiAEl5 To purchase a full-bngth recording of this All Flights Flesenved lncluding Public Penfonmance piece, go to alfred.com/downloads.. CAFIAVAI\I. By DUKE ELLINGTON and
The School of International Business offers an entirely unique and advanced type of degree pro- gram which, after four intensive calendar years of study and work, leads to
Amadeus generated Data Amadeus Travel Intelligence Engine Customer generated. Data (private) (incl. other GDSs)
The borrower at the borrower's expense, and in form satisfactory to the solicitors of McMaster University, shall give to the University a mortgage to be subject only to any
Create the highlight to the left of the interior vertical transition by shading the left area a 10 percent value, then lift off the horizontal teardrop-shaped highlight with
The classification of edges and the change in multiplicity of an The classification of edges and the change in multiplicity of an eigenvalue of a real symmetric matrix resulting
<Describe the organization¹s communication security policies, standards and procedures, including the organization¹s secure transmission capabilities, and how the
AUTHORITY: Subject to the terms and conditions of this policy and under the authority of ORS Chapter 293, the designated OST Fixed Income Investment Officer(s)