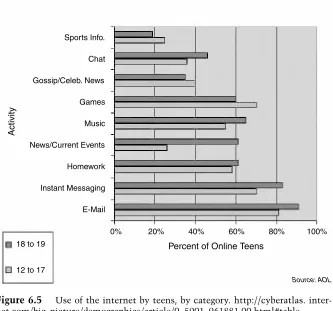
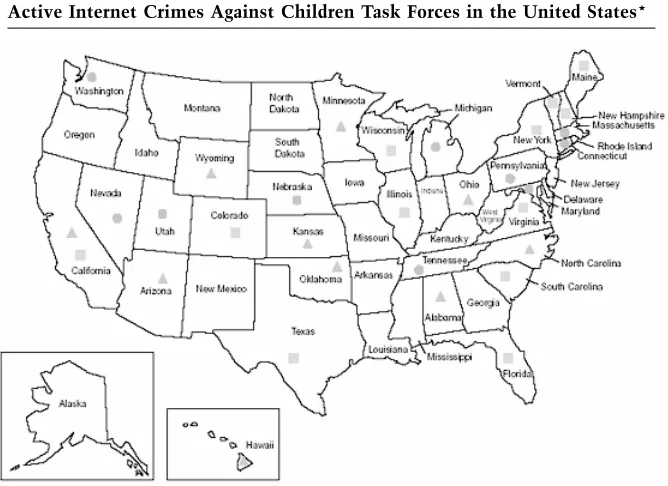
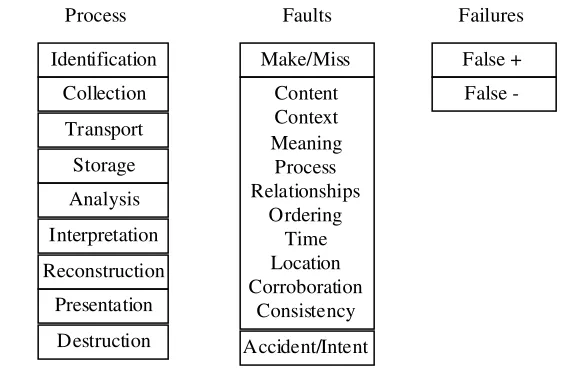
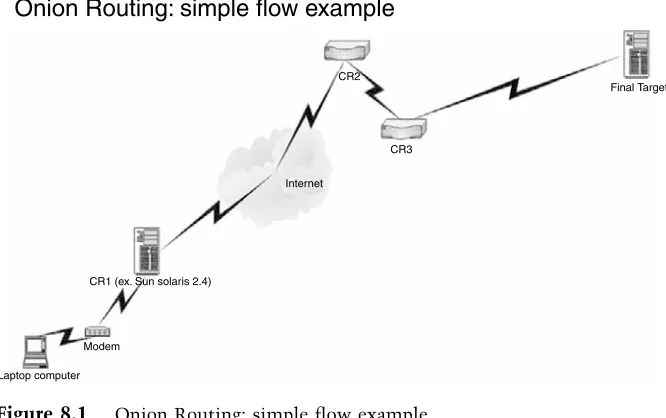
Forensic Computer Crime Investigation pdf
Full text
Figure
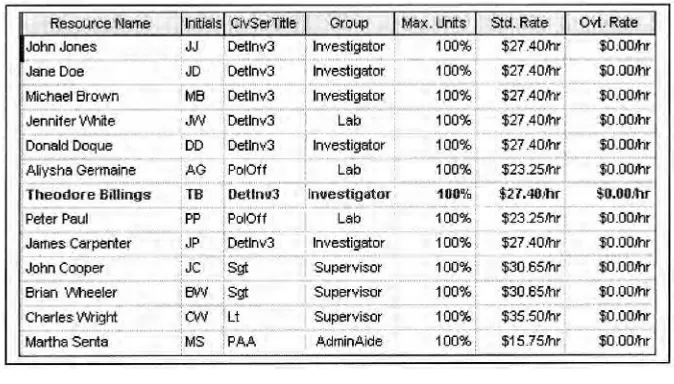
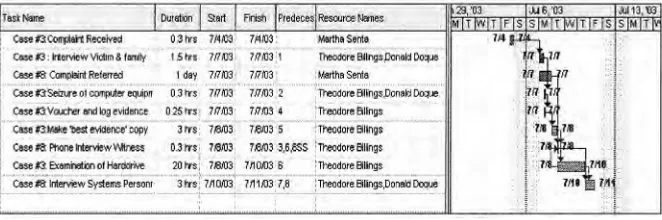

Related documents
We used both the bacterial and archaeal 16S rRNA gene sequences to design specific probes for fluorescence in situ hybridization (FISH). Samples collected during the 16 month period
»Budući da nije bitno kako se sjeme poljoprivrednika, šumara ili vrtlara kontaminiralo genetički modificiranim sjemenom, da li kroz međusobnu oplodnju, prijenosom peludi uz
R25 per uur vir addisionele ure 1.1.1 Bereken die normale loon per uur vir beide
Alternative voting rules, bargaining, and the efficiency of fiscal decisions – the optimal constitution?. Political Power and the supply of
The PROMs questionnaire used in the national programme, contains several elements; the EQ-5D measure, which forms the basis for all individual procedure
During all instrument approaches, the PF achieves and maintains a stable airspeed, descent rate, vertical flight path, and configuration by 500 feet below the FAF. Between 1000
b In cell B11, write a formula to find Condobolin’s total rainfall for the week.. Use Fill Right to copy the formula into cells C11
1. In the period between FX trade execution and final settlement, a bank is exposed to a number of different risks. The risks vary depending on the type