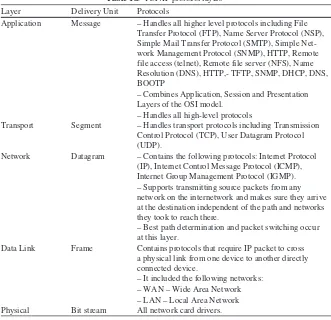
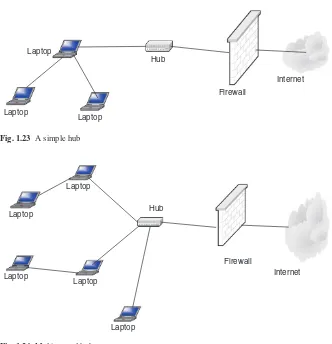
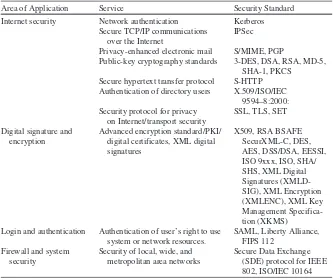
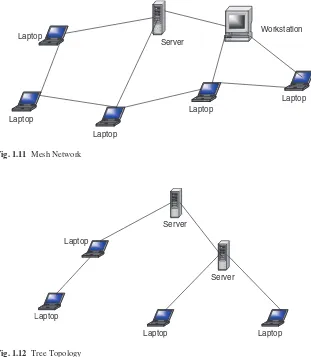
58 Guide To Computer Network Security [ PUNISHER ] pdf
Full text
Figure



Outline
Related documents
We find that compared with firms not complying with Section 404 (non-accelerated filers), firms complying (accelerated filers) are more likely to detect material errors in
Steered molecular dynamics simulations were conducted on the BNNT/lipid/water/ion system for the 2 nm length (10, 10) and (10, 0) BNNTs with a NaCl concentration of 140 mM. The BNNT
In vitro expression of the mutations Y493F, A429P and del234-241 KCNH2 showed a loss of hERG potassium channel function by reduction of the current, suggesting a
+11 years pioneering SaaS HR +4,000 customers $330M Revenue (2011) +15M Cloud Users 35 languages, 168 country presence Employee Central • Next Generation Cloud-Based HCM
Discussion: The results of the present study will help to understand the effect of physical exercise training on subsequent non-exercise physical activity, appetite and energy intake
Secondly, we define a unique unit speed non-planar geodesic on the right generalized cylinder whose base curve is the considered plane curve with a constant speed one divided
The Department of Social Security and the Department for Education and Employment have jointly commissioned a programme of research to evaluate the NDDP pilots from a variety
DEL Delete (low-profile only).. There are also six non-alphabetic control characters. Their names must appear in single quotation marks. These keys perform