A model-based approach for automatic validation of protection settings
Full text
Figure
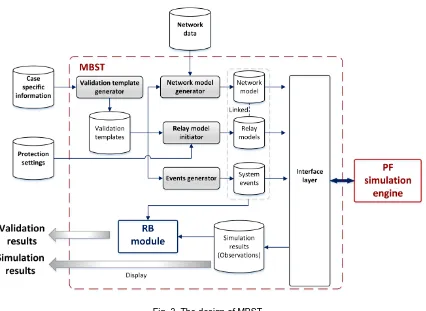
![Fig. 1. The principle of MBR [12]](https://thumb-us.123doks.com/thumbv2/123dok_us/1592459.111993/2.595.208.385.557.744/fig-the-principle-of-mbr.webp)
Related documents
The Eligible Services List specifically identifies network management and monitoring functionality as ineligible as a Basic Maintenance service, and makes no statement on the
Of these, 125 were intraosseous cystic lesions of the jaws of which, 81 (64.8%) were developmental in origin, 42 (33.6%) were inflammatory in origin and the rest of the
Surgical Site Infection Reduction Through Nasal Decolonization Prior to Surgery..
In order to obtain androgen-dependent prostate can- cer cell-specific antibody fragments, seven rounds of screening and enrichment were completed with a yeast- displayed scFv
ECHAM5 Fortran 90 BLAS, LAPACK, NetCDF MPI/OpenMP read at start, write periodically. NEMO Fortran 90 NetCDF MPI read at start,
Evaluation of Dermal Exposure to Polycyclic Aromatic Hydrocarbons Using DREAM Method in Production of Bituminous Waterproofing.. Archives of