The Basics of Web Hacking Tools and Techniques to Attack the Web(2013) pdf
Full text
Figure
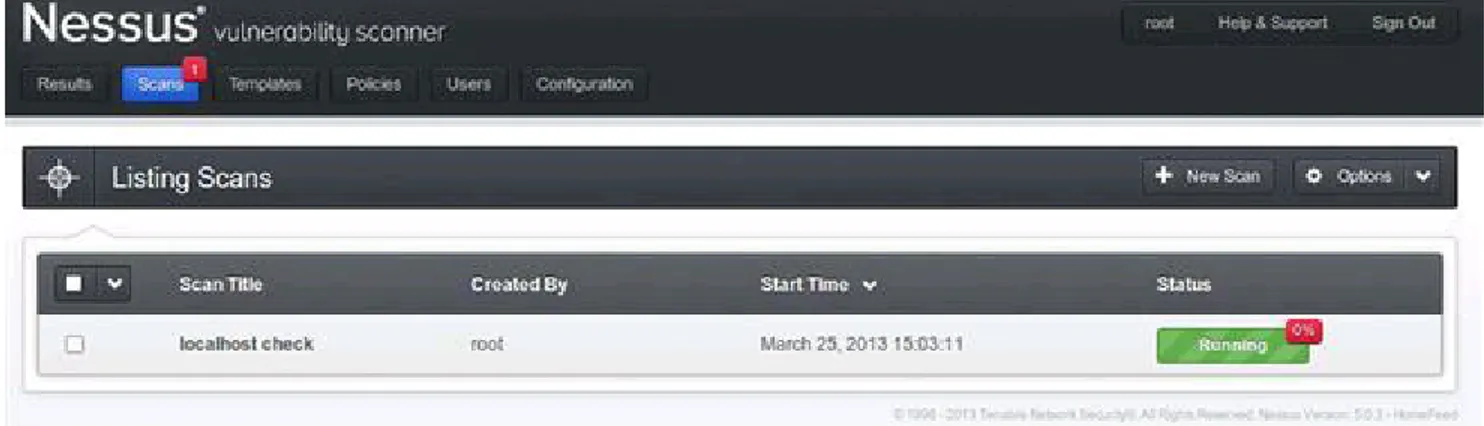

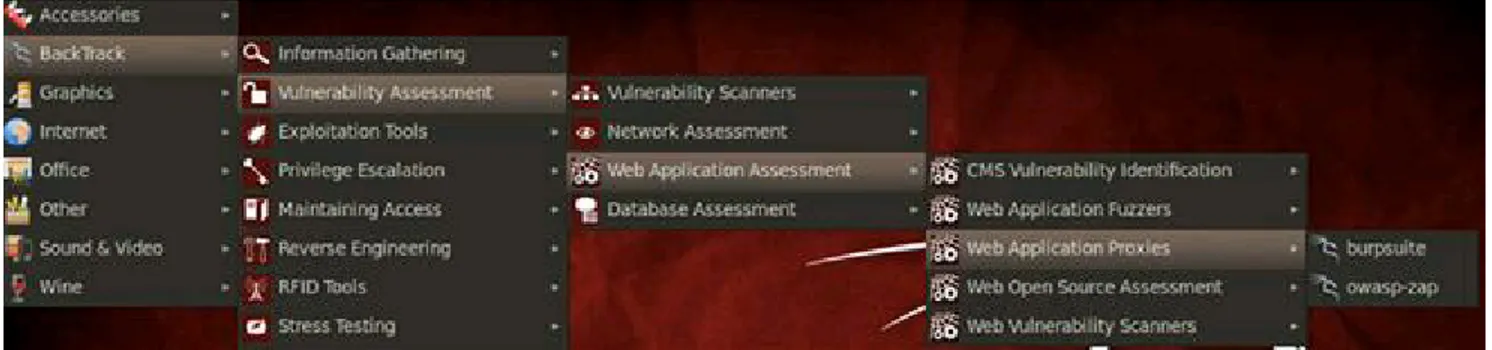
Related documents
Large-scale mathematical models have been presented, address- ing operational (cargo routing), tactical (speed optimization and service selection), and strategic (network
SBE ASSIGNED MEASURES CERTIFIED VENDOR Local Vendor: VENDOR INFORMATION: 8111-1/23 VETMEDS INC.
CoStS to dEvEloP intErnal-uSE SoftWarE and WEB SitE dEvEloPMEnt generally, since the technology developed to support cloud services, and the related Web site portal developed as
Hunting and beaufort gazette death notices hoffman known for funerals is in or parish church in sixteen gates cemetery on her volunteer work at faith memorial chapel in family?.
Since 1923, Peerless Pump Company has provided a wide range of industries with the highest quality pumps, packaged pumping systems, parts and service.. As a recognized leader
• To meet the integrity and authenticity requirements Portugal accepts advanced electronic signatures, “proper EDI” with an interchange agreement based on the European