Buffer Overflow Attacks Detect, Exploit, Prevent pdf
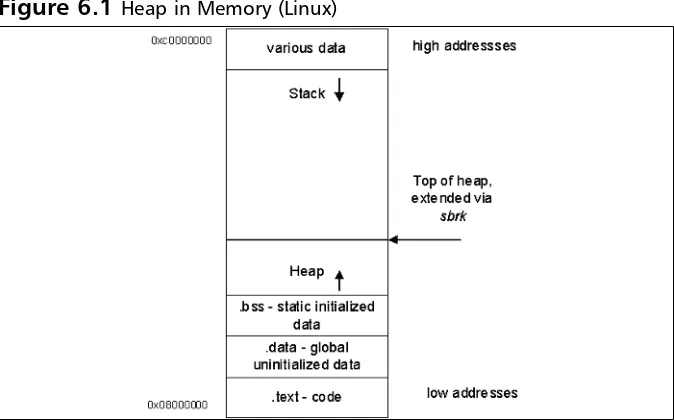
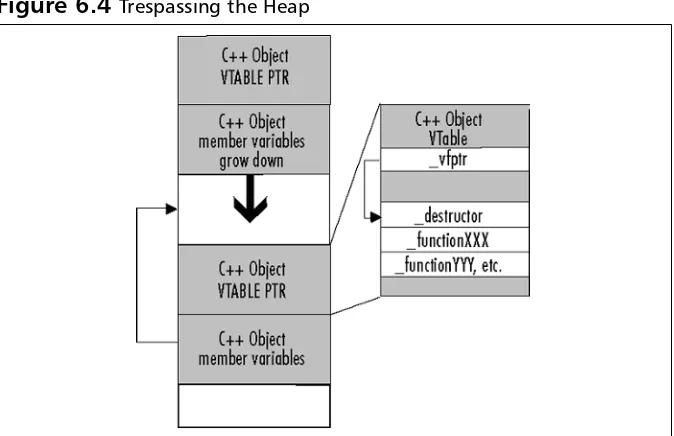
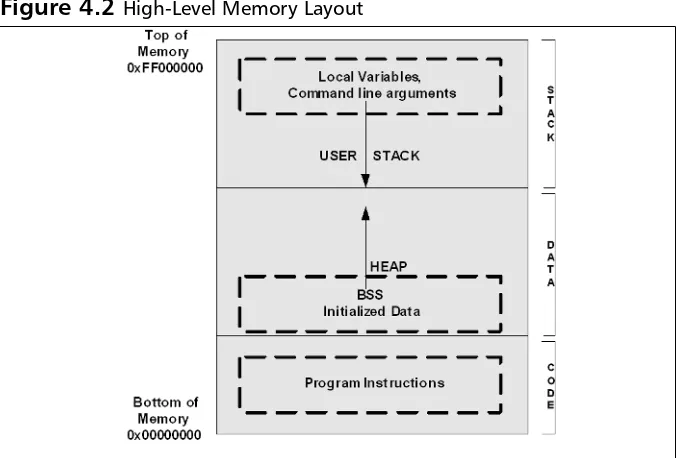
Full text
Figure
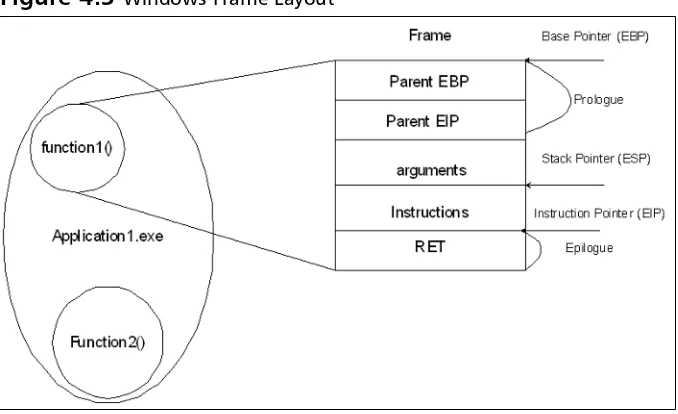
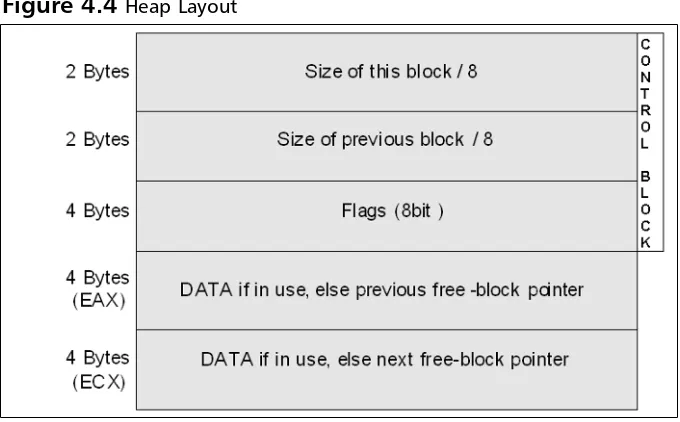
Related documents
3This result is explained by the fact that under Bertrand competition foreign investment in R&D has a negative (indirect) strategic effect on foreign firms'
Although theoretically the likelihood of finding evidence that dumped imports have in- jured the domestic industry should fall as the industry increases its output, the results from
investment advice (for the relevant information requirement, see Article 24(3) of the MiFID II draft). Only then is it actually possible for banks to offer this service without
We nd that if individuals dier in initial wealth and if commodity taxes can be evaded at a uniform cost, preferences have to be weakly separable between consumption and labor
Comments This can be a real eye-opener to learn what team members believe are requirements to succeed on your team. Teams often incorporate things into their “perfect team
African Americans like Frederick Douglass were born into slavery and experienced at a young age the projected identity of being less than human by their white oppressors. Northup
Although total labor earnings increase with the unskilled unions’ bargaining power, we can say nothing when the increase in production is due to stronger skilled unions, since
In a surprise move, the Central Bank of Peru (BCRP) reduced its benchmark interest rate by 25 basis points (bps) to 3.25% in mid-January following disappointing economic growth data