Authentication and key distribution for wired and wireless systems
Full text
Figure
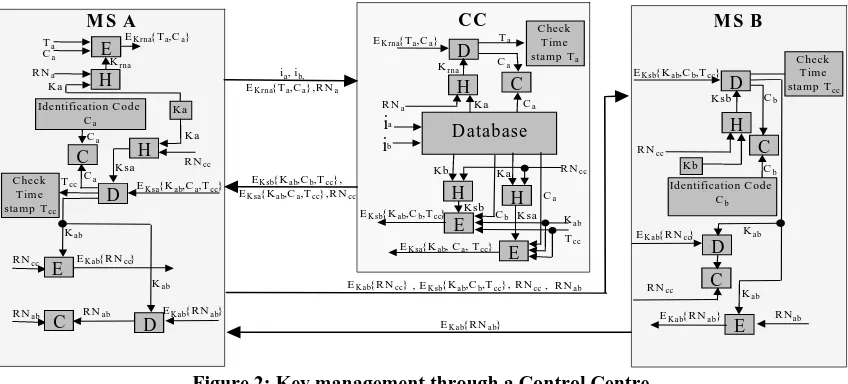
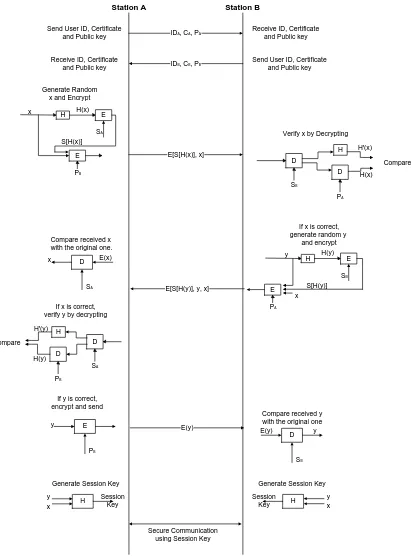
Related documents
Specifically, we consider optimal choice of the tightness, of the lag length and of both; compare alternative approaches to h -step ahead forecasting (direct, iterated
Also, for Chile, Korea, Pakistan, Philippines and Taiwan the lagged conditional volatility coefficients are higher in the second period and for Argentina, India
The ILS sensitive area (LSA) is protected by a system of red colored stop bars on Taxi- ways Echo, Foxtrot, Golf, Hotel, India and at the aircraft alternate parking positions, prior
Stage 1 of the Queensland Government’s Return to Play Guide outlines that no indoor or outdoor formal organised individual or team community sport or training will be permitted,
Wisconsin Precision manage- ment cited synergies and expanded service offerings as the main drivers for the acquisition.. The financial terms of the transaction were
To secure the Company’s assets, a Primary User may reduce the daily transaction limit of a particular service by accessing the “Administrator Management” through the Services or
In order to assess whether the above comments are appropriate when applied to research practice in Vietnam, where the capital market is not as developed as the countries in
Administrative and other delays are very common as most asylum seekers wait many years before receiving asylum. Some are never granted asylum, spend time in detention