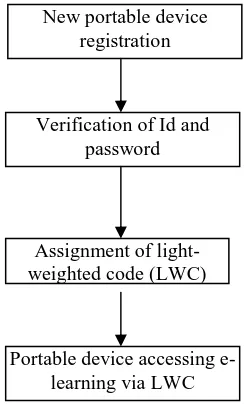
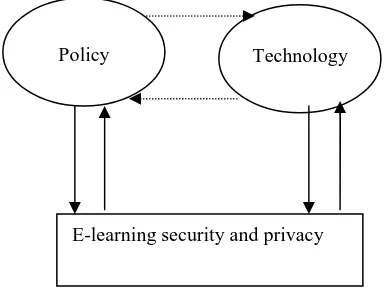
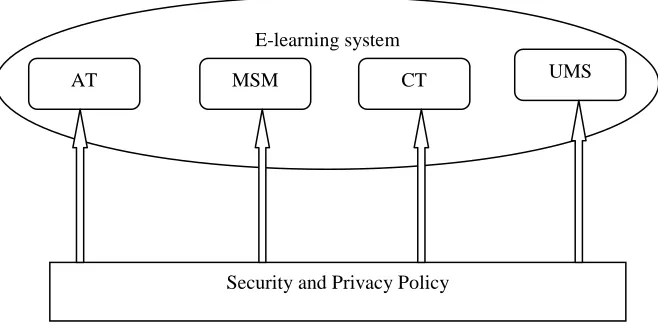
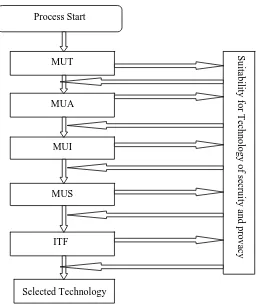
Security and privacy preservation for mobile e-learning via digital identity attributes
Full text
Figure
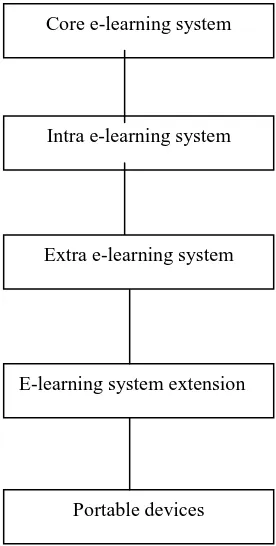
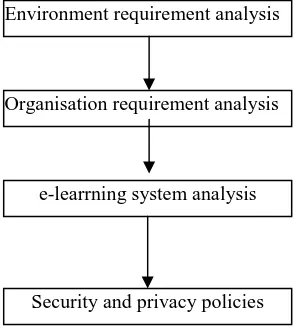
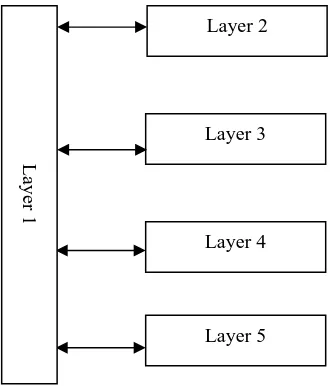
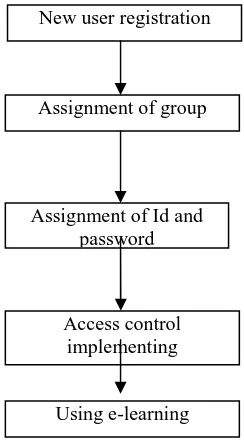
Related documents
Unfortunately the search for profit and opportunities has often avoided the poorest areas, the base of the pyramid (BOP), which has tended to be neglected by especially
This project studies the illegal use of private property — practices like squatting, farming, and scrapping — in the city of Detroit in order to answer two main questions: “How do
However, the expected profit in Spain, which is higher than in the other feed-in countries, is not due to a high support level, but rather to rela- tively low onshore wind
The demand for travelling in intact and relatively untouched nature is rising and governments see a great possibility to create revenue for the country. Due to the fact that
There were about 778 injuries and fatalities from various road traffic accident underreported to Motor Traffic and Transport Unit, MTTU, of the Ghana Police Service in the
The accounting method used by Compassion Suisse is based on the income collected. Income from sponsorship fundraising is recorded as due and is used to offset the expenses arising
Key words: Bacteria, Lactobacillus reuteri , Lactobacillus brevis , Aedes albopictus , midgut, ease of infection, persistence, protein
Results, obtained by means of a stochastic cost frontier analysis on samples of European-15 and Islamic banks during the period 1996-2002, show that the ratio of equity to