Twitter Scanner to Search Malicious URLs for Twitter Users
Full text
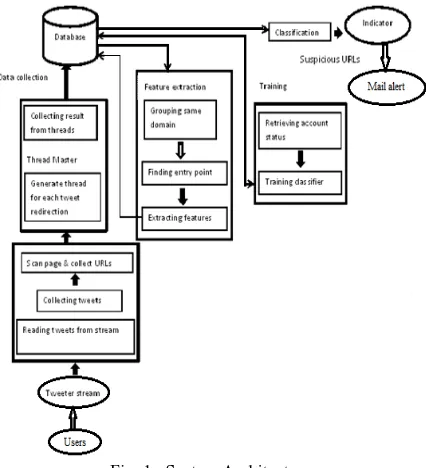
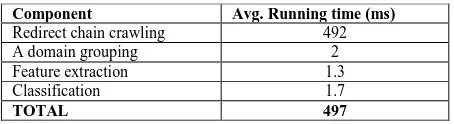
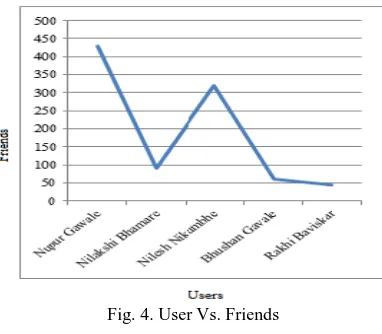
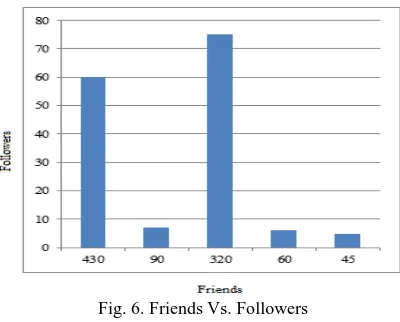
Figure
Related documents
Subrecipient agrees that, except with respect to the rehabilitation or construction of residential property containing less than eight (8) units, all contractors
In the particular case of the SHI scheme for the poor in Colombia, if coverage is expanded to enroll the poor-uninsured, out-of-pocket expenses would be reduced in about 50% at
Channel transmission losses are an “under-researched” hydrological process that affects resource availability in many semi-arid regions such as the Limpopo River Basin in
SKILLS DEVELOPMENT OPPORTUNITIES ELECTRICITY SYSTEM DESIGNER/ADVISER STREAM/ AGREEMENT LEVEL CAREER PATH/ GRADE DESCRIPTION TECHNICAL EMPLOYEE LEVEL 4 Salary
Grants increase during local election years, more funds are transferred to municipalities where the government party had higher percentages of votes, and where there
The mining process then determines highly informative features or feature combinations from the candidate sets that can be used as a steady source of auxiliary information
The applicant acknowledges their responsibility to obtain the required written assessment, written assessment plan, resident care agreement, and health care appraisal forms
Limitations on use of Performance Venues: The Center will reserve certain days for facility maintenance, and the facility, or such portion thereof as shall be determined by