Towards Secure Cryptographic Software Implementation Against Side-Channel Power Analysis Attacks
Full text
Figure

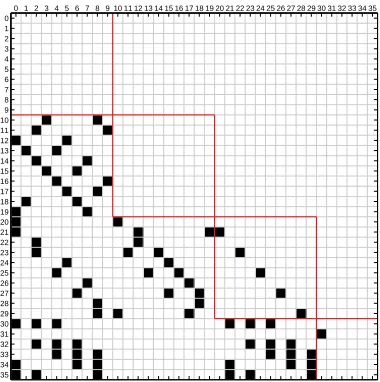
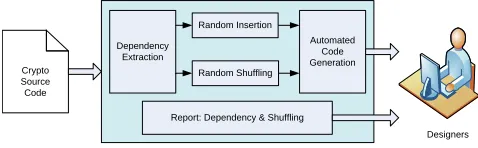
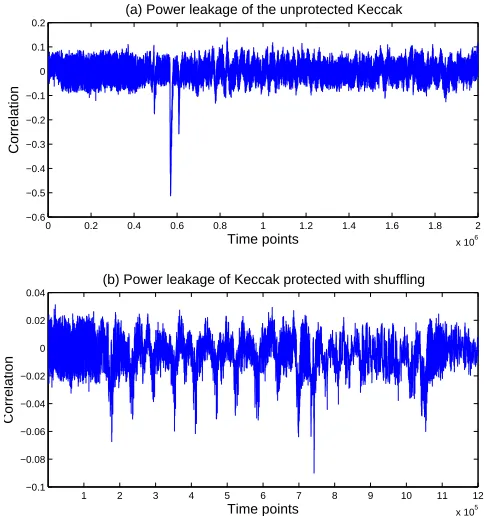
Related documents
The IRA (Prager, 1986), which has no previously reported estimates of reliability or validity in older adults who have relocated to retirement communities or assisted
In the previous sections, we dis- cuss the expectation that a neural network exploiting the fractional convolution should perform slightly worse than a pure binary (1-bit weights
Customer to pay any amount within ten (10) days after the amount is due and payable, b) abuse of the System or the equipment, c) dissolution, termination, discontinuance,
RL-29018F Ravenol Outboardoel 2T Teilsynth Ravensberger Schmierstoffvertrieb GmbH RL-29019G Ravenol Watercraft Fullsynth 2-Takt Ravensberger Schmierstoffvertrieb GmbH
An on-site garden, used either as wander space or a treatment environment or both, is perceived as improving quality of life, sleep, appetite, stress levels, and mood for
Based on conducted researches that showed the continuity of attachment styles during the life and individual’s adulthood romantic and intimacy relations are formed in the respect
During the thesis work, I measured six different parameters: the number of emergency processes, hash table entry number, caching replacement policy, cache entry
The clear favorite when looking at the breakdown plots for the canonical vectors is the projection pursuit method based on the Spearman correlation (PP-SPM).. The MSEs