Survey on Access Control and Management Issues in Cloud and BYOD Environment
Full text
Figure
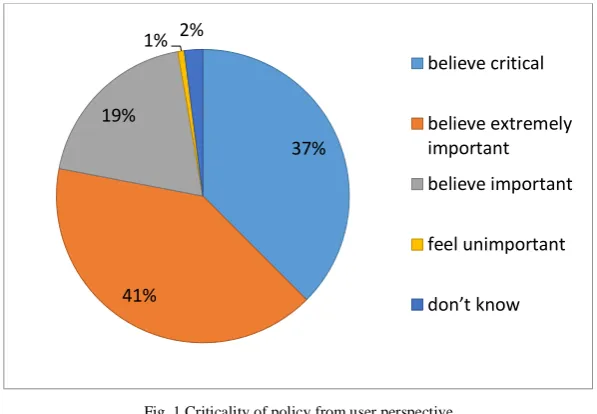
![Fig. 3 employees's opinion about who is the most responsible for securing BYOD devices [21]](https://thumb-us.123doks.com/thumbv2/123dok_us/1903310.1249239/7.595.131.466.258.449/fig-employees-s-opinion-responsible-securing-byod-devices.webp)
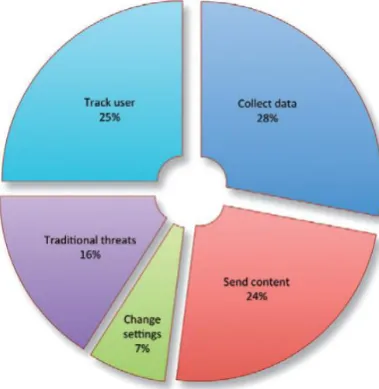
![Fig. 4 The main advantage of BYOD from employee’s perspective [40]](https://thumb-us.123doks.com/thumbv2/123dok_us/1903310.1249239/8.595.125.472.306.488/fig-main-advantage-byod-employee-s-perspective.webp)
Related documents
6:2 lid 1 Wft ondubbelzinnig blijkt dat onder "vermogensbestanddelen van de betrokken onderneming" niet alleen activa, maar ook passiva, verplichtingen, van de
In this way, the proposed count registers the line condition just once and applies its bearings to figure most of the photo lines' relating pixels in the goal picture.. The
If you want to file a complaint involving access to care, quality of care, communication issues with your primary care provider, or unpaid medical bills and you are enrolled in
Facts: PO2 Masi dispatched PO1 Pacis and PO1 Labaclado of the Station Anti-Illegal Drugs Task Force to conduct surveillance in Sampaloc St., Camarin, Caloocan City because of
These allies include but are not limited to: the Attawapiskat Education Authority, the Mushkegowuk Tribal Council, the Ontario Public School Boards Association, (members of
Anomaly series of SAT over the IP (upper panel, in ◦ C) Northwest precipitation (middle panel, in mm/month) and South- east precipitation (lower panel, in mm month − 1 ) in winter
For this particular abrupt cli- mate event, we identify which climatic change is most likely linked to water isotope change – changes in local precipita- tion amount, monsoon
Despite the importance of doctoral student education and preparation in the counseling profession, and, an extensive body of research about clinical supervision, there is a paucity of