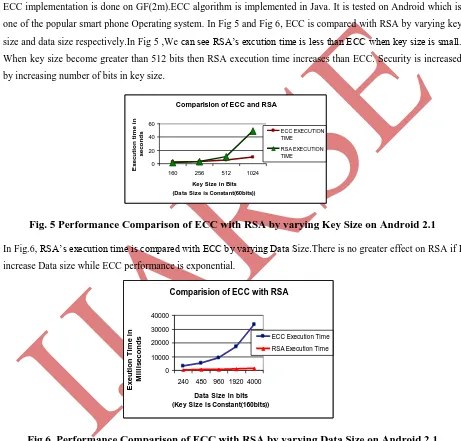
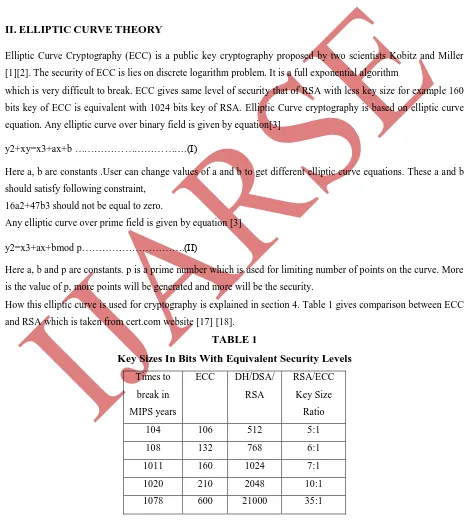
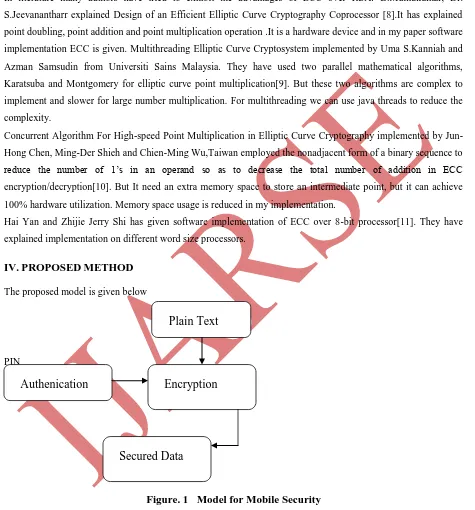
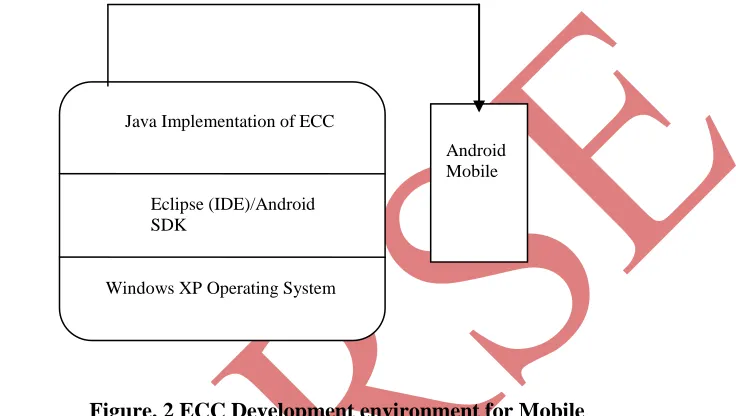
EXTENDING DATA SECURITY TO AVOID DATA FRAUDS ON MOBILE DEVICES
Full text
Figure
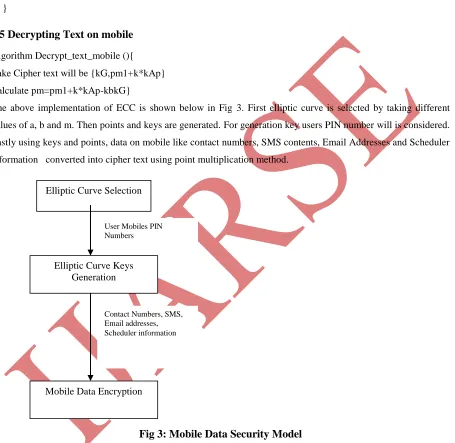
Related documents
The deviation of clustering coefficient C of the graph from the overall mean of the four groups as a function threshold T at three frequency bands..
A retrospective study of length of hospital stay in infants treated for neonatal abstinence syndrome with methadone and oral morphine preparations.
Whereas most previous studies have examined the relationship between these markets using pairwise exchange rates of the home country relative to other foreign currencies and the
Depending on the participant’s insurability, a participant can choose Option 1 and purchase a ten year term life insurance policy with a death benefit totaling ten years worth
The comparison of the share prices at the following two points of time has been made: (a) the market price prevailing before the announcement regarding buyback is made (here
Based on this argument modified Langmuir and Freundlich isotherms have been proposed in this work where initial concentration C has been incorporated in the
The purpose of this Special Report is to provide you with possible ways to stop foreclosure, explain why bankruptcy is NOT the best solution, and offer other insights into
[r]