The Effect of Restraint Stress on the Reactivation of Colitis in Acetic Acid-Induced Ulcerative Colitis Rat
Full text
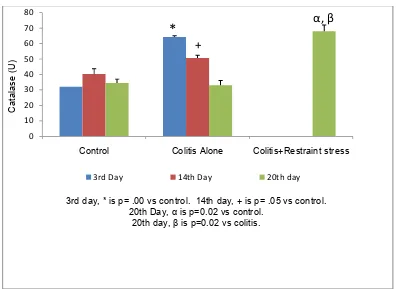
Figure



Related documents
On the other hand, explicit averaging strategies use average fitness values, obtained across a specific number of fitness evaluations, to ensure that evaluation of individuals is
The object of this study is to compare the effects of low-level laser therapy (LLLT), low-intensity pulsed ultrasound (LIPUS), and their combination on bone remodeling
employees under the old statutory default retirement age regime given prior to 6 April 2011 are invalid if they do not expressly state that the employee's right to request
ALP: Alkaline phosphatase; ALT: Alanine aminotransferase; AST: Aspartate aminotransferase; BUN: Blood urea nitrogen; CDC: The Centers for Disease Control and Prevention; CFR:
Thus, eight types of intelligence have been identified: verbal / linguistic intelligence, logical / mathematical intelligence, visual / spatial intelligence, body
As the results table shows, The diet of an equation of GDP, inflation rate in the first and third interrupt negative and positive relationship with economic growth
But only the efficiency of the internal control information will help to achieve the stated aims of management, to maintain stability and quality of the work, in future to move to a
The Crypto Ghost architecture consists of three main modules (i.e. key derivation, AES-GCM encryption and AES-GCM decryption) (as shown in Figure 5). Architecture of the