Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
Reinforcing Isolation Refuging in Personalized
Web Search
R. Saranya
1, R. Nithyarani
2PG Scholar, Department of CSE (with specialization in networks), Sethu Institute of Technology, Tamilnadu, India1
Assistant Professor, Department of CSE, Sethu Institute of Technology, Tamilnadu, India2
ABSTRACT: personalized web search is mainly used for improving quality of various web search.PWS provides the better search results which are based on user private information. The user creates the profile which contains user personal details. In existing system click log based and profile generalization methods are used to provide accurate result. But these methods are not efficient because, the click log search results based on user click query and Profile generalization result is based on recent search results. To overcome these problems two greedy algorithms are proposed. There are GreedyDP and GreedyIL. The client receives the user query and server replay the answer to the client. Finally, GreedyDP and GreedyIL is increased the efficiency of search engine. In the web search is used for privacy. Personalized web search is easy to applicable and protect the information. During the runtime algorithm is effectively to give the correct result. In the concept is preventing the interception data between other users. It is high-level of privacy to search the information. This provided accurate result from the search. The effectiveness framework is designing for the project. The framework allowed users to specify customized privacy requirements via the hierarchical profiles. The results also confirmed the effectiveness and efficiency of the solution.
I. INTRODUCTION
man-Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
in-the- inside attack, invading the server. Privacy is a major problem for PSW service. The existing methods do not take into account the customization of privacy requirements. This possibly makes some user privacy to be overprotected whileothers insufficiently protected. Many personalization techniques require iterative handler. Relations when creating personalized search results. They usually polish the search results with some metrics which require multiple user interactions. Personalized web search (PWS) has demonstrated its effectiveness in improving the quality of various search services on the Internet. However, evidences show that user’s hesitancy to disclose their private information during search has become a major barrier for the wide proliferation of PWS. Privacy protection in PWS applications that model user preferences as hierarchical user profiles. PWS framework called UPS that can adaptively generalize profiles by queries while respecting user -specified privacy requirements. Our runtime generalization aims at outstanding a balance between two predictive metrics that evaluate the utility of personalization and the privacy risk of exposing the generalized profile. Two greedy algorithms, namely GreedyDP and GreedyIL, for runtime generalization. To provide an online prediction mechanism for deciding whether personalizing a query is beneficial. Extensive experiments reveal the effectiveness of our framework. The experimental results also expose that GreedyIL significantly outperforms GreedyDP in terms of efficiency. As the amount of information on the Web increases swiftly, it creates many new challenges for Web search. When the same query is acquiesced by dissimilar users, a typical search engine returns the same result, irrespective of who acquiesced the query. This may not be suitable for us ers with different material needs. For example, for the query "apple", some users may be interested in documents dealing with “apple” as “fruit”, while some other users may want documents related to Apple computers. One way to determine the words in a query is to associate a small set of categories with the query. For example, if the category "cooking" or the category "fruit" is associated with the query "apple", then the user's intention becomes clear. Present search engines such as Google or Yahoo! have orders of categories to help users to specify their intentions. The use of hierarchical classes such as the library of Congress Classification is also common among librarians.
II. RELATED WORK
2.1 A Profile-Based Personalization
Personalized Web Search is mainly focus on improving the search quality. The basic idea of these works is to tailor the search results by mentioning to, often implicitly, a user profile that reveals an individual information goal. In the residue of this section, the previous solutions to PWS on two aspects, namely the depiction of profiles, and the degree of the efficiency of personalization. Many profile symbols are available in the literature to facilitate different personalization approaches. Earlier techniques utilize term lists/vectors or bag of words to signify their profile. However, most recent mechanism build profiles in hierarchical structures due to their stronger expressive ability, better scalability, and advanced access efficiency. The graded profile automatically via term-frequency investigation on the user data.In our proposed UPS framework. Actually, our framework can potentially adopt any hierarchical representation based on a taxonomy of information. As for the presentation measures of PWS in the literature, Normalized Discounted Cumulative Gain (NDCG) is a common measure of the effectiveness of an information retrieval system. It is based on a human graded relevance scale of item-positions in the result list, and is, therefore, recognized for its high cost in clear feedback collection.
2.2 Privacy Protection in PWS System
Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
nationals. They can agree to submit the query on behalf of who delivered it, or onward it to other neighbours. The faults of current solutions in class one is the high cost introduced due to the association and message. The solutions in class two do not require third-party assistance or associations between social network entries. In these solutions, users only belief themselves and cannot tolerate the exposure of their complete profiles an anonymity server. One main limitation in this work is that it builds the user profile as a finite set of attributes, and the probabilistic typical is qualified through predefined recurrent queries. These assumptions are impractical in the context ofPWS. A privacy protection solution for PWS based on hierarchical profiles. Using a user-specified verge, a generalized profile is obtained in effect as a rooted sub trees of the whole profile. Unfortunately, this work does not address the query value, which is crucial for the service quality of PWS. For comparison method takes both the privacy requirement and the query utility into account. The concept of personalized privacy protection in Privacy-Preserving Data Publishing (PPDP). A person can specify the degree of privacy protection for her/his sensitive values by specifying “guarding nodes” in the taxonomy of the sensitivequality.
III. PROPOSED METHODOLOGY
Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
Fig 1.Dataflow diagram
Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
actual for almost all kinds of queries, but are reported to be uneven under some circumstances. The profile-based PWS has confirmed more effectiveness in improving the quality of web search.
IV. EVALUATION
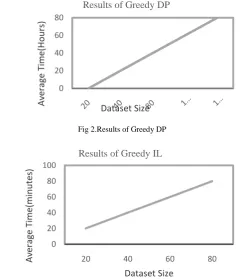
There are three operations are performed in this search, such as role based, online and offline.Rolebased means the result will be displayed in role based. Online means the searching will happened through online search engine. Offline means the result will displayed from the database. The two algorithm is processed correctly and finally retrieve the result from the personalized web search engine based upon the given user query. A greedy algorithm is a mathematical process that looks for simple, easy-to-implement solutions to multipart, multi-step problems by deciding which next step will provide the most obvious benefit. This algorithm is applied for pruning process. But it leads to computational cost increasingly. In fig.2 Greedy DP algorithm is a bottom up manner during the interaction to maintain best profile .The main problem of greedy algorithm discriminating power and privacy risk. The choice made by a greedy algorithm may depend on choices made so far but not on future choices or all the solutions to the sub tricky. It iteratively makes one greedy choice after another, reducing each given problem into a slighter one. In other words, a greedy algorithm never re-evaluates its choices. This is the main difference from dynamic programming, which is comprehensive and is guaranteed to find the solution. After every stage, lively programming makes decisions based on all the decisions made in the previous stage, and may re-evaluate the previous stage's algorithmic path to solution. To improve the recital of the Greedy DP algorithm apply the Greedy IL algorithm into the result. In fig.3 Greedy IL algorithm improves the efficiency of the simplification using heuristics based on several conclusions. One important conclusion is that any prune-leaf process decreases discriminating power of the profile. In other words, the DP presentations monotonicity by prune-leaf.
Fig 2.Results of Greedy DP
.
Fig 3.Results of Greedy IL 0
20 40 60 80
Av
era
ge
T
im
e(Ho
u
rs
)
Dataset Size
Results of Greedy DP
0 20 40 60 80 100
20 40 60 80
Av
era
ge
T
im
e(m
in
u
tes
)
Dataset Size
Pandian Saraswathi Yadav Engineering College, Arasanoor, Sivagangai, Tamilnadu, India
V. CONCLUSION
A client-side privacy protection framework called UPS for modified web search. UPS could theoretically be adopted by any PWS that captures user profiles in a hierarchical catalogue. The framework allowed users to specify customized privacy requirements via the tiered profiles. In addition, UPS also performed online generalization on user profiles to protect the personal privacy without compromising the search superiority. Two greedy algorithms are proposed, namely GreedyDP and GreedyIL, for the online generalization. Our untried results revealed that UPS could achieve quality search results while preserving user’s customized privacy requirements. The fallouts also confirmed the effectiveness and competence of solution. Future enhancement of this project is to developed security to the user query. Runtime user request to search query is privacy and do not intercept with other. As one future work, extend the deep classification algorithm for different kinds of applications, such as online advertisement grouping. Another work is to improve the efficiency of the search stage algorithm of deep classification. Develop more effective indexing algorithms to improve the classification performance.
ACKNOWLEDGEMENT
The authors acknowledge the contributions of thestudents, faculty of Sethu Institute of Technology for helping in the design of the search and for tool support. The authors alsothank the anonymous reviewers for theirthoughtfulcomments that helped to improve this paper. Theauthors would like to thank the anonymousreviewers for their constructive critique from whichthis paper greatly benefited.
REFERENCES
[1] LidanShou, He Bai, Ke Chen, and Gang Chen, “Supporting privacy Protection in Personalized Web Search”, 2014.
[2] A. Krause and E. Horvitz, “A Utility-Theoretic Approach toPrivacy in Online Services,” J. Artificial Intelligence Research,vol. 39, pp. 633-662, 2010.
[3] Z. Dou,R. Song, and J.-R.Wen, “A Large-Scale Evaluation and Analysis of Personalized Search Strategies,” Proc. Int’l Conf. World Wide Web (WWW), pp. 581-590, 2007.
[4] Y. Xu, K. Wang, B. Zhang, and Z. Chen, “Privacy-EnhancingPersonalized Web Search,” Proc. 16th Int’l Conf. World Wide Web(WWW), pp. 591-600, 2007.
[5] F. Qiu and J. Cho, “Automatic Identification of User Interest for Personalized Search,” Proc. 15th Int’l Conf. World Wide Web(WWW), pp. 727-736, 2006.
[6] K. Hafner, Researchers Yearn to Use AOL Logs, but They Hesitate, New York Times, Aug. 2006.
[7] X. Shen, B. Tan, and C. Zhai, “Context-Sensitive InformationRetrieval Using Implicit Feedback,” Proc. 28th Ann. Int’l ACMSIGIR Conf. Research and Development Information Retrieval (SIGIR), 2005.
[8] X. Shen, B. Tan, and C. Zhai, “Implicit User Modelling forPersonalized Search,” Proc. 14th ACM Int’l Conf. Information andKnowledge Management (CIKM), 2005.
[9] M. Spertta and S. Gach, “Personalizing Search Based on UserSearch Histories,” Proc. IEEE/WIC/ACM Int’l Conf. Web Intelligence (WI), 2005. [10] P.A. Chirita, W. Nejdl, R. Paiu, and C. Kohlschu¨ tters, “Using ODP Metadata to Personalize Search,” Proc. 28th Ann. Int’l ACM SIGIR Conf. Research and Development Information Retrieval (SIGIR), 2005.
[11]K. Sugiyama, K. Hatano, and M. Yoshikawa, “Adaptive WebSearch Based on User Profile Constructed without any Effort from Users,” Proc. 13th Int’l Conf. World Wide Web (WWW), 2004.
BIOGRAPHY
R.Saranyahas received B.Tech degree in Information Technology from PandianSaraswathyYadav Engineering College, sivagangai in 2011. She is currently pursuing Master of Engineering in Computer Science and Engineering (with specialization in networks) in Sethu Institute of Technology, Viruthunagar. Her areas of interest in research are Data Mining and Wireless Networks.