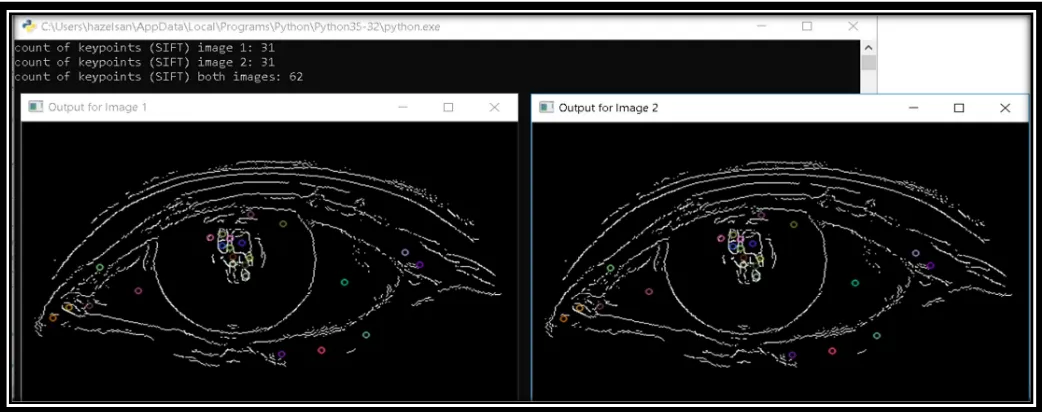
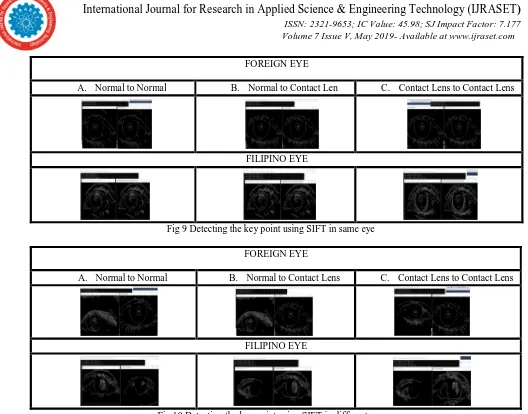
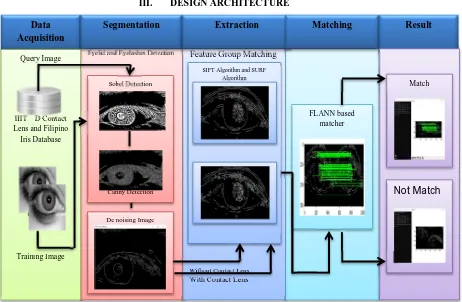
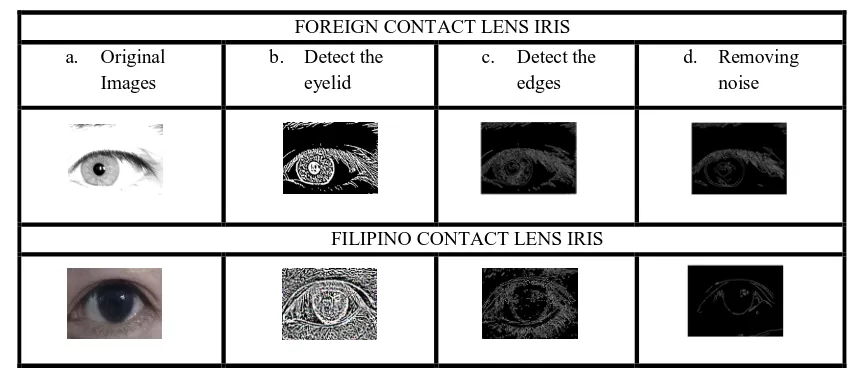
Contact Lens Detection for Security
Full text
Figure


Related documents
Additionally, during the development of this thesis some other studies explored the effects of mTOR inhibitors (particularly NVP-BEZ235 a dual PI3K/mTORC1/2 inhibitor
The estimated models also show that the assumption of symmetric e ff ects is rejected by the data (the coe ffi cients associated with the regressors in X it − are generally
The interaction of SW BA and the cubic term of calendar year is not signifi- cant, indicating that the long-term trend in radial growth does not change for beech trees growing in
implementation. Towers also now has the most complete offering of private exchange solutions in the industry, which we expect to be an incremental source of cost savings for
Anti-CD52 monoclonal antibody In the case of latent tuberculosis patients undergoing alemtuzumab therapy, concomitant treatment with isoniazid for nine months, rifampin for four
Somewhere neighbourhood plan now forms part of the development plan along with Cornwal Councill Local Plan, and will be used to assess the acceptability of planning applications
b GFP expression in the DN. The GFP expression is selectively observed in the DN of mice injected with the NeuRet-Cre vector. c GFP expression in the VA/VL and the CL. The
The purpose of this study is to study the prevalence and risk factors for cardiac autonomic neuropathy (CAN) and the utility of prolongation of corrected QT