Caught in the Act of an Insider Attack: Detection and Assessment of Insider Threat
Full text
Figure
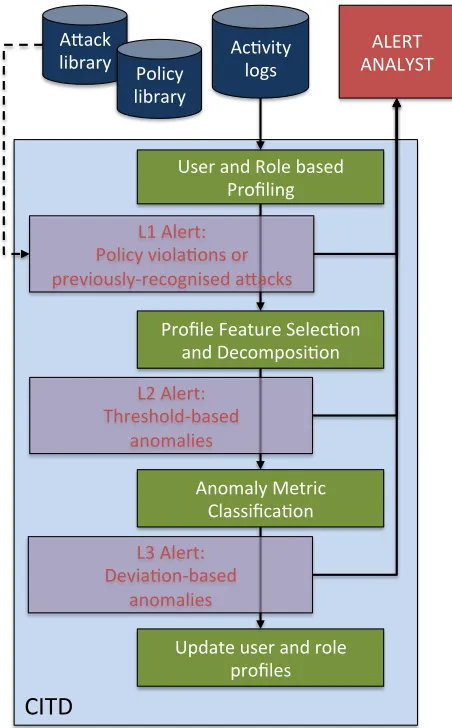
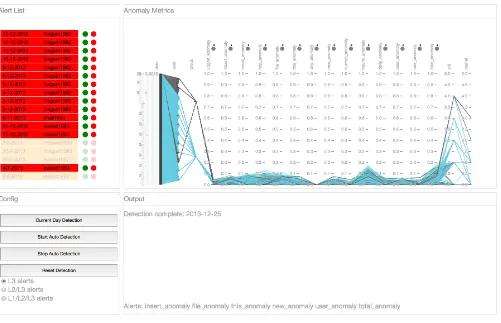
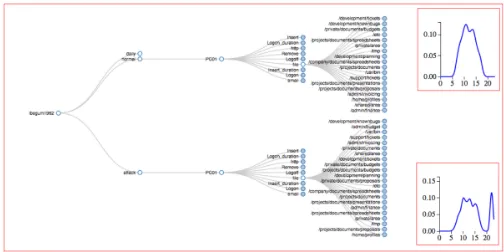
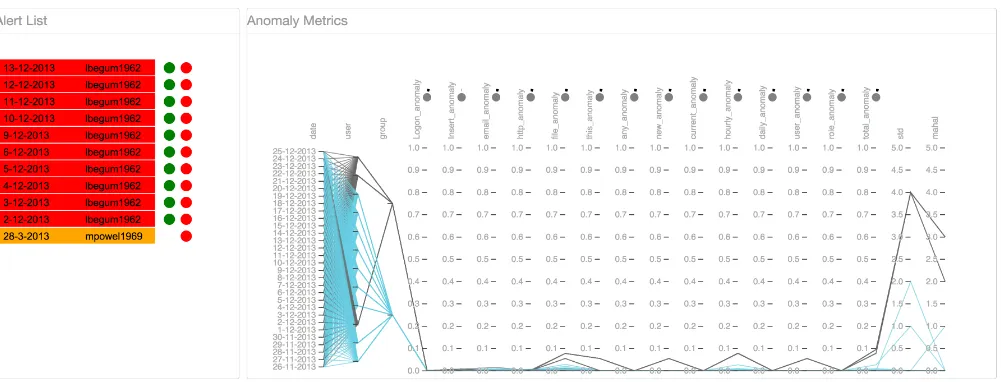
Related documents
In addition, the findings further reveal that none of the studies investigate the mediating effect of the nature of innovation (incremental and radical) on the relationship
This program introduces high school students to complex corporate transactions, takes them on enrichment trips to visit corporations, and hosts monthly meetings to revisit curriculum
Another interesting type of topology is the one using a central mediation element for data transfer between systems (Goel 2006), which is called a message broker or
This study employed an opportunistic sample of patients with psychosis and substance use who were participating in a multi-centred clinical trial evaluating Motivational
Areas under the ROC curve determine the predicative performance of adult excretory/secretory (ES) products (A), tegument proteins (B), egg ES products (C) and soluble egg antigen
This study employed quantitative and qualitative methods and aimed to examine and develop routes for halal traveling in the five southern bordered provinces in
Cultural archiving challenges: self-determination, land tenure, and educational dissemination Participation in language archiving projects can be challenging for Native
shall be deposited as offsetting collections into the Department of Homeland Security Science and Technology “Research, Development, Acquisition, and Operations” account and,