Biometric PKI Authentication System Using Fingerprint Minutiae
Full text
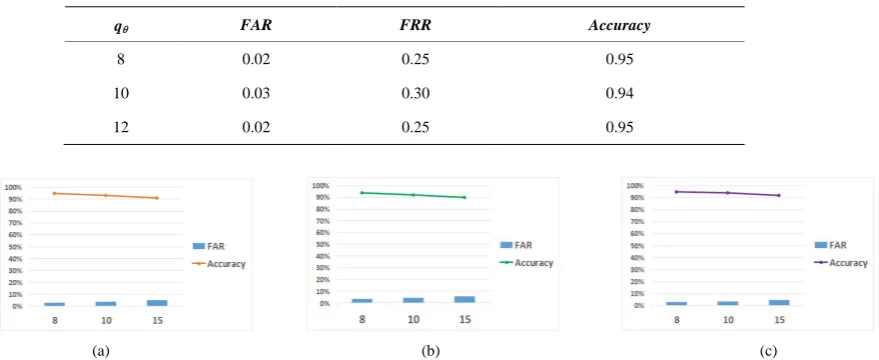
Figure

Related documents
Guaranteed algorithms for scheduling applications struc- tured as parallel task graphs (PTGs) have been developed in the case of a single homogeneous parallel computing platform,
In Reverse Osmosis process the fresh water is forced in to one side of the vessels, the raw water is travel through the membrane, its removing the salt and other micro
The physico chemical parameters such as water temperature, turbidity, pH, total dissolved solid, total suspended solid , total solid conductivity (µs/cm),
Audit your current data security and protection, including backup and restore procedures, tape drives or other onsite backup devices to validate if all of your data is actually
The workload components evaluated in our study include all tasks in TB diagnosis and care, all registra- tion, supervision and training-related time spent by service delivery staff
For this reason, new indicators relate to the wider impacts of transport operations on the environment are defined: fuel and energy consumption, expressed in liters or tonnes of
Research objective focused on different amplifiers such as erbium doped fiber amplifier, Raman amplifier and semiconductor optical amplifier, have been investigated