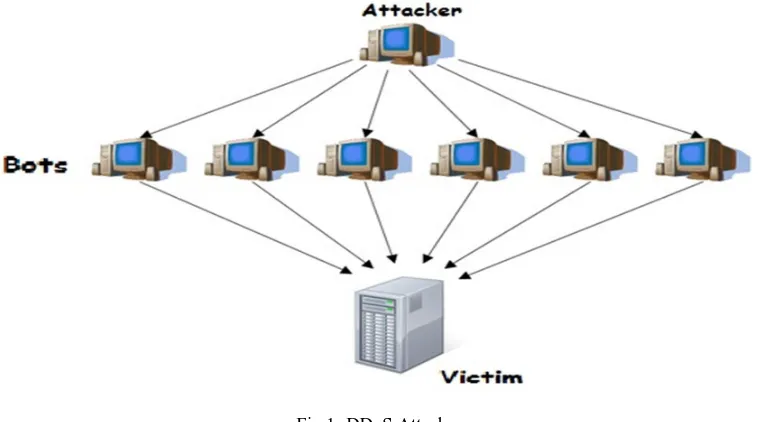
Detection and Classification of Distributed Denial of Service (DDoS) Attack
Full text
Figure
Related documents
The role played by the Lucas organisation was crucial in the planting of Ballarat’s Avenue of Honour, the building of its Arch of Victory, the long-term civic management of the
This qualitative study focused on the experiences of immigrant Nigerian women who are in current leadership positions in the United States and what impact the United States
In order to reflect the actual traffic damage after disaster occurs, many factors should be considered and those factors includes the damage proportion of the whole distance and
Evidence for real estate wealth – where FCM holders have a slightly higher median but at the same time a slightly lower mean than DCM holders – is mixed (table 1). At any rate, FCM
tier Targeted Development Areas is developed. This could be done in conjunction with the Jaffrey Conservation Commission and would be a helpful guide for decisions
At IndiaWebDevelopers, e-learning solutions include e-learning development, interactive learning, online learning, instructional design, learning management systems, online
N OTE : In the upper panel, the height of each bar denotes the number of FOMC participants who judge that, under appropriate monetary policy and in the absence of further shocks
I express great appreciation to ANTAQ (Brazilian maritime authority), Brazilian Port of Itaqui authorities and specially Vale Operations and Management teams in