A comparison of discrete cosine transform and discrete wavelet transform algorithm in watermarking against common attacks
Full text
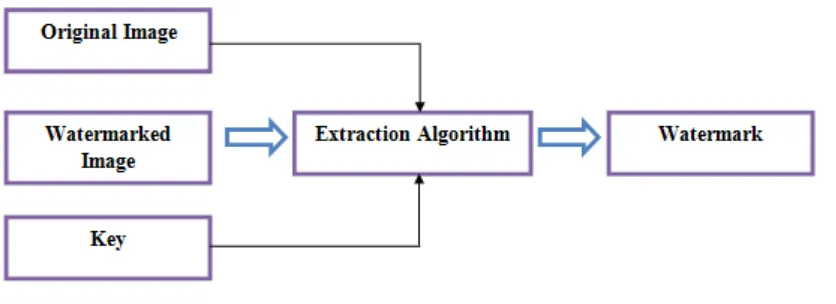
Figure



Related documents
These proxy-advisory firms specialize in collecting information about upcoming corporate votes, processing it, and providing advice to their institutional clients about how to
This study was meant to address the issue of health insurance penetration, especially by the National Hospital Insurance Fund), among the low income groups of the society in Kenya..
Considering the relapse of treated open bite in six patients during the retention phase, it seems that fixed retainers alone were not absolutely sufficient for maintaining
The list of plant growth regulators used in the tissue culture of Canna for the formation of callus, somatic embryo, shooting and rooting are provided in table I..
Pharmacognostic standardization, physic- chemical evaluation of the leaves of Caryota urens was carried out to determine its macro-and microscopical characters and also
Since the data demonstrate differential recombination in the two sexes (lower in the female) the estimate obtained for the male is a minimal figure, and the
Section 2 includes a step by step procedure for the design of proposed antenna, viz., design of a UWB monopole antenna, employing band notch structures, and achieving


