AUTHENTICATION ARCHITECTURE USING THRESHOLD CRYPTOGRAPHY IN KERBEROS FOR MOBILE AD HOC NETWORKS
Full text
Figure


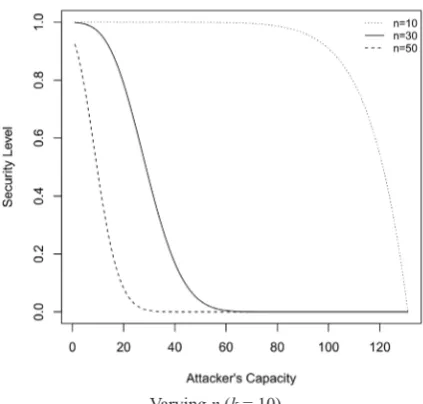

Related documents
We found no significant difference in the rates of insignificant and high- risk prostate cancer between men ≤ 55 years and >55 years, in either the prostate biopsies or
Deworming of stray dogs and wild canines with praziquantel-laced baits delivered by an unmanned aerial vehicle in areas highly endemic for echinococcosis in China.. Qing Yu 1,2,3*
Significant efforts were made to provide genomic and bioinformatic data as downloadable files, including raw sequencing reads, genome maps, gene annotations, protein functional
This study directed to investigate and determine the genetic diversity and relationship of the tidal swamp rice germplasm of the South Kalimantan Province, Indonesia using
We address here gaps in our understanding of the link between non-crop vegetation in field margins and pest suppression by using a system of partial differential equations to
ABSTRACT: Empirical Analysis of software projects: Software projects is not a perfect clone of software engineering, but it borrows many of software
The aim of this observational real time study is to deliver exact data about physicians' work at hospitals of different ownership.. Methods: The consequences of different
Framework for the establishment of a feasible, tailored and effective perinatal education programme Artieta Pinedo et al BMC Pregnancy and Childbirth (2017) 17 58 DOI 10 1186/s12884