Security against Phishing Attacks
Full text
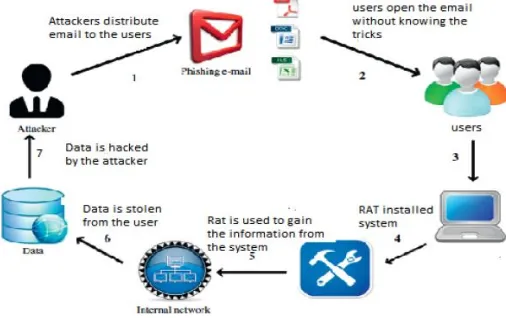
Figure


Related documents
Ethernet Features 10 Mbit/s operation (10BASE-T; IEEE 802.3i; IEEE 802.3 clauses 13-14) 100 Mbit/s operation (100BASE-TX; IEEE 802.3u; IEEE 802.3 clauses 21-30) 1000 Mbit/s
Their method uses effective field theory and re- places the extended object by a point particle, whose interactions (or effective world-line action) encode all of its
CoStS to dEvEloP intErnal-uSE SoftWarE and WEB SitE dEvEloPMEnt generally, since the technology developed to support cloud services, and the related Web site portal developed as
Diese Lösung wurde erstellt von Julia Umschaden. Sie ist keine offizielle Lösung des Ministeriums für Schule und Weiterbildung des Landes Nordrhein-Westfalen.. a) Diwali (= “row
A random analysis of campaign messages sent to 61 million Facebook users during the 2008 elections found that they directly influenced political self-expression, information
This collection contains apparel, memorabilia, and photographs collected by John Martin during his tenure as Volleyball Coach and Associate Athletic Director for Facilities
Further- more, combining this foreground selection approach with background selection for the recurrent parent genotype Table 1 Chromosome locations associated with resistance
However, the question remains as to the extent of this ontology in contemporary Cambodia: are Khmer artists and Khmer people in general constantly in the presence of their