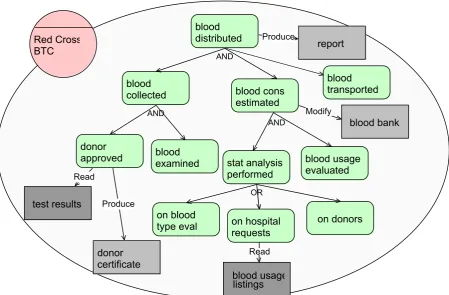
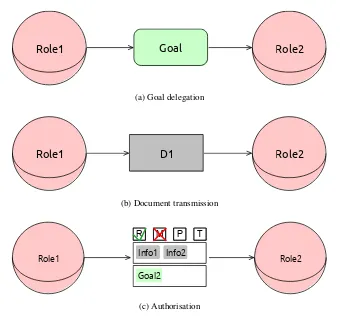
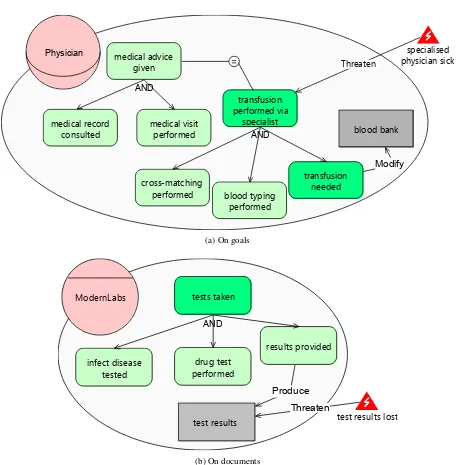
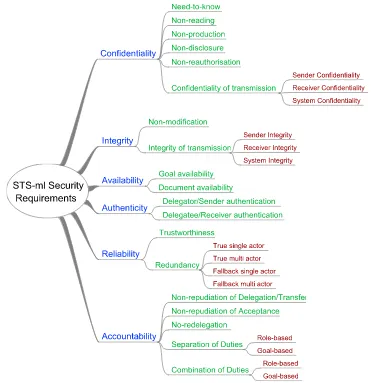
STS: a Security Requirements Engineering methodology for socio-technical Systems
Full text
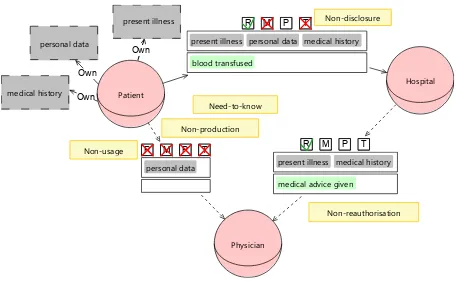
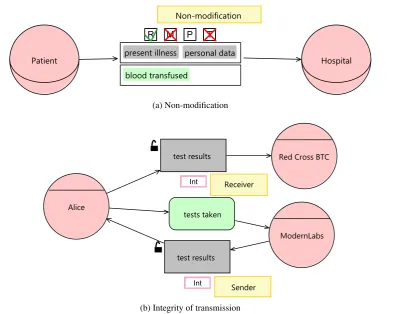
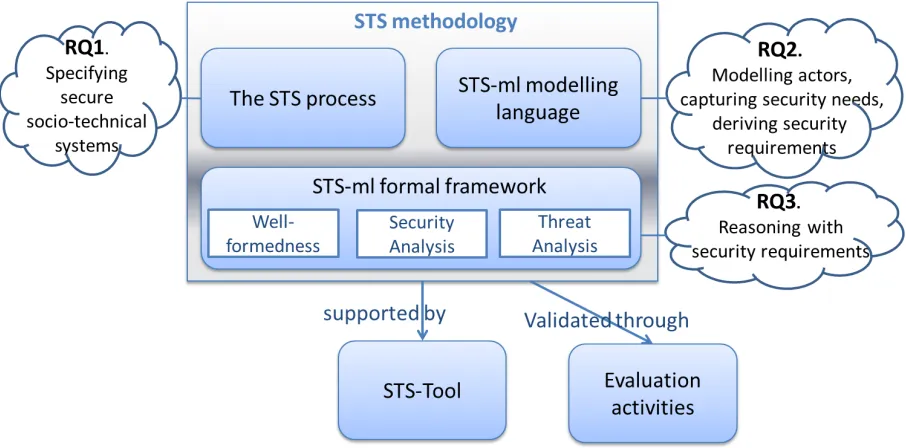
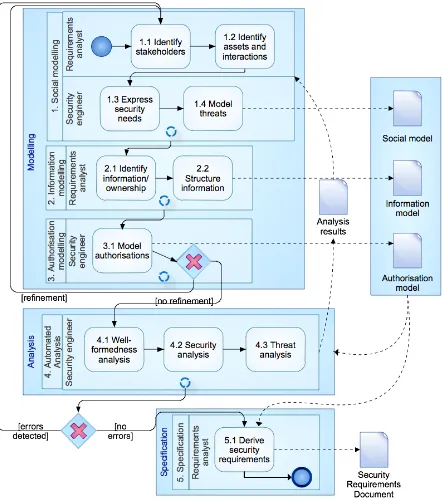
Figure
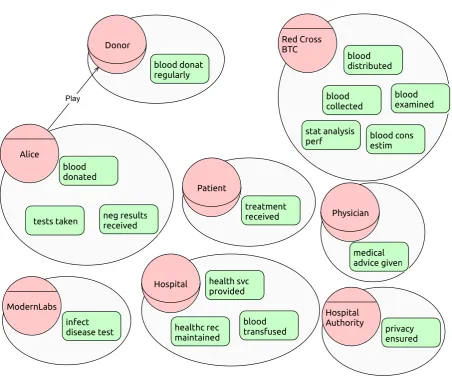
Related documents
Using text mining of first-opinion electronic medical records from seven veterinary practices around the UK, Kaplan-Meier and Cox proportional hazard modelling, we were able to
more than four additional runs were required, they were needed for the 2 7-3 design, which is intuitive as this design has one more factor than the 2 6-2 design
implementing intervention schools need to understand students role in bullying (e.g., bully, victim, bully-victim, defender, outsider) to appropriately target the behaviors
Minors who do not have a valid driver’s license which allows them to operate a motorized vehicle in the state in which they reside will not be permitted to operate a motorized
4.1 The Select Committee is asked to consider the proposed development of the Customer Service Function, the recommended service delivery option and the investment required8. It
• Follow up with your employer each reporting period to ensure your hours are reported on a regular basis?. • Discuss your progress with
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
Proprietary Schools are referred to as those classified nonpublic, which sell or offer for sale mostly post- secondary instruction which leads to an occupation..