TERRORISM CONTROL BY USING EXISTING AD-HOC NETWORK (TCEAN)
Full text
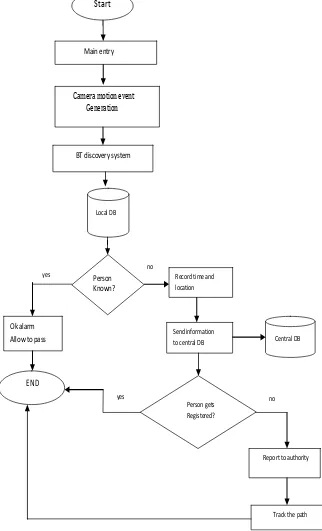
Figure


Related documents
For instance, IEEE Xplore (IEEE) and ACM Digital Library (ACM) mainly contain computer related journal and conference papers that are published by IEEE and ACM respec- tively
The four key priorities of research and innovation policy continue to be: (a) keeping pace with global technology trends, (b) providing funding for public and
"If the people creating a product that will later be localized for sale in other countries do not factor that future localization into their plans, the localization effort ends
Multimedia networking (routing, QoS management, pricing), Multimedia applications (3D protocols, multi-camera tele-!. immersive systems, mobile multimedia, P2P
Returning to the lexical options that are used to realize the other main thanking components including acknowledging supervisors and other academics, resources, and moral
The first data set used in the cross-reference study was taken from ‘‘Soil Species of China (six volumes)’’ (The Office of the Second National Soil Survey of China, 1993, 1994,
For illustrative purposes, the functional outcome of the group of total femur endoprosthetic replacement patients was compared to that in groups of patients treated with proximal