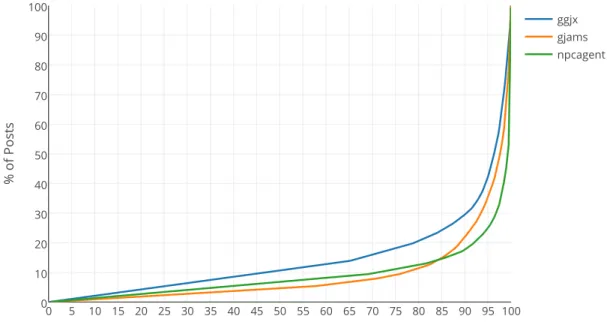
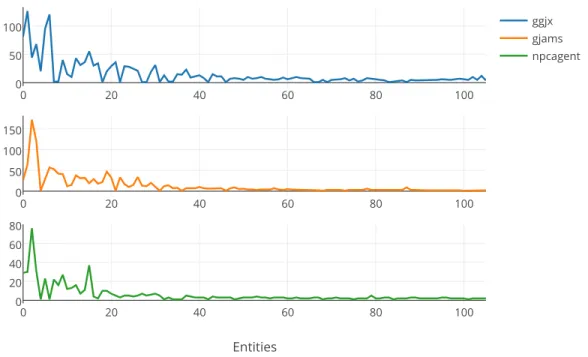
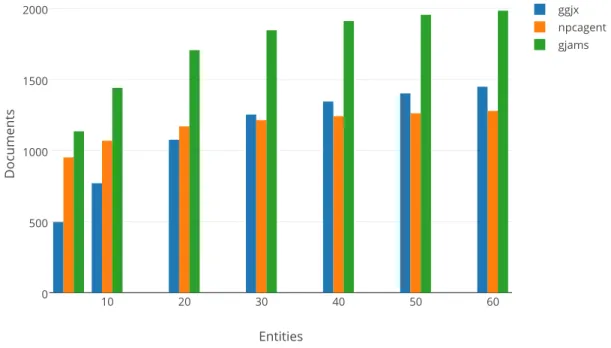
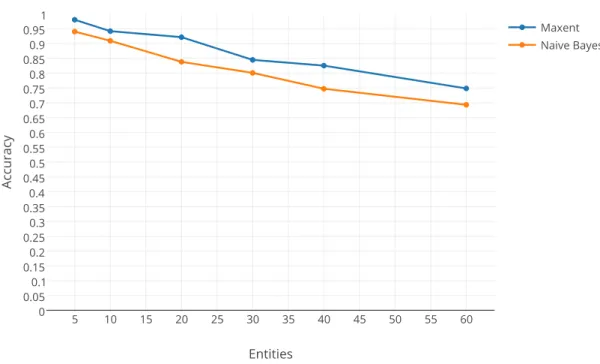
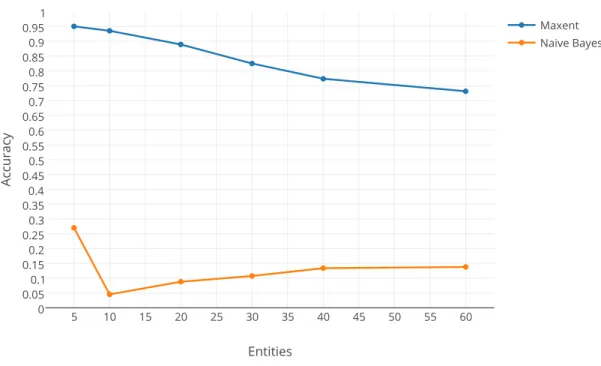
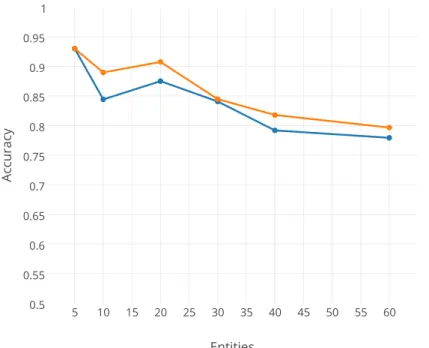
Categorizing Blog Spam
Full text
Figure
![Figure 2.1: The Main Steps Involved in a Spam Filter [11].](https://thumb-us.123doks.com/thumbv2/123dok_us/1417264.2689708/19.918.194.765.198.464/figure-main-steps-involved-spam-filter.webp)

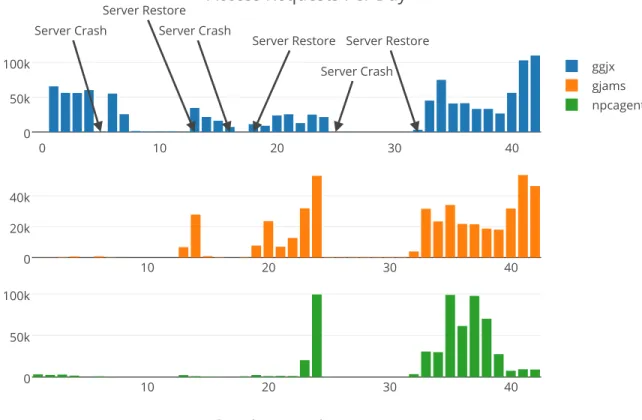
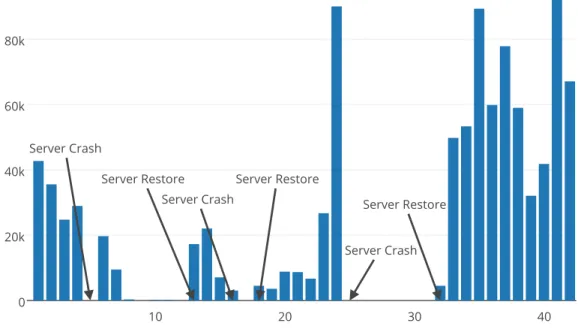
Related documents
In order to reveal the role of tenure, education, sector operated and previous work type in explaining the income differential among female employers, a specification of below
School sites and clubs may not register or own their own domain names or host school-related.. District-related Web sites are hosted on District Web servers. Only with
Not Christian or Jesus but Zions' Watchtower.. Interestingly also the Ancient Hebrews. used the black cube as a symbol for their God "Saturn"
No attempts on milkfish culture have been made in semi-arid areas where plenty of high salinity (up to 30 ppt) inland saline groundwater is available. Since the effects of
According to NIST, “Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g.,
[r]
[r]
This article describes the use of an additive diagnostic wax-up that is transferred to the mouth by means of an intraoral mock-up (aesthetic pre-evaluative temporary) with