Hong Kong Institute of Vocational Education (Tsing Yi)
Department of Multimedia and Internet Technology
Higher Diploma in
Multimedia and lnternet Applications
(41381)
Final Year Project Report
Apply Multi-Biometrics Recognition Systems for
Intelligent House Management
By
Chan Ka Lun, Peae
Tsang Man Piu
ABSTRACT
This final year project describes the design and development of applying the
biometrics technology with facial recognition and fingerprint recognition system.
Several commonly used applications for our biometric system are reviewed in this
report.
Details of the design criteria of both hardware and software principles of operation as
well as the testing and verification of the system are presented. Further development
of project is also proposed and recommended.
This project is to develop and built up a biometrics system for intelligent house and
clubhouse. As biometrics is a popular and safety technology, the project applies this
technology to improve the security level and easy for management.
TABLE OF CONTENTS
page
ABSTRACT
i
TABLE OF CONTENTS
ii
LIST OF FIGURES
v
LIST OF TABLES
viii
LIST OF APPENDICES
ix
Chapter 1
Introduction
1
1.1 Overview
1
1.2 Background
Information
1
1.3 Structure of the Final Year Project Report
1
Chapter 2
Literature Review
3
2.1 Introduction
3
2.2 Introduction to Biometrics Technologies
3
2.2.1 What is Biometrics?
3
2.2.2 History of Biometrics
3
2.2.3 How does it work?
4
2.2.4 Applications in Biometrics
6
2.2.5 Template size of each Biometrics Technology
7
2.3 Examples
of
biometrics system in my life
7
2.4 Examples
of
biometrics system layout
8
2.5 Examples of hardware design
10
2.6 Examples of software interface design
11
2.7 Summary
12
Chapter 3
Development Methodology for
Chapter 4
Details of the Multi-Biometrics Recognition
System
20
4.1 Overview
20
4.2 Workflow of Recognition System
21
4.3 Function of Recognition System
22
4.3.1 Function of Administration tools
22
4.3.2 Function of Building security system
23
4.3.3 Function of Clubhouse system
23
4.4 Hardware of Recognition System
24
4.5 Development Software use
25
4.6 Software needs and setup
26
4.7 Database
Structure
28
4.7.1 Relational between tables
28
4.7.2 Householder
29
4.7.3 Householder Log
29
4.7.4 Visitor
30
4.7.5 Building
30
4.7.6 Floor and Flat
31
4.7.7 Clubhouse
31
4.8 Graphics Design and Layout
32
4.8.1 Administration Tools layout design
32
4.8.2 Building security system layout design
34
4.8.3 Clubhouse system layout design
35
Chapter 5
Evaluation of Multi-Biometrics Recognition
Systems
38
5.1 Overview
38
5.2 Principle of Biometric Enrolment and Verification
38
5.3 Summary
38
Chapter 6
Application Procedure of Multi-Biometrics
Recognition Systems
39
6.1 Administration
tools
39
6.1.1 Add new householder
39
6.1.2 Edit householder
43
6.1.3 Delete householder
45
6.1.4 Householder entry log
46
6.2.1 Householder mode
49
6.2.2 Visitor mode
51
6.3 Clubhouse
system
54
6.3.1 Clubhouse login and logout system
54
6.3.2 Clubhouse payroll system
57
Chapter 7
Verification of the Multi-Biometrics
Recognition Systems
59
7.1 Overview
59
7.2 Verification of Result
59
7.3 Summary
59
Chapter 8
Conclusion and Further Development
60
8.1 Overview
60
8.2 Contribution of Final Year Project
60
8.3 Discussion on the Project Limitation
60
8.4 Further
Proposal
61
References 62
Appendices 64
Appendix A:
Team member workload
64
Appendix B:
Project plan
65
LIST OF FIGURES
page
Fig. 2.1
Biometric identification and encrypted data system
8
Fig. 2.2
Biometric access control system (Exys Security system)
8
Fig. 2.3
Country entry and exit control system
8
Fig. 2.4
Hand geometry control system
9
Fig. 2.5
Biometric experiment system
9
Fig. 2.6
Presse Fotos ekey fingerprint system
10
Fig. 2.7
Biometric reader clocking system
10
Fig. 2.8
Office access control system
10
Fig. 2.9
Windows lcqon recognition system
11
Fig. 2.10 Breaker facial searching system
11
Fig. 2.11 Biometric Patient Tracking System
11
Fig. 2.12 fingerID system with biometrics in USA
11
Fig. 3.1
Types of fingerprint
13
Fig. 3.2
Optical Fingerprint Sensors
14
Fig. 3.3
Surface Pressure Sensor
14
Fig. 3.4
Capacitive Sensors
14
Fig. 3.5
Facial geometry example
15
Fig. 3.6
Correct recognition example
15
Fig. 3.7
Facial recognition in airport
16
Fig. 3.8
First Visitor mode layout
17
Fig. 3.9
Second Visitor mode layout
18
Fig. 3.10 Clubhouse mode layout
18
Fig. 3.11 Database schema of Biometrics System
19
Fig. 4.1
Structure of System
20
Fig. 4.2
Workflow of Building security system
21
Fig. 4.3
Workflow of Clubhouse system
22
Fig. 4.4
Marcomedia Flash
25
Fig. 4.5
Adobe Photoshop
25
Fig. 4.6
Visual Basic 6.0
25
Fig. 4.7
Create MySQL user
26
Fig. 4.8
Restore the backup file
27
Fig. 4.9
Permission of the folder
27
Fig. 4.10 Folder of householder and visitor
28
Fig. 4.12 Main page of Administration Tools
32
Fig. 4.13 Database Management of Householder
32
Fig. 4.14 Entry Log of Householder
33
Fig. 4.15 Entry Log of Visitor
33
Fig. 4.16 Selection mode of building security system
34
Fig. 4.17 Householder mode of building security system
34
Fig. 4.18 Visitor mode of building security system
35
Fig. 4.19 Language Selection mode of clubhouse system
35
Fig. 4.20 Selection mode of clubhouse system
36
Fig. 4.21 Login mode of clubhouse system
36
Fig. 4.22 Choose facilities mode of clubhouse system
37
Fig. 4.23 Logout mode of clubhouse system
37
Fig. 6.1
Select “Database Management”
39
Fig. 6.2
Click the “Add New” button
39
Fig. 6.3
“Add user” windows
40
Fig. 6.4
Procedure of face enrollment
40
Fig. 6.5
Successful message of face enrollment
41
Fig. 6.6
Successful message of add new householder
41
Fig. 6.7
Error message of add new householder
42
Fig. 6.8
New householder in the list
42
Fig. 6.9
Click the “Edit” button
43
Fig. 6.10 Enroll new face
43
Fig. 6.11 Successful message of face enrollment
44
Fig. 6.12 Successful message of update householder
44
Fig. 6.13 Delete the householder
45
Fig. 6.14 Confirm to delete householder
45
Fig. 6.15 Select “Entry Log” of householder
46
Fig. 6.16 Query of Householder Entry Log
46
Fig. 6.17 Result of Householder Entry Log
47
Fig. 6.18 Select “Entry Log” of visitor
47
Fig. 6.19 Query of Visitor Entry Log
48
Fig. 6.27 Error message of enter wrong floor
52
Fig. 6.28 Procedure of face capture
52
Fig. 6.29 Procedure of fingerprint capture
53
Fig. 6.30 Visitor register complete
53
Fig. 6.31 Step 1 of process clubhouse system
54
Fig. 6.32 Step 2 of process clubhouse system
54
Fig. 6.33 Step 3 of process clubhouse system
55
Fig. 6.34 Step 4 of process clubhouse system
55
Fig. 6.35 Step 5 of process clubhouse system
56
Fig. 6.36 Step 6 of process clubhouse system
56
Fig. 6.37 Step 1 of process clubhouse payroll system
57
Fig. 6.38 Step 2 of process of clubhouse payroll system
57
Fig. 6.39 Step 3 of process of clubhouse payroll system
58
LIST OF TABLES
page
Table 2.1
Template size of each Biometrics Technology
7
Table 4.1
Database structure of householder 29
Table 4.2
Database structure of householder log
29
Table 4.3
Database structure of visitor
30
Table 4.4
Database structure of building
30
Table 4.5
Database structure of floor and flat
31
Table 4.6
Database structure of clubhouse
31
Table 7.1
FRR rate of facial recognition
59
LIST OF APPENDICES
page
Appendix A
Team member workload
64
Appendix B
Project plan
65
Chapter 1 Introduction
1.1 Overview
Nowadays, Biometrics becomes important in our life. Since it has a high security and
convenient, so that people use Biometrics technology on anything. Such as, door
access control, border control, banking, identify people, intelligent house, etc. The
application is very diverse and their capacity of development is very large.
The intelligent house becomes popular for the past few years. It can provide a safety
and comfortable to the householder. But the security is very important, it must be
identify the house holder accurately and prevent the system to make a mistake for
identification. So that, we need to build a system like the security to make a identity
and monitoring the security of building.
1.2 Background
Information
In fact, Hong Kong building security is decreased. The thief is increased to make the
people safety to be damaged. So, we must improve the building security and the
management. By the way, when we come back to our building, we may use words of
password or the key to open the building door. That is so trouble and inconvenience.
Biometrics technologies can help us to improve the security and easy to management.
So, we may use the biometrics technologies to maintain our final year project.
1.3 Structure of the Final Year Project Report
The remainder of this report is divided into Seven Chapters. They are as follows:
-
Chapter 2 covers the literature review on the design
research of biometrics system.
We find a lot of the information and image from Internet.
Chapter 3 discusses on the design criteria
of hardware system, software, layout and
database
Chapter 8 concludes the report and out lines the contributions of the project. The
limitations were highlighted and suggestions are made for further development to
improve the system.
Chapter 2 Literature Review
2.1 Introduction
That part is literature review. It means we will show you all our research before our
project starting. And the research should be about example of biometric system,
layout of the hardware system, layout of the software interface, etc. We will show you
all of our research for the final year project.
2.2 Introduction to Biometrics Technologies
2.2.1
What is Biometrics?
The term biometrics refers to the emerging field of technology devoted to the
identification of individuals using biological traits or behaviours
[1]
. In practice, this
means capturing an image of a unique feature of an individual such as a fingerprint,
hand, eye or face, and comparing it with a template captured previously. For ease of
explanation this has been over-simplified, but in essence this is biometric technology
works.
Human Recognition Systems works with 4 key biometric technologies:
z
Iris Recognition
zHand Recognition
zFingerprint Recognition
zFacial Recognition
2.2.2 History
of Biometrics
1800s identification largely relied upon "photographic memory"
[2]
. This was changed
in 1883 when Alphonse Bertillon, a clerk in the Paris police prefecture, introduced
physical measurement system (which came to bear his name: bertillonage) Bertillon
based his system on the claim that measurement of adult bones does not change
throughout life. Measurements in his system included: height, length, and breadth of
the head, the length of different fingers, the length of forearms, etc (Bertillon
estimated that the odds of duplicate records were 286,435,456 to 1 if 14 traits were
the Chinese for years. However the idea of biometrics as a field of study with useful
identification applications, was there and interest in it has grown.
Personal Identification Numbers (PINs) were one of the first methods used for
identification. There are also methods that involve passwords and physical tokens e.g.
smart cards. There are a number of problems associated with this kind of
identification. People forget passwords, lose tokens, reuse passwords, write them
down, tokens can get stolen. The recognition of the above does not mean the
identification of the person providing it - they could be presented by anybody. With the
advent of e-commerce brings increased pressure on IT managers to provide partners
and customers with means of identification to access corporate networks. This results
in a deluge of passwords and means of access, which are often forgotten, misused or
lost. With the increased population accessing these networks the risk of attacks on
the networks is increased. Companies are turning to Biometric Systems to bring
tighter security to their computer networks.
Today we have the technology to realize the aims, and to refine the accuracy of
biometric identification, and therefore the possibility of making it a viable field. Soon
biogenetics technology will be used in every house hold and it is getting increasingly
more and safer to use biometric technologies in order to better our life.
2.2.3
How does it work?
False Reject Rates:
For most applications, letting the good guys in is just as important as keeping the bad
guys out
[3]
. The probability that a biometric device won't recognize a good guy is
called the "False Reject Rate."
The False Reject Rates quoted for current biometric systems range from 0.00066% to
1.0%.
A low False Reject Rate is very important for most applications, since users will
become extremely frustrated if they're denied access by a device that has previously
recognized them.
There has a example may be helpful.
A company with 100 employees has a biometric device at its front door. Each
employee uses the door four times a day, yielding 400 transactions per day.
A False Reject Rate of 1.0% predicts that every day, four good guys (1% of 400) will
be denied access. Over a five-day week, that means 20 problems. Reducing the
False Reject Rate to 0.1% results in just two problems per week.
A low False Reject Rate is very important for most applications, since users will
become extremely frustrated if they're denied access by a device that has previously
recognized them. As mentioned previously, the combination of a low False Reject
Rate plus a simple keypad code provides virtually unbreakable security.
Equal Error Rates:
Error curves give a graphical representation of a biometric device's "personality." The
point where false accept and false reject curves cross is called the "Equal Error
Rate." The Equal Error Rate provides a good indicator of the unit's performance. The
smaller the Equal Error Rate, the better.
Validity of Test Data:
Testing biometrics is difficult, because of the extremely low error rates involved. To
attain any confidence in the statistical results, thousands of transactions must be
examined.
Some error rates cited by manufacturers are based on theoretical calculations. Other
rates are obtained from actual field testing. Field data are usually more reliable. In the
case of False Reject rates, only field test data can be considered accurate, since
biometric devices require human interaction. For example, if the device is hard to use,
false reject rates will tend to rise. A change in the user's biometric profile could also
cause a false reject (a finger is missing, for example).
Currently, most field test error rates have been generated by various biometric
manufacturers using end-user data. Tests have also been conducted by independent
laboratories such as the U.S. Department of Energy's Sandia National Laboratories.
The most recent test released by Sandia was performed in 1991.
It's important to remember that error rates are statistical: they are derived from a
series of transactions by a population of users. In general, the larger the population
and the greater the number of transactions, the greater the confidence level in the
accuracy of the results.
If the error rate is reported at 1:100,000, and only 100 transactions were included in
the study, the confidence level in the results should be very low. If the same error rate
was reported for 1 million transactions, the confidence level would be much higher.
The magnitude of the reported results affects the size of the sample required for a
reasonable confidence level. If the reported error rate is 1:10, then a sample of 100
transactions may provide a sufficient confidence level. Conversely, a 100-transaction
sample would be too small if the error rate was reported as 1:100,000.
2.2.4
Applications in Biometrics
There are 9 biometrics applications:
[4]
z
Physical Access Control
zLogical Access Control
zJustice/Law Enforcement
zTime and Attendance
zBorder Control/Airports
zHIPAA
z
Financial/Transactional
zIntegrators/Resellers
zSafes, Door Locks
2.2.5
Template size of each Biometrics Technology
Biometrics Technology
Template size per record
Iris 256
Bytes
Fingerprint 512-1000
Bytes
Facial >512
Bytes
Hand Geometry
9 Bytes
Table 2.1 Template size of each Biometrics Technology
2.3 Examples of biometrics system in my life
Law Enforcement
The law enforcement community is perhaps the largest biometrics user group.
Police forces thought the world use AFIS technology to process criminal
suspect, match finger images and bring guilty criminals to justices. A number
of biometrics vendors are earning significant revenues in this area.
Banking
Bank has been evaluating a range of biometrics technologies for many years.
Automated Teller Machines (ATMs) and transaction at the point of scale are
particularly vulnerable to fraud and can be secured by biometrics. Other
emerging markets such as telephone banking and internet bank must also be
totally secure for bankers alike.
2.4 Examples of biometrics system layout
We researched that the following figures are the examples of the biometrics system.
Fig. 2.1 Biometric identification and encrypted data system [5]
Fig. 2.2 Biometric access control system (Exys Security system) [6]
Fig. 2.4 Hand geometry control system [8]
2.5 Examples of hardware design
We may show you our research of hardware. The following figures are below.
Fig. 2.6 Presse Fotos ekey fingerprint system [10]
Fig. 2.7 Biometric reader clocking system [11]
2.6 Examples of software interface design
The following figures are our research of the biometrics software interface examples.
Fig. 2.9 Windows lcqon recognition system [13]
Fig. 2.10 Breaker facial searching system [14]
2.7 Summary
After the research that, we find many about the information of biometrics and many
different kinds of the biometrics system. In fact, there were many technologies were
used the biometrics technology. It is the truth and it must be more popular in the
future. Now a day, many old systems are displaced by the biometric system. For
example: access control system, payroll system, banking system, etc.
During the project development, the biometric hardware is used. There are TiFace
system, U are U fingerprint system. TiFace system enables to capture and enrol
user’s face. U are U fingerprint system is use to capture and enrol user’s fingerprint.
So, we have to use the biometric in the future life.
Chapter 3 Development Methodology for Multi-Biometrics
Recognition System
3.1 Introduction
In this part, we will tell you about our first development methodology. What kinds of
hardware did we use. Why we use that hardware. What kinds of software did we use.
Why we use that software. And we also post our first layout design in that part. We will
all tell you the answer
3.2 Design Consideration of Hardware System
Fingerprint recognition represents the oldest method of biometric identification. Its
history is going back as far as at least 2200 BC. The use of fingerprints as a personal
code has a long tradition and was already used by the Assyrians, the Babylonians,
the Chinese and the Japanese. Since 1897, dactyloscopy (synonym for
non-computer-based fingerprint identification) has been used for criminal
identification. A fingerprint consists of ridges (lines across fingerprints) and valleys
(spaces between ridges). The pattern of the ridges and valleys is unique for each
individual.
[17]
There are two major methods of fingerprint matching: Minutiae matching and global
pattern matching. The first approach analyses ridge bifurcations and endings, the
second method represents a more macroscopic approach. The last approach
considers the flow of ridges in terms of, for example, arches, loops and whorls. As the
equal-error-rate is low, therefore fingerprint recognition is very accurate. The prices of
such systems compared to other biometric systems are quite low and the user
acceptance is very high. The strength of fingerprint identification is, that it can be
deployed in a varied range of environments.
There are 6 types of sensors for fingerprint recognition:
z
Optical Fingerprint Sensors
z
Themalelectric
Sensors
z
Capacitive
Sensors
z
E-Field
Sensors
z
Touchless
Sensors
z
Surface Pressure Sensor
Fig. 3.2 Optical Fingerprint Sensors [19] Fig. 3.3 Surface Pressure Sensor
[20]
Fig. 3.4 Capacitive Sensors [21]
The template size varies from 100 bytes to 1500 Bytes depending on the algorithm
and the quality of a fingerprint. Nevertheless, very rarely there are fingerprints without
any minutiae-points that leads to a failure to enroll (FER = Failure to Enroll Rate). It is
also difficult to extract the minutiae points accurately when the fingerprint has got a
low quality.
Introduction of facial recognition
Facial recognition systems are built on computer programs that analyze images of
human faces for the purpose of identifying them. The programs take a facial image,
measure characteristics such as the distance between the eyes, the length of the
nose, and the angle of the jaw, and create a unique file called a "template." Using
templates, the software then compares that image with another image and produces
a score that measures how similar the images are to each other. Typical sources of
images for use in facial recognition include video camera signals and pre-existing
photos such as those in driver's license databases.
[22]
Computers can do increasingly amazing things, but they are not magic. If human
beings often can't identify the subject of a photograph, why should computers be able
to do it any more reliably? The human brain is highly adapted for recognizing faces -
infants, for example, remember faces better than other patterns, and prefer to look at
them over other patterns. The human brain is also far better than computers at
compensating for changes in lighting and angle. The fact is that faces are highly
complex patterns that often differ in only subtle ways, and that it can be impossible for
man or machine to match images when there are differences in lighting, camera, or
camera angle, let alone changes in the appearance of the face itself.
All of this makes face recognition ideal for high traffic areas open to the general public,
such as:
z
Airports and railway stations
z
Casinos
zCashpoints
zStadiums
zPublic transportation
zFinancial institutions
zGovernment offices
z
Businesses of all kinds
3.3 Design Consideration of Software
We choose macromedia flash and adobe Photoshop for our design software.
Why we use that two software for design development?
It is because macromedia flash is so powerful. It can be used actionscript for many
different of animation. Although, it is easy to use and popular in the design area.
The second point is we don’t want to have a static and boring interface. So, we
decided to use flash animation to replace of static picture interface. It can attract the
people to use our system and make the system more interest.
In the internet, many people used that two software. It is the brand name power and
that software is really good for design.
On the other hand, Photoshop can help us for tuning the photo color, light, size, effect,
etc. It also can help us to make the picture be good.
3.4 Graphics Design and Layout
Fig. 3.9 Second Visitor mode layout
Fig. 3.10 Clubhouse mode layout
.
3.5 Structure of Database Design
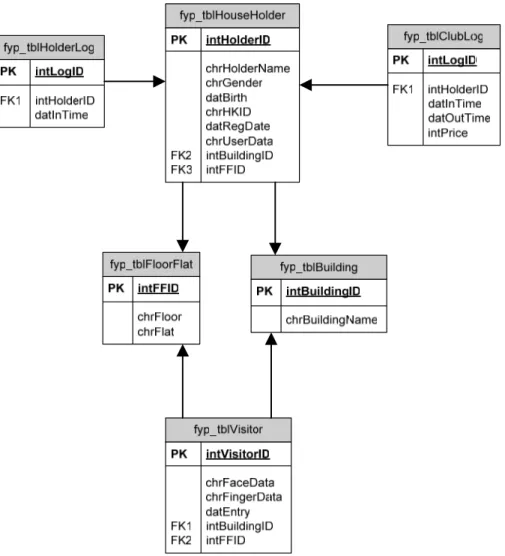
The following Fig. 3.11 is our first development of database structure design.
It only consists of 4 tables: tblHouseHolder, tblBuilding, tblVisitoryymmdd and
tblFloorFlat. That is our first developed schema.
Chapter 4 Details of the Multi-Biometrics Recognition System
4.1 Overview
In this part, we finished to discuss and develop all the kinds of tool should we use. We
will use two hardware for the system. It should be Face recognition and fingerprint
hardware. And we will tell you the function of our biometric system. It has three
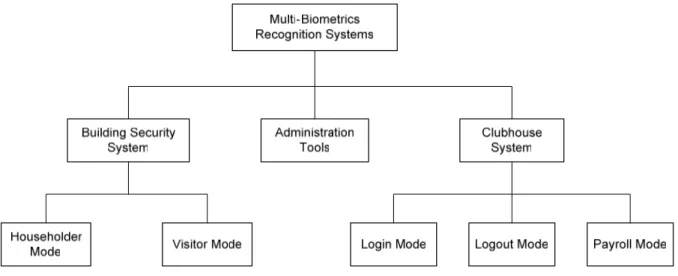
different parts of the recognition system, please refer to Fig. 4.1.
Finally, we choose the software, hardware and the final layout. We will show you all
the things in the following.
4.2 Workflow
of
Recognition System
The following two figures 4.2 & 4.3 are our workflow of the building security system
and clubhouse system.
Entry
Select Mode
Facial Recognition
Check database & identify
Open door
Input Floor and Flat Enroll Face Enroll Fingerprint Open door Visitor Vaild Invaild Householder
Entry
Select Login/Logout
Login mode
Store login time to database
Facial
recognize
Check
database
InvaildLogout mode
Facial
recognize
Check
database
Store logout time to database Invaild Login Logout vaild vaild
Fig. 4.3 Workflow of Clubhouse system
4.3 Function of Recognition System
There are three parts of our recognition system. It consists of Administration Tools,
Building security system and Clubhouse system.
4.3.1 Function
of
Administration Tools
Actually, householder and visitor also need to enroll fast when they want to use the
biometric system. We make an enrolment to analysis this problem. Householder can
come to our office to use the householder enrolment system.
They only need to put their face in front of the camera. Their face record will store to
our database for verify used. They also need to type their information (e.g. name,
gender, and floor no., flat no., etc.) to our database used. It is used for comparison.
4.3.2
Function of Building security system
We design that householder mode is for householder using. They are no need to
remember the word of password for house entry. It is because the entry password
always changed a time. The householder may forget the password or remember the
wrong one.
So, Householder mode system can help person easily for entry. They only put their
face in front of camera. If they are our householders then the door will open
automatically by our system.
Nowadays, people visit to their friend house. They must write down their personal
information (e.g. name, id, gender, visit reason, visit room no.) in the building entry
control. It is because the building needs to protect their householder safety and giving
record. It may make the visitor inconvenient.
So, we make a visitor mode for visitor using. It can help visitor more convenient,
Visitor only put their face in front of camera and fingerprint to record their personal
data. That should be fast and more convenient than the paper record.
4.3.3
Function of Clubhouse system
Clubhouse is to be more popular to the new building. Householders can use their own
clubhouse facilities. When they used the clubhouse facilities, they need to make a
paper rent. That is not convenient and trouble.
So, we make a clubhouse biometric system for householder using. They only open
our system and put their face in front of the camera. Our system will record their login
time. Otherwise, when they want to logout and leave that they also use our system to
record their logout time. They can use our clubhouse easily.
4.4 Hardware of Recognition System
We choose facial recognition and fingerprint for our system used Facial recognition
systems are computer-based security systems that are able to automatically detect
and identify human faces. These systems depend on a recognition algorithm. The
first step for a facial recognition system is to recognize a human face and extract it fro
the rest of the scene. Next, the system measures nodal points on the face, such as
the distance between the eyes, the shape of the cheekbones and other
distinguishable features. Facial recognition is a good biometric system and it is too
convenience and user-friendly. So that, we use facial recognition for our system used.
For the fingerprint reason, we found that following good points:
z
More securable than passwords by intercepting use and approach of
Unauthorized people whose identification is not registered.
z
Free from inconvenience to upgrade and remember passwords and the company
z
It can save much cost to manage passwords.
z
Fast and exact perception with high technology of finger print identification.
z
Adopted dsp system that is to calculate moving direction and distance without
Password by the image perceiving sensor.
z
No roller and soft movement thanks to less rubbing resistance.
z
Finally, fingerprint is easy too use, user-friendly and too cheap in the kinds of
biometrics devices.
4.5 Development Software use
Macromedia Flash
Fig. 4.4 Marcomedia Flash [26]
Adobe Photoshop
Fig. 4.5 Adobe Photoshop [27]
These two design tools are very powerful and easy to use. It can help us to analysis
all the design problems. And we can make many different effects by that two software.
It is very popular and great. So that, we used the tools for our interface layout design.
Programming tools
Fig. 4.6 Visual Basic 6.0 [28]
4.6 Software needs and setup
The basic software needs to install of the system are below:
z
Flash Player 8.0
z
TiFace
Runtime
z
TiFace SmartGate SDK
z
Futronic Fingerprint SDK
The server and driver of the system needs are below:
z
MySQL Server 4.0.x
z
MySQL ODBC 3.51 Driver
For easy to manage the database, we suggest to install these software are below:
z
MySQL
Administrator
z
MySQL
Query
Browser
Now, I will show you how to create new database account and restore the table in
database form sql backup file.
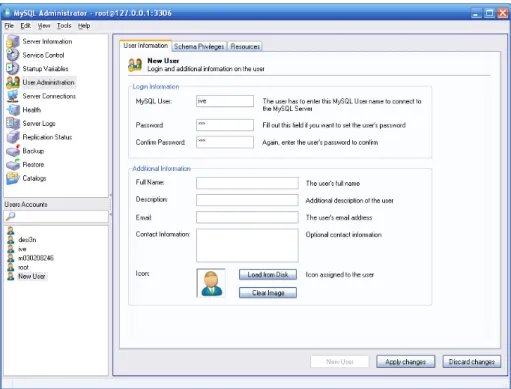
Step1. Use MySQL Administrator to create a new account. The MySQL user and
password also is “ive”. Then, click “Apply changes”. The user will be created.
Step2. Open the sql backup file to restore the table needs in the database. It will
create the schema “ive_fyp” automatically.
Fig. 4.8 Restore the backup file
Next, I will show how to share the folder. This folder is used to store householder and
visitor’s template and photo.
Step1. Create a folder “userdata” in your any local drive. E.g.: C drive.
Step2. Share this folder and set the permission of Everyone to Full control.
Step3. Create two folders “householder” and “visitor” in the “userdata” folder.
Fig. 4.10 Folder of householder and visitor
Then, I will show you how to change the server ip of the system connect.
Step1. Open the “config.ini” file in the same level of folder.
Step2. Modify the IP and enter the correct server IP. For example, you MySQL
server’s IP is 192.168.0.1. So, you should enter the “serverIP=192.168.0.1”.
And the template file and photo also store in this server. Important: If your
MySQL server is setup on localhost, you must enter “127.0.0.1”.
4.7 Database
structure
4.7.2 Householder
Table: fyp_tblHouseHolder
Description: Store the detail of householder
Key Field Name
Data Type
Description
9
intHolderID INT(5)
HouseHolder’s
ID
chrHolderName
VARCHAR(255)
HouseHolder’s
Name
chrGender
CHAR(1)
HouseHolder’s
Gender
datBirth
DATE
HouseHolder
Birthday
chrHKID
VARCHAR(11)
HouseHolder’s HKID Number
datRegDate DATE
Register
Date
chrUserData VARCHAR(64)
Template Filename of Face Enroll
intBuildingID INT(2)
Building
ID
intFFID
INT(3)
Floor and Flat ID
Table 4.1 Database structure of householder
4.7.3 Householder
Log
Table: fyp_tblHolderLog
Description: Store the log of householder login
Key Field Name
Data Type
Description
9
intLogID INT(8) Log
ID
intHolderID INT(5)
Householder’s
ID
datInTime
DATETIME
Login Date and Time
Table 4.2 Database structure of householder log
4.7.4 Visitor
Table: fyp_tblVisitor
Description: Store the detail and log of visitor
Key Field Name
Data Type
Description
9
intVisitorID INT(8)
Visitor’s
ID
chrFaceData VARCHAR(64)
Template Filename of Face Enroll
chrFingerData
VARCHAR(64)
Template Filename of Fingerprint
Enroll
datEntry
DATETIME
Entry Date and Time
intBuildingID INT(2)
Building ID of Visitor visit
intFFID
INT(3)
Floor and Flat ID of Visitor visit
Table 4.3 Database structure of visitor
4.7.5 Building
Table: fyp_tblBuilding
Description: Store the name of building
Key Field Name
Data Type
Description
9
intBuildingID INT(2)
Building
ID
chrBuildingName
VARCHAR(255)
Building
Name
Table 4.4 Database structure of building
4.7.6
Floor and Flat
Table: fyp_tblFloorFlat
Description: Store the floor and flat
Key Field Name
Data Type
Description
9
intFFID
INT(3)
Floor and Flat ID
chrFloor
CHAR(2)
Floor
Number
chrFlat
CHAR(1)
Flat
Character
Table 4.5 Database structure of floor and flat
4.7.7 Clubhouse
Table: fyp_tblClubLog
Description: Store the log of householder using clubhouse
Key Field Name
Data Type
Description
9
intLogID INT
Log
ID
intHolderID INT(5)
Householder’s
ID
datInTime
DATETIME
Login Date and Time
datOutTime
DATETIME
Logout Date and Time
intPrice
INT(5)
Price of using clubhouse
Table 4.6 Database structure of clubhouse
4.8 Graphics Design and Layout
4.8.1 Administration
Tools layout design
Fig. 4.12 Main page of Administration Tools
1. Menu
bar
Fig. 4.13 Database Management of Householder
1. Query
search
2. List of the householder
3. Add new householder
4. Edit selected householder
Fig. 4.14 Entry Log of Householder
1. List of entry log
2. Query search
4.8.2
Building security system layout design
Fig. 4.16 Selection mode of building security system
1. Date and Time
2. Mode selection button
Fig. 4.17 Householder mode of building security system
1. Date and Time
2. Camera box
3. Message
box
4. Exit
button
Fig. 4.18 Visitor mode of building security system
1. Date and Time
2. Display of floor and flat
3. Message box
4. Number and character keypad
5. Exit
button
Fig. 4.20 Selection mode of clubhouse system
1. Mode selection button
Fig. 4.21 Login mode of clubhouse system
1. Camera box
2. Message box
3. Login
button
Fig. 4.22 Choose facilities mode of clubhouse system
1. Camera box
2. Message box
3. Login button
4. Facilities button
Chapter 5 Evaluation of Multi-Biometrics Recognition Systems
5.1 Overview
We would like to tell you our biometric system. It’s all of good points in the popular
area. And we also have any short points for future improvement.
5.2 Principle of Biometric Enrolment and Verification
For the good side, people no need to remember the word of password for entry to
their building. They no need to use any key or find other people to help them open the
door. Our biometric system can easy to help people only put their face in front of the
camera for open the door. It seen that it is very convenience, comfortable and
user-friendly to our customer.
For the bad side, when a householder sometime wears glasses, sometime not wear
glasses. Our facial recognition system may verify failed for their glasses or cap.
It is because our system is followed the capture face data to compare the person’s
face. If the person wear glasses or cap, it may verify failed.
On the other hand, if the area has not enough light. It also may distort the verify %.
It is because if the area has not enough light, then the camera can not capture the
face data fully and immediately.
5.3 Summary
In fact, all of the technology also has good and bad points. Facial recognition system
also has that two points. But Biometric system really can help people to make the
world convenience and more easy.
So that, biometric system also can help human to analysis many problems. We may
improve the biometric technology as soon as possible. It is because it may be the
future one of the main technology.
Chapter 6 Application Procedure of Multi-Biometrics Recognition
Systems
6.1 Administration
Tools
6.1.1 Add new householder
Step1. Select “Householder” -> “Database Management” in menu bar.
Fig. 6.1 Select “Database Management”
Step3. The “Add user” windows will appear. Enter the detail of householder.
Fig. 6.3 “Add user” windows
Step4. Click the “Start” button to open the camera and click “Enroll” button to make a
face enrollment.
Step5. The successful message will be appear when the face enrollment success.
Fig. 6.5 Successful message of face enrollment
Step6. Click the “Save” button after enroll the face and enter the detail. The tools will
add new householder in database and show the successful message.
Step7. If you do not enroll the face before click the “Save” button, the tools will show
the error message and tell you enroll the face.
Fig. 6.7 Error message of add new householder
Step8. The tools will show you the new householder in the list.
6.1.2 Edit
householder
Step1. Select the householder you want to edit in the list, and then click “Edit”
button.
Fig. 6.9 Click the “Edit” button
Step2. Click the “Start” button to open the camera and click “Enroll” button to make
a new face enrollment.
Step3. The successful message will be appear when the face enrollment success.
Fig. 6.11 Successful message of face enrollment
Step4. Click the “Save” button after enroll the face and modify the detail. The tools
will update householder in database and show the successful message.
6.1.3 Delete
householder
Step1. Select the householder in the list and click “Delete” button.
Fig. 6.13 Delete the householder
6.1.4
Householder entry log
Step1. Select “Householder” -> “Entry Log” in menu bar.
Fig. 6.15 Select “Entry Log” of householder
Step2. Enter the householder ID or name and select the range of date to search the
log.
Step3. The tools will show the result.
Fig. 6.17 Result of Householder Entry Log
6.1.5
Visitor entry log
Step2. Select the date and building
Fig. 6.19 Query of Visitor Entry Log
Step3. You can select the visitor in the list and it will show the photo of visitor.
6.2 Building Security System
6.2.1 Householder
Mode
Step1. Press the Householder button.
Fig. 6.21 Mode selection of Building Security System
Step2. The systems will identify after 3 seconds automatically. No needs enter any
button.
Step3. If the systems cannot identify you, it will show the error message and identify
after 3 seconds again.
Fig. 6.23 Error message when cannot identify the householder
Step4. If success to identify, the systems will show your name and show you the
success message. The door will be open.
6.2.2 Visitor
Mode
Step1. Press the Visitor button.
Fig. 6.25 Mode selection of Building Security System
Step2. Enter the floor and flat you want to go. Then, press the Enter button. Also,
you can the Clear button when you enter wrong floor and flat.
Step3. Our floor range is 1 to 15. If you enter large than 15, you will get the error
message and enter the correct floor.
Fig. 6.27 Error message of enter wrong floor
Step4. Press the button to capture your face when you are ready in front of the
camera. After press the button, the systems will countdown 3 seconds to
capture automatically.
Step5. Put your any finger on the fingerprint device to capture your finger. It needs to
capture 3 times.
Fig. 6.29 Procedure of fingerprint capture
Step6. After face and fingerprint capture, the systems will save your data in
database and open the door.
6.3 Clubhouse
system
6.3.1
Process of clubhouse login and logout system
Step1. You can see the selection page. When you want to login clubhouse, you
can press the “
登入
” button
Fig. 6.31 Step 1 of process clubhouse system
Step2. The login page is opened. You can see the monitor and message. In this
moment, you need to put your face in front of the camera.
Step3. When you are our householder, our database will find your face data. The
system will let you pass the login process and click the login button for
verifies.
Fig. 6.33 Step 3 of process clubhouse system
Step5. When you want to leave our clubhouse, you must logout our system. It is as
same as login part. You also put on your face in front of the camera. Our
database will record your logout time automatically.
Fig. 6.35 Step 5 of process clubhouse system
Step6. When you logout successful, our database should store your logout time
record.
6.3.2
Process of clubhouse payroll system
Step1. When you pay the clubhouse free, you may go to our clubhouse payroll
system.
Fig. 6.37 Step 1 of process clubhouse payroll system
Step2. You also put your face in front of our camera. Our database will search your
login and logout time for calculates the price for clubhouse payment.
Step3. When you pay the money to our staff, our database should store your
payment record.
Chapter 7 Verification of the Multi-Biometrics Recognition
Systems
7.1 Overview
In this part, we would like to represent our system’s verification result of facial
recognition. We will test it 20 times to get the result of its FAR and FRR. It cans test
the reliable and accuracy of the system.
7.2 Verification of Result
FAR and FRR of Facial recognition:
No. of correct
acceptance (a)
No. of false rejection
(b)
False Rejection Rate (FRR)
b / (a + b)
15 5
0.25
Table 7.1 FRR rate of facial recognition
No. of correct rejection
(a)
No. of false
acceptance (b)
False Acceptance Rate (FAR)
b / (a + b)
20 0
0
Table 7.2 FAR rate of facial recognition
7.3 Summary
To summarize, the FRR of facial recognition is a little bit high. It is 0.25%. Sometimes,
it cannot verify properly. It is because the light, glasses, cap may affect the system to
verify. Although the FRR is a little bit high, the FAR is 0. It shows that the system have
a high reliable. And the system have a high accuracy to verify the user.
Chapter 8 Conclusions and Further Development
8.1 Overview
Base on the important of biometrics technology, it is popular and user-friendly to
displace many older technologies and systems in the future technology development.
8.2 Contribution
of
Final Year Project
The achievements and contributions of this project can be summarizes as follows:-
We are developed the three parts of the recognition system. There are Administration
Tools, Building Security System and Clubhouse System. It is ready to apply in the
building. This recognition is convenience and safety for security management. We
also need to improve our technology, security and method for biometrics system built
up process and developed any great ideas.
They are no need to remember the word of password for house entry. It is because
the entry password always changed a time. The householder may forget the
password or remember the wrong one. Now, they only use their face to make an entry
and no need to bring smartcard and remember the password.
8.3 Discussion on the Project Limitation
When a person sometime wears glasses, sometime not wear glasses. Our facial
recognition system may verify failed for their glasses or cap. It is because our system
is followed the capture face data to compare the person’s face. So, the person enrolls
the face record that he has no wear any glasses or anything on his face. If the person
wears glasses or cap to verify, it may verify failed.
On the other hand, if the area has not enough light or in a dark area. It also may
distort the verify %. It may verify failed. It is because if the area has not enough light,
then the camera cannot capture the face data fully and immediately.
8.4 Further
Proposal
After this project, we have other further ideas. The further ideas are below:-
z
Administration Tools can generate the report of householder or visitor.
z
Add Chinese interface of the building security system.
z
Send the email or signal to householder when visitor come.
z
Payroll monthly statement for members.
z
Car entry and exit recognition system for car park
Use face recognition to identify the householder and open the gate
Record the entry and exit log for security
References
[1]
Introduction of Biometrics
http://www.hrsltd.com/identification_technology/biometrics.htm
[2]
History of Biometrics
http://library.thinkquest.org/TQ0313041/scrottyhistory.htm
[3]
How does it work?
http://www.findbiometrics.com/Pages/guide2.html
[4]
Applications in Biometrics
http://www.findbiometrics.com/index.html#applications
[5]
Fig. 2.1 Biometric identification and encrypted data system
http://www.pressi.com/gb/image/61510.html
[6]
Fig. 2.2 Biometric access control system (Exys Security system)
http://www.exys.co.za/resume.html
[7]
Fig. 2.3 Country entry and exit control system
http://www.komotv.com/news/story.asp?ID=17825
[8]
Fig. 2.4 Hand geometry control system
http://www.inspectech.us/Securitysolutions_biometric.cfm
[9]
Fig. 2.5 Biometric experiment system
http://www.intellisystem.it/eventi/TIMcatania2003/Tim2003.htm
[10]
Fig. 2.6 Presse Fotos ekey fingerprint system
http://www.ekey.at/presse/fotos.asp
[11]
Fig. 2.7 Biometric reader clocking system
http://www.tensor.co.uk/english/biometric-clocking-system.htm
[12]
Fig. 2.8 Office access control system
http://www.clarinetsys.com/en/kiosk.htm
[13]
Fig. 2.9 Windows lcqon recognition system
http://www.acroprint.com/acroprintstore/Solutions/biometrics-faq.aspx
[14]
Fig. 2.10 Breaker facial searching system
http://www.asia-soft.com/frs/en/projects/obraz/
[15]
Fig. 2.11 Biometric Patient Tracking System
http://www.questbiometrics.com/biometrics-timekeeper-software.html
[16]
Fig. 2.12 fingerID system with biometrics in USA
http://msnbc.msn.com/id/3999879
[17]
Introduction of fingerprint recognition
http://www.bergdata.com/downloads/Introduction%20to%20Fingerprint.pdf
[18]
Fig. 3.1 Types of fingerprint
[19]
Fig. 3.2 Optical Fingerprint Sensors
http://www.bergdata.com/downloads/Introduction%20to%20Fingerprint.pdf
[20]
Fig. 3.3 Surface Pressure Sensor
http://www.bergdata.com/downloads/Introduction%20to%20Fingerprint.pdf
[21]
Fig. 3.4 Capacitive Sensors
http://www.bergdata.com/downloads/Introduction%20to%20Fingerprint.pdf
[22] Introduction of facial recognition
http://www.findbiometrics.com/Pages/face_articles/face_2.html
http://www.c-vis.com/htd/frt.html
[23]
Fig. 3.5 Facial geometry example
http://www.c-vis.com/htd/frt.html
[24]
Fig. 3.6 Correct recognition example
http://www.c-vis.com/htd/frt.html
[25]
Fig. 3.7 Facial recognition in airport
http://www.c-vis.com/htd/frt.html
[26]
Fig. 4.1 Marcomedia Flash
http://www.adobe.com/products/flash/flashpro/
[27]
Fig. 4.2 Adobe Photoshop
http://www.adobe.com/products/photoshop/
[28]
Fig. 4.3 Visual Basic 6.0
http://msdn.microsoft.com/vbrun/
Tutorial and example of VB and MySQL
http://www.vbmysql.com
Tutorial of embedded Flash in VB6
http://www.adobe.com/devnet/flash/articles/flash_vb.pdf
http://www.vbcode.com
Appendices
Appendix A: Team member workload
Chan Ka Lun, Peae (leader)
z
Design interface of Householder mode
z
Design interface of Visitor mode
z
Design interface of enrolment mode
z
Design interface of administrator mode
z
Programming of Householder mode
z
Programming of Visitor mode
z
Programming of enrolment mode
z
Programming of administrator mode
z
Build up database system
Tsang Man Piu
z
Design interface of Clubhouse login system
z
Design interface of Clubhouse payroll system
z
Programming of Clubhouse login system
z
Programming of Clubhouse payroll system
Appendix B: Project plan
PROJECT PLAN
Course :
41381/3A
Student Name
: Chan Ka Lun, Tsang Man Piu
Project Title
: Apply Multi-Biometrics Recognition Systems for Intelligent
House Management
Project Supervisor
: Mr. MK Lam
Date
: 7 October, 2005 (Week 4)
Project Objective(s)
:
-
Developed to use human’s face and fingerprint to in place of
the words of password and key.
-
Development of Multi-Biometrics Recognition System to
instead of traditional security
Week No. 2 4 6 8 10 12 14 16 18 20 22 24 26 28 30 32 34 36 38 Survey & Research
Work flow & Database draft
design Interface draft design
Read SmartGate’s manual and SDK
Read Futronic Fingerprint SDK Database & Interface
programming Programming
Testing Project report &
presentation
Project Resources Plan
Equipment:
z
PC with development environment
z
Webcam
z
Fingerprint device
z
Touch screen
Appendix C: Programming code
z
The class module of system
CRijndael.cls
This class module is used to generate the 64 character filename of the
template.
1 Option Explicit 2
3 Private m_lOnBits(30) As Long 4 Private m_l2Power(30) As Long 5 Private m_bytOnBits(7) As Byte 6 Private m_byt2Power(7) As Byte 7
8 Private m_InCo(3) As Byte 9
10 Private m_fbsub(255) As Byte 11 Private m_rbsub(255) As Byte 12 Private m_ptab(255) As Byte 13 Private m_ltab(255) As Byte 14 Private m_ftable(255) As Long 15 Private m_rtable(255) As Long 16 Private m_rco(29) As Long 17
18 Private m_Nk As Long 19 Private m_Nb As Long 20 Private m_Nr As Long 21 Private m_fi(23) As Byte 22 Private m_ri(23) As Byte 23 Private m_fkey(119) As Long 24 Private m_rkey(119) As Long 25
26 Private Declare Sub CopyMemory Lib "kernel32" Alias "RtlMoveMemory" _ 27 (ByVal Destination As Any, ByVal Source As Any, ByVal Length As Long) 28
29 '******************************************************************************* 30 ' Class_Initialize (SUB)
31 '******************************************************************************* 32 Private Sub Class_Initialize()
33 m_InCo(0) = &HB 34 m_InCo(1) = &HD 35 m_InCo(2) = &H9 36 m_InCo(3) = &HE 37
38 ' Could have done this with a loop calculating each value, but simply 39 ' assigning the values is quicker - BITS SET FROM RIGHT
40 m_bytOnBits(0) = 1 ' 00000001 41 m_bytOnBits(1) = 3 ' 00000011 42 m_bytOnBits(2) = 7 ' 00000111 43 m_bytOnBits(3) = 15 ' 00001111 44 m_bytOnBits(4) = 31 ' 00011111 45 m_bytOnBits(5) = 63 ' 00111111 46 m_bytOnBits(6) = 127 ' 01111111 47 m_bytOnBits(7) = 255 ' 11111111 48
49 ' Could have done this with a loop calculating each value, but simply 50 ' assigning the values is quicker - POWERS OF 2
51 m_byt2Power(0) = 1 ' 00000001 52 m_byt2Power(1) = 2 ' 00000010 53 m_byt2Power(2) = 4 ' 00000100 54 m_byt2Power(3) = 8 ' 00001000 55 m_byt2Power(4) = 16 ' 00010000 56 m_byt2Power(5) = 32 ' 00100000 57 m_byt2Power(6) = 64 ' 01000000 58 m_byt2Power(7) = 128 ' 10000000 59
60 ' Could have done this with a loop calculating each value, but simply 61 ' assigning the values is quicker - BITS SET FROM RIGHT
65 m_lOnBits(3) = 15 ' 00000000000000000000000000001111 66 m_lOnBits(4) = 31 ' 00000000000000000000000000011111 67 m_lOnBits(5) = 63 ' 00000000000000000000000000111111 68 m_lOnBits(6) = 127 ' 00000000000000000000000001111111 69 m_lOnBits(7) = 255 ' 00000000000000000000000011111111 70 m_lOnBits(8) = 511 ' 00000000000000000000000111111111 71 m_lOnBits(9) = 1023 ' 00000000000000000000001111111111 72 m_lOnBits(10) = 2047 ' 00000000000000000000011111111111 73 m_lOnBits(11) = 4095 ' 00000000000000000000111111111111 74 m_lOnBits(12) = 8191 ' 00000000000000000001111111111111 75 m_lOnBits(13) = 16383 ' 00000000000000000011111111111111 76 m_lOnBits(14) = 32767 ' 00000000000000000111111111111111 77 m_lOnBits(15) = 65535 ' 00000000000000001111111111111111 78 m_lOnBits(16) = 131071 ' 00000000000000011111111111111111 79 m_lOnBits(17) = 262143 ' 00000000000000111111111111111111 80 m_lOnBits(18) = 524287 ' 00000000000001111111111111111111 81 m_lOnBits(19) = 1048575 ' 00000000000011111111111111111111 82 m_lOnBits(20) = 2097151 ' 00000000000111111111111111111111 83 m_lOnBits(21) = 4194303 ' 00000000001111111111111111111111 84 m_lOnBits(22) = 8388607 ' 00000000011111111111111111111111 85 m_lOnBits(23) = 16777215 ' 00000000111111111111111111111111 86 m_lOnBits(24) = 33554431 ' 00000001111111111111111111111111 87 m_lOnBits(25) = 67108863 ' 00000011111111111111111111111111 88 m_lOnBits(26) = 134217727 ' 00000111111111111111111111111111 89 m_lOnBits(27) = 268435455 ' 00001111111111111111111111111111 90 m_lOnBits(28) = 536870911 ' 00011111111111111111111111111111 91 m_lOnBits(29) = 1073741823 ' 00111111111111111111111111111111 92 m_lOnBits(30) = 2147483647 ' 01111111111111111111111111111111 93
94 ' Could have done this with a loop calculating each value, but simply 95 ' assigning the values is quicker - POWERS OF 2
96 m_l2Power(0) = 1 ' 00000000000000000000000000000001 97 m_l2Power(1) = 2 ' 00000000000000000000000000000010 98 m_l2Power(2) = 4 ' 00000000000000000000000000000100 99 m_l2Power(3) = 8 ' 00000000000000000000000000001000 100 m_l2Power(4) = 16 ' 00000000000000000000000000010000 101 m_l2Power(5) = 32 ' 00000000000000000000000000100000 102 m_l2Power(6) = 64 ' 00000000000000000000000001000000 103 m_l2Power(7) = 128 ' 00000000000000000000000010000000 104 m_l2Power(8) = 256 ' 00000000000000000000000100000000 105 m_l2Power(9) = 512 ' 00000000000000000000001000000000 106 m_l2Power(10) = 1024 ' 00000000000000000000010000000000 107 m_l2Power(11) = 2048 ' 00000000000000000000100000000000 108 m_l2Power(12) = 4096 ' 00000000000000000001000000000000 109 m_l2Power(13) = 8192 ' 00000000000000000010000000000000 110 m_l2Power(14) = 16384 ' 00000000000000000100000000000000 111 m_l2Power(15) = 32768 ' 00000000000000001000000000000000 112 m_l2Power(16) = 65536 ' 00000000000000010000000000000000 113 m_l2Power(17) = 131072 ' 00000000000000100000000000000000 114 m_l2Power(18) = 262144 ' 00000000000001000000000000000000 115 m_l2Power(19) = 524288 ' 00000000000010000000000000000000 116 m_l2Power(20) = 1048576 ' 00000000000100000000000000000000 117 m_l2Power(21) = 2097152 ' 00000000001000000000000000000000 118 m_l2Power(22) = 4194304 ' 00000000010000000000000000000000 119 m_l2Power(23) = 8388608 ' 00000000100000000000000000000000 120 m_l2Power(24) = 16777216 ' 00000001000000000000000000000000 121 m_l2Power(25) = 33554432 ' 00000010000000000000000000000000 122 m_l2Power(26) = 67108864 ' 00000100000000000000000000000000 123 m_l2Power(27) = 134217728 ' 00001000000000000000000000000000 124 m_l2Power(28) = 268435456 ' 00010000000000000000000000000000 125 m_l2Power(29) = 536870912 ' 00100000000000000000000000000000 126 m_l2Power(30) = 1073741824 ' 01000000000000000000000000000000 127 End Sub 128
141 LShift = 0 142 End If
143 Exit Function
144 ElseIf iShiftBits < 0 Or iShiftBits > 31 Then 145 Err.Raise 6
146 End If 147
148 If (lValue And m_l2Power(31 - iShiftBits)) Then
149 LShift = ((lValue And m_lOnBits(31 - (iShiftBits + 1))) * _ 150 m_l2Power(iShiftBits)) Or &H80000000
151 Else
152 LShift = ((lValue And m_lOnBits(31 - iShiftBits)) * _ 153 m_l2Power(iShiftBits)) 154 End If 155 End Function 156 157 '******************************************************************************* 158 ' RShift (FUNCTION) 159 '******************************************************************************* 160 Private Function RShift(ByVal lValue As Long, _
161 ByVal iShiftBits As Integer) As Long 162 If iShiftBits = 0 Then
163 RShift = lValue 164 Exit Function
165 ElseIf iShiftBits = 31 Then 166 If lValue And &H80000000 Then 167 RShift = 1
168 Else
169 RShift = 0 170 End If
171 Exit Function
172 ElseIf iShiftBits < 0 Or iShiftBits > 31 Then 173 Err.Raise 6
174 End If 175
176 RShift = (lValue And &H7FFFFFFE) \ m_l2Power(iShiftBits) 177
178 If (lValue And &H80000000) Then
179 RShift = (RShift Or (&H40000000 \ m_l2Power(iShiftBits - 1))) 180 End If 181 End Function 182 183 '******************************************************************************* 184 ' LShiftByte (FUNCTION) 185 '******************************************************************************* 186 Private Function LShiftByte(ByVal bytValue As Byte, _
187 ByVal bytShiftBits As Byte) As Byte 188 If bytShiftBits = 0 Then
189 LShiftByte = bytValue 190 Exit Function
191 ElseIf bytShiftBits = 7 Then 192 If bytValue And 1 Then 193 LShiftByte = &H80 194 Else
195 LShiftByte = 0 196 End If
197 Exit Function
198 ElseIf bytShiftBits < 0 Or bytShiftBits > 7 Then 199 Err.Raise 6
200 End If 201
202 LShiftByte = ((bytValue And m_bytOnBits(7 - bytShiftBits)) * _ 203 m_byt2Power(bytShiftBits)) 204 End Function 205 206 '******************************************************************************* 207 ' RShiftByte (FUNCTION) 208 '******************************************************************************* 209 Private Function RShiftByte(ByVal bytValue As Byte, _
210 ByVal bytShiftBits As Byte) As Byte 211 If bytShiftBits = 0 Then

![Fig. 2.4 Hand geometry control system [8]](https://thumb-us.123doks.com/thumbv2/123dok_us/774574.2597960/19.892.243.649.118.419/fig-hand-geometry-control-system.webp)