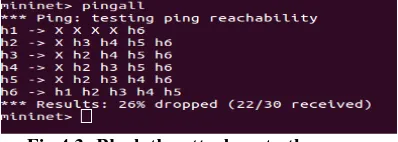
DDOS Detection and Denial Using Third Party Application in SDN
Full text
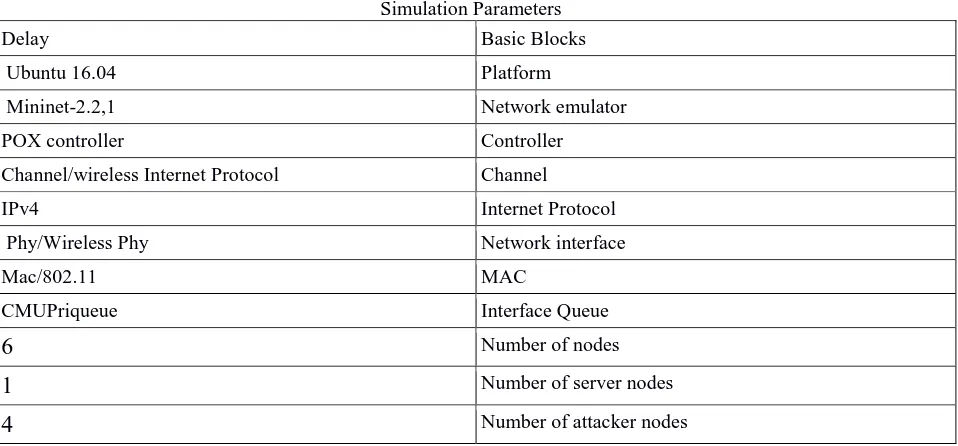
Figure
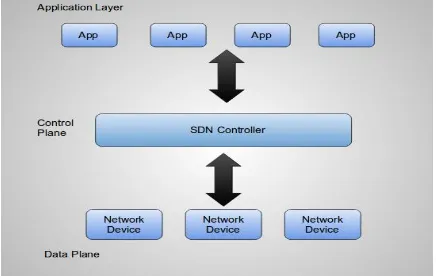
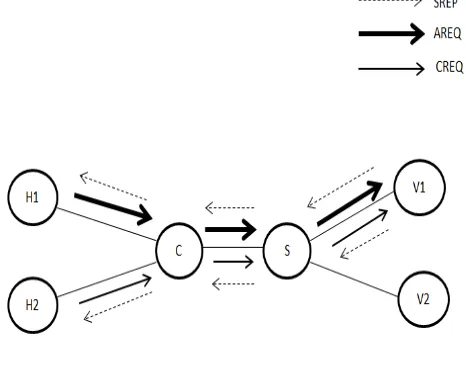
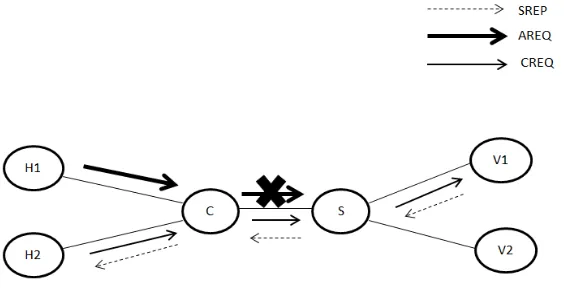
Related documents
Results suggest that the probability of under-educated employment is higher among low skilled recent migrants and that the over-education risk is higher among high skilled
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
• Follow up with your employer each reporting period to ensure your hours are reported on a regular basis?. • Discuss your progress with
4.1 The Select Committee is asked to consider the proposed development of the Customer Service Function, the recommended service delivery option and the investment required8. It
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
First, based on the teachers the average error and standard d preferred output and the syste type-1 fuzzy logic systems (on we present only a sample of th show that the type-2
Minors who do not have a valid driver’s license which allows them to operate a motorized vehicle in the state in which they reside will not be permitted to operate a motorized