Optimal XOR based (2,n)-Visual Cryptography Schemes
Full text
Figure

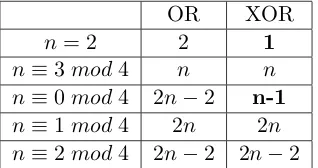
Related documents
In general, human capital strategy including training, development, and empowerment is formulated in universities of medical sciences throughout the country and
A cohabiting individual of higher type (a woman) will suffer from a utility loss in comparison to what she could get when matched with a partner of the same class under
Conclusion: According to risk of suicide ideation and high rate of the suicide attempt in addicts, especially after relapse identification of risk factors and pre-determinants
Levels and pattern of methylation of CpG sites along the BRCA1 promoter region in WBC from a newborn carriers, b woman carriers, c breast cancer patients, and i ovarian
Notwithstanding his foreman’s concern as a result of repeated warnings from the general contractor about employees being exposed to fall hazards, Bob Anderson made no attempt
1) Dense omental, intestinal adhesions to anterior, lateral abdominal well. 3) Dense, fragile adhesions; with the anatomy of small and large intestines distorted and formed a
Department Store sites with a cosmetics
Nevertheless, an inspection of the modification indices revealed four significant direct effects from stressors on two dimensions of CWB (i.e., interpersonal conflict and lack