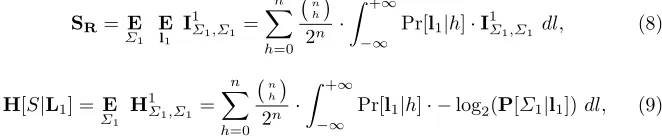Towards Security Limits in Side-Channel Attacks
Full text
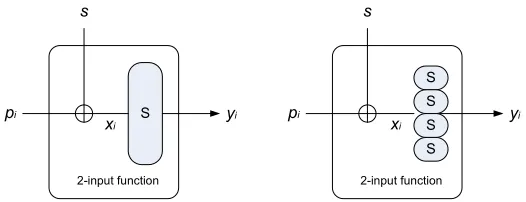
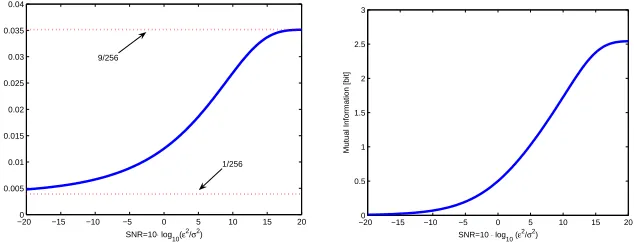
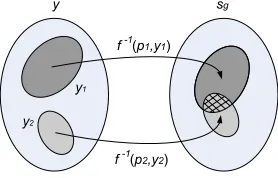
Figure

Related documents
We conducted a comparative bind- ing analysis of the putative haloacid-binding site of DehrP with six haloacid ligands (monobromoacetate, MBA; monochloroacetate, MCA;
These strains are only antigen-negative with respect to the adult-specific antibodies; an unadsorbed antiserum that cross-reacts with the L4 surface also cross-reacts
Based on this index, we de-veloped ProMiSH-E that finds an optimal subset of points and ProMiSH-A that searches near-optimal results with better data structures
talent management practice helps enhancing their skills for effective work performance for. effective work performance to a
Consistent with industry standards, the correlation between test and analysis results enables extension of the qualification by combined analysis and testing to other equipment,
MACRAE and ANDERSON observed a large frequency change of mitochondrial DNA (mtDNA) haplo- types in a population initiated with two allopatric strains of
BMI: Body mass index; CI: Confidence interval; FPG: Fasting plasma glucose; HAART: Highly active antiretroviral therapy; HDL-C: High-density lipoprotein cholesterol; HIV:
Ahmedov and Bessler (2012) discovered another extremely intriguing finding in 2008 that amidst the crisis period, Hang Seng followed its global peers such as DJIA or