Spatial and Frequency Domain Digital
Image Watermarking Techniques for
Copyright Protection
Manasha Saqib
Department of CSE, SEST Jamia Hamdard, New Delhi, India
manashasaqib@gmail.com
Sameena Naaz *
Department of CSE, SEST Jamia Hamdard, New Delhi, India
snaaz@jamiahamdard.ac.in * Corresponding Author Abstract
Digital image watermarking is considered to be one of the extremely valuable technology for providing security to the digital media on web. The act of concealing a message related to a digital signals in various forms such as an image, video, song inside the signal itself is known as Digital image watermarking. Watermarking is significant application in the image processing. Watermarking is the process of embedding predefined designs into multimedia information in a way that the degradation of image quality is reduced and remain at an imperceptible level. It is fundamentally required to shield the data from the unauthorized access. The important issues to be considered while performing digital image watermarking are imperceptibility, capacity robustness, and security. In this paper, an overview of an image watermarking, types of watermarking and necessities of digital watermarking is presented. It presents various techniques of digital image watermarking depending upon spatial & frequency domain.
Key words: Digital Watermarking, Discrete Cosine Transform, Discrete Wavelet Transform, Discrete Fourier Transform, Singular Value Decomposition, Security.
1. Introduction
The term digital watermarking appeared first in 1993, when Tirkel introduced two watermarking methods to conceal the watermark information within the images. With the expanding utilization of the web, protection of copyright for the multimedia information has transformed into a significant issue. The protection of the information is primary concern for reliable communication. Historically, the cryptographic methods were utilized for giving the protection to the data however, it has its own limitation. To determine the issue of the traditional methods, the main target has been on the investigation of the digital watermarking technology. It will increase the security of the information and the data is protected from unauthorized access [1]. Digital watermark technique permits an individual to include hidden copyright data or alternative confirmation message to digital media. Watermarking is the method that inserts information called a watermark or digital signature or label or tag into a multimedia object so that watermark can be later extracted. Digital watermark is a sequence of data which contains the owners copyright for the multimedia information. It is embedded invisibly or visibly into other image so that it can be later extracted as a proof that an owner is authentic. The watermark might be an emblem, a random sequence or a label [2]. The aim of a typical good watermarking scheme is that under malicious attack it must keep the inserted watermark very robust in spectral and real domains.
2. Watermarking Requirements
The most vital prerequisites for digital watermarking are outlined as beneath. Depending upon the application, the relative significance of these properties may change.
2.1 Imperceptibility
2.2 Robustness
Regardless of the possibility that the algorithmic rule of the watermarking technique is public, it should be impossible to eliminate the watermark. Clearly, the watermark can be evacuated with adequate knowledge of particular inserting process however it ought to be robust against an extensive variety of attacks. [5-6]
2.3 Capacity
An appropriate measure of data is inserted into an image in a watermarking framework. This inserted measure of data in a watermarked image is referred to as data payload. It implies the quantity of bits encoded with the image and the measure of it must be sufficient in order to make possible the imagined application. [4, 7]. 2.4 Security
The aim of the watermark is to directly eliminate the inserted information that is the watermark should resist against attacks. Without the knowledge of the secret key, it should be impossible for an attacker to remove, recover or change the watermark. [8]
3. Types of Watermarking
The various types of watermarking are:
3.1 Visible: The visible watermark is used to identify the owner [9]. In this the watermark is noticeable such as a logo or a text.
3.2 Invisible: Here, the watermark is inserted into the image such that the human eye cannot see it. In order to secure the image authentication and furthermore keep it from being duplicated, invisible watermark is used [3]. Invisible watermark is divided into following three types:
3.2.1 Robust Watermark
The aim of robust watermark is to insert data in a file that cannot be effectively distorted. Robust watermarks are designed to oppose the encountered manipulations. It is used in those applications where security is the primary issue [9].
3.2.2 Fragile Watermark
Fragile watermark is designed with very less robustness. It is used to check the trustworthiness of articles [9]. 3.2.3 Public and Private Watermark
As per the secrecy necessities for the key that is used to insert and recover watermarks public and private watermark are separated. During the detection process, if the original image is unknown then it is called a blind watermark or a public watermark and it is called a private watermark or a non-blind watermark if the original image is known [9].
4. Classification of Watermarking
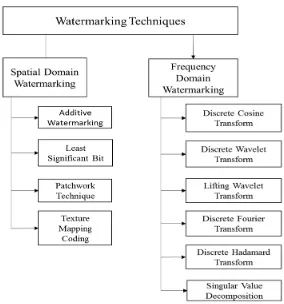
Digital watermarking includes different watermarking techniques for the security of the information. Based on different criteria, Watermarking techniques can be divided into different categories. Depending upon the domain in which the watermark is embedded, they are classified into spatial and frequency domain techniques.
4.1 Spatial-domain watermarking
The information can be added by varying the values of the pixel of the carrier signal in Spatial-domain watermarking. The values of color or the intensities of some selected pixels are directly modified by Spatial-domain technique. During embedding of watermark, no changes can be applied to the host signal. This technique is not robust against various attacks [10]. The principle qualities of spatial-domain technique is that they have low computational complexity and are simple. This technique is less tedious when compared to frequency domain techniques or wavelet. The various spatial domain techniques are Additive Watermarking, Least Significant Bit, Patchwork and Text mapping coding etc.
4.1.1 Additive Watermarking
Figure 1: Image Watermarking Techniques
4.1.2 Least Significant Bit (LSB)
The most straightforward method to implement is LSB technique. In this process watermark bit is added to each pixel of the LSB. During extraction or detection method, the last bit of every pixel is read to unveil the watermark information. In this technique, regardless of the possibility that the watermarked image is cropped the recipient can even get the required information since the information is inserted number of times. This method cannot be utilized for practical purposes as it is very sensitive to noise. It is not very robust [11]
Advantages of LSB Technique:
1. It is one of the simplest strategy to implement.
2. For both watermark embedding and watermark extraction, the computational complexity of Least Significant Bit is very less.
3. In LSB technique the degradation of the quality of an image is less. Disadvantages of LSB Technique
1. Least Significant Bit technique is not very robust against various attacks.
2. The various attacks such as scaling, cropping and shuffling destroy the inserted watermark. 3. This technique is extremely sensitive to noise.
4.1.3 Patchwork Technique
Patchwork technique is one of the statistical technique that was developed by Bender et al. Based on a statistic discovered utilizing a Gaussian distribution, patches of watermark are inserted in this technique. The working of this technique is as follows: Two patches are arbitrarily chosen say patch A and patch B. The image information of Patch A is brightened and image information of Patch B is darkened. In this method redundant pattern encoding is used to insert information into an image.
Advantages of Patchwork Technique:
In this method, the robustness against various attacks is very high. Disadvantages of Patchwork Technique:
4.1.4 Texture mapping coding
In the texture part of the image, the watermark is concealed in Texture mapping coding technique. This technique is utilized for just those images which have some content part. Within the persistent arbitrary texture pattern of an image, the data is concealed. Thus, the technique is appropriate for only those images which have variable texture [12].
Advantages of Texture Mapping Coding Technique:
The data is inserted in the continuous arbitrary texture pattern of an image. Disadvantages of Texture Mapping Coding Technique:
This technique is only appropriate for those zones having expansive number of texture images. The human intervention is needed by this technique.
4.2 Frequency Domain Watermarking
Frequency domain inserts a message by changing the transform coefficients of the cover message rather than the pixel values. Ideally, frequency domain has the impact in the spatial domain of allotting the concealed data through various order bits in a way that is robust. There are present a number of transforms which can be applied to digital images, yet there are outstandingly six most commonly used transforms in image watermarking. They are Discrete Cosine Transform (DCT), Discrete Wavelet Transform (DWT), Discrete Fourier Transform (DFT), Lifting Wavelet Transform (LWT), Discrete Hadamard Transform (DHT) and Singular Value Decomposition (SVD).
4.2.1 Discrete Cosine Transform
The conversion of time domain signal into the frequency domain signal is done by Discrete Cosine Transform. The 2-dimensional Discrete Cosine Transform of a matrix gives the transform coefficients in form of other matrix. The lowest frequency coefficients is represented by the left top most corner of the matrix while the highest frequency coefficients is represented by the right bottom most corner of the matrix. In DCT, an image is divided into pseudo frequency bands, and the watermark is embedded into the middle frequency sub bands. On the other hand, the watermark is easy to be concealed if the watermark is embedded in high frequencies, but, this technique is less resistant against attacks [13, 14, and 15].
Advantages of DCT
1. Discrete Cosine Transform has semantically important watermark design. 2. It has great perceptual invisibility.
3. It has adequate robustness. 4. Different client-chosen choices. 5. Reasonable complexity/execution time.
6. Suitable and quick for robustness against JPEG compression.
7. DCT is real transform which has better computational efficiency compared to DFT that is by definition a complex transform.
Disadvantages of DCT 1. DCT has block effect.
2. DCT has effect of picture cropping.
3. One of the fundamental issues and the feedback of the DCT is the blocking effect. In DCT images are divided into blocks that is 8x8 or 16x16 or greater. The issue with these blocks is that if an image is reduced to higher compression ratios, then these blocks are visible. This is known as the blocking effect.
4.2.2 Discrete Wavelet Transform
which are represented by large coefficients present in the high frequency sub-bands. The vertical detail data corresponding to horizontal edges is represented by LH sub-band. While the horizontal detail data corresponding to the vertical edges is represented by HL sub-band. The LL (low pass) sub-band can be additionally divided into another level of decomposition and this procedure is proceeded until the application determine the desired level of decomposition [17, 19].
Wavelet domain is a promising area in watermark embedding. Discrete Wavelet Transform depends on little waves of constrained length and different frequency. The coefficients demonstrate the measure of likeness between the selected wavelet and the signals of the image. Most of the similarities of the signal are shown by the big coefficients. Firstly, in Discrete Wavelet Transform the cover image is converted into frequency domain and after that the coefficients of frequency are modified depending upon the transformed coefficients of the watermark and afterwards a robust watermarked image is achieved. Then the inverse discrete wavelet transform (IDWT) is applied to obtain the reconstructed image [20].
Advantages of DWT
1. It has excellent localization of the spatial domain. 2. It has frequency spread (that is multi resolution).
3. The time frequency analysis is excellent (Discrete Wavelet Transform captures both information of location and frequency).
4. The energy compaction is good. 5. The signal processing attacks is good.
6. It is compatible with JPEG 2000 for compaction. Disadvantages of DWT
1. The cost of processing DWT when compared to DCT is higher.
2. The utilization of greater Discrete Wavelet Transform basis functions produces ringing noise and blurring near edge areas in video frames or images.
3. It has very large compression time.
4 DWT is less robust against various geometric attacks. 4.2.3 Lifting Wavelet Transform
The Lifting Wavelet Transform technique was proposed for the efficient implementation of the two dimensional Discrete Wavelet Transform. It is called as Lifting Wavelet Transform because of its construction on spatial wavelets. The fundamental idea of this technique is to remove the redundancy and this can be achieved by using the correlation in the image pixels values [21, 22]. The LWT technique has three stages:
1. Split. 2. Predict 3. Update.
In the split phase, the input sequence is split into two sub-sequences which consists of the odd samples and the even samples. In predict and update phases, the low-pass values and the high-pass values are calculated respectively.
Advantages of LWT
Lifting wavelet Transform technique has many advantages than conventional convolution-based procedures. The advantages of LWT technique are following [21, 22]:
1. The performance improvement of Lifting Wavelet Transform scheme algorithms is more compared to conventional convolution-based implementation. The quantity of operation in the Lifting technique methodology is just about one half of that in the convolution-based methodologies. Lifting technique filters is considered alluring for high-performance implementation because of the reduction in the computational complexity.
2. There is no need to manage image borders in lifting scheme implementation while it is necessary in the conventional convolution-based methodologies.
5. It is easy to build non-linear wavelet transforms with lifting transforms. For example, wavelet transforms that map integers to integers. These transformations are important for lossless image compression and for hardware implementation.
6. The inverse transform of Lifting wavelet transform technique is straightforward because it can easily inverse its functionality order. Thus, to implement IDWT same resources and operations could be reused.
Disadvantages of LWT
1. To take decisions on coefficient values is difficult in LWT because small values represent large coefficients.
4.2.4 Discrete Fourier Transform (DFT)
In image processing, Fourier transform is considered to be one of the finest and comprehensively utilized strategies. Although there is no positioning capability in the space-time domain, but it gives a pure analysis of frequency domain. Fourier transform is not able to offer frequency data in any partial time quantum. Discrete Fourier Transform domain was studied by researches as it gives robustness against various geometric attacks like translation, cropping, rotation and scaling, etc. [23].
• Characteristics of DFT
1. Discrete Fourier Transform of an original image is usually complex valued, thus resulting in the representation of phase and magnitude of an image.
2. Discrete Fourier Transform indicates translation invariance. The representation of the phase of the image is affected by the spatial shifts in the image, but not the representation of magnitude. The magnitude of the Fourier transform in the spatial domain is not affected by the circular shifts.
3. Discrete Fourier Transform is found to be resistant to cropping since cropping effect leads to the blurring of spectrum. It is called normalized coordinates, if the watermarks are inserted in the magnitude and these require no synchronization.
4. The powerful components of the Discrete Fourier Transform are the primary parts containing the low frequencies.
5. The scaling of an image results in amplification of retrieved signal. This can be found by correlation coefficient. There is no effect of Image translation on extracted signal.
6. The rotation of an image results in cyclic shifts of extracted signal. This can be identified by exhaustive search.
7. Inverse scaling in the frequency domain is caused by the scaling in the spatial domain. Image rotation in the spatial domain causes the similar rotation in the frequency domain
• Coefficient Selection Criteria
1. Low frequency coefficients are avoided in DFT because in the spatial domain, low frequency coefficients modification cause visible artifacts.
2. During JPEG compression, high frequency coefficients are removed because they are not well suited.
3. In order to avoid the weakness of both the lower and higher frequencies, the location to insert the watermark is the mid-level frequency.
Advantages of DFT
DFT is good resistant against various rotation and scaling attacks. Disadvantages of DFT
DFT is not robust to some geometric attacks such as shearing and cropping.
Due to loss of time frequency analysis, there is difficulty in processing of DFT (only frequency information).
4.2.5 Discrete Hadamard Transform (DHT)
Discrete Hadamard Transform is mostly used in image compression and image processing. It is a non-sinusoidal change depending upon Hadamard matrix [25]. DHT is an orthogonal square matrix whose order is n and values are (+-1). DHT uses less number of coefficients when compared to other methods. DHT fulfills the following relation:
HHT=I
Where,
H=N*N Hadamard matrix I= Identity matrix
The complexity of DHT method is very less since this technique requires only basic subtraction and addition operation. For concealing or inserting the watermark, DHT has useful high frequency band and middle band compared to the other high gain transformation methods such as DWT and DCT at high noise level. DWT and DCT methods are appropriate just at the low channel noise [26]. If watermark is added during compression by using DCT and DWT, it might get lost but it does not occur in DHT. Noise present in the transmitted signal can be reduced using DWT [27].
Characteristics of Hadamard transform
1. DHT uses only basic subtraction and addition operation. That is there is no need of multiplication and division operation. Only real values are used in a matrix and not complex value thus making DHT technique easier.
2. DHT method can survive under the image compression attack.
3. The computational complexity of DHT is less when compared to other transformation methods. Advantages of DHT
1. The computational cost of DHT is low.
2. DHT is less complex since only addition and subtraction operation is used. 3. DHT consists of real values that is +1 and -1
4. DHT is more efficient. Disadvantages of DHT
1. The complexity of DHT is less when compared to other transform methods but its complexity is more than spatial domain method.
4.2.6 Singular Value Decomposition (SVD)
Singular value decomposition is a numerical method that is based upon linear algebra and is used by complex matrix or factorization of a real matrix having many useful applications in statistics and signal processing. SVD is considered to be one of valuable numerical analysis tools that is used to analyze matrices. SVD is shown from three combined compatible perspectives. On the another hand, it is considered to be a technique for changing correlated variables into a set of uncorrelated variables that better uncover the different relationships among the original information things. In the meantime, Singular value decomposition is a strategy for distinguishing and ordering the measurements along which information points show the most variation. Using SVD it is possible to locate the best estimate of the original information points using less dimensions [24]. Thus, SVD is viewed as a technique for reduction of data. In Singular value decomposition transformation, a matrix is decomposed into three matrices having the size same as that of the original matrix. Given A to be a n × square matrix, this matrix is decomposed into three segments, L, D and U, respectively as shown below:
[L D U] = SVD (A), A’ = LDUT, L-1 where A = LDU.
, , ,
, , ,
, , ,
, , ,
, , ,
, , ,
, , ,
, , ,
, , ,
=∑ (1)
Σ are non-zero matrix diagonals of A. Since, the orthogonal matrices L and U depend on A so SVD is considered to be a nonlinear as given in Equation (1). After applying the inverse SVD transformation reconstructed matrix A’ is obtained. Reduced singular value decomposition is the mathematical method underlying a document type retrieval and word semblance technique. These are therefore called as Latent Semantic Analysis or Latent Semantic Indexing. Thus, the three segments of matrices L, D, and U represent
= Ii and µiT A= σiuiT.
Advantages of SVD
1. SVD has good resistance against signal processing and geometric attacks. It means SVD has high robustness.
2. SVD has high energy compaction. 3. SVD has low computation cost. Disadvantages of SVD
1. There is present false positive problem in SVD. 2. Rising calculation costs if used alone.
Conclusion
Digital image watermarking technique is found to be very useful. Digital image watermarking is considered to be one of the efficient process of sending the information securely. The major factor that is taken into consideration while the information is being exchanged over the web is Security. Earlier numerous watermarking strategies have been proposed for the protected information transmission. On the basis of above review, it is found that the most used technique is spatial domain technique because in this the watermark can be easily and successfully recovered if the image is translated or cropped when compared to frequency domain technique. On another hand, frequency domain technique offers more security but at the same time it is difficult to recover the watermark at the receiver end as the complexity increases. Frequency domain techniques does not provide successful recovery of watermark. Thus, in this paper the various techniques of digital image watermarking, depending upon spatial and frequency domain techniques are discussed.
Reference
[1] Dr. B. Hari Krishna and Dr. T. Sarvanan,” A survey on Digital Image Watermarking”, International Refereed Journal of Engineering
and Science (IRJES), Volume 1, Issue 4 (December 2014).
[2] Mr. Bhupendra Ram and Mr. Manoj Kumar, ‘’ Digital Image Watermarking Technique Using Discrete Wavelet Transform and
Discrete Cosine Transform”, International Journal of Current Research in Multidisciplinary (IJCRM), Volume 1, Issue 1 (May 2016).
[3] E. Hussein and M. A. Belal, "Digital Watermarking Techniques, Applications and Attacks Applied to Digital Media: A Survey,"
International Journal of Engineering, vol. 1, 2012.
[4] M. A. Akhaee and F. Marvasti, "A Survey on Digital Data Hiding Schemes: Principals, Algorithms, and Applications," The ISC
International Journal of Information Security, vol. 5, p. 5, 2013.
[5] A. A. Hood and N. Janwe, "Robust Video Watermarking Techniques and Attacks on Watermark–A Review," International Journal of
Computer Trends andTechnology-volume4, Issue1, 2013.
[6] G. Gupta and J. Pieprzyk, "Database relation watermarking resilient against secondary watermarking attacks," in Information Systems
Security, Springer, 2009, pp. 222-236.
[7] N. M. Basheer and S. S. Abdul Salam, "Digital, Image Watermarking Algorithm in Discrete Wavelet Transform Domain Using HVS
Characteristics," in Proceedings of the IEEE International Conference on Information Technology: Coding and Computing, 2011, pp. 122-127.
[8] A. Nikolaidis, "Local distortion resistant image watermarking relying on salient feature extraction," EURASIP Journal on Advances in
Signal Processing, vol. 2012, pp. 1-17, 2012.
[9] Sasmita Mishra, Amitav Mahapatra, Pranati Mishra, “A Survey on Digital Watermarking Techniques”, International Journal of
Computer Science and Information Technologies, ISSN: 0975-9646, Vol. 4, 2013, 451-456.
[10] Namita Chandrakar and Jaspal Bagga, ‘’Performance Comparison of Digital Image Watermarking Techniques: A Survey”,
International Journal of Computer Applications Technology and Research Volume 2– Issue 2, 126 - 130, 2013.
[11] K.P.Sonam, K.I.Ramachandran –“Insight into Wavelets from, Theory to Practice”.
[12] Tamirat Tagesse Takore, Dr P. Rajesh Kumar and Dr P. Rajesh Kumar, “A Modified Blind Image Watermarking Scheme Based on
DWT, DCT and SVD domain Using GA to Optimize Robustness”, International Conference on Electrical, Electronics and Optimization Techniques (ICEEOT), 2016.
[13] S. D. Lin, et al., "Improving the robustness of DCT-based image watermarking against JPEG compression," Computer Standards &
Interfaces, vol. 32, pp. 54-60, 2010.
[14] S. Bedi, et al., "Robust secure SVD based DCT–DWT oriented watermarking technique for image authentication," in International
Conference on IT to celebrate S. Charmonman's 72nd birthday, 2009, pp. 46.1-46.7.
[15] D. Arya, "A survey of frequency and wavelet domain digital watermarking techniques," International Journal of Scientific &
Engineering Research, vol. 1, 2010.
[16] A. K. Singh, et al., "Wavelet Based Image Watermarking: Futuristic Concepts in Information Security," Proceedings of the National
Academy of Sciences, India Section A: Physical Sciences, vol. 84, pp.345-359, 2014.
[17] M. Ali and C. W. Ahn, "An optimized watermarking technique based on self-adaptive DE in DWT–SVD transform domain," Signal
[18] H. A. Abdallah, et al., "Blind Wavelet-Based Image Watermarking," International Journal of Signal Processing, Image Processing & Pattern Recognition, vol.4, 2011.
[19] Dolatabadi, Z.S.S., A.B.A. Manaf, and M. Zamani, Using Three Levels DWT to Increase Robustness against Geometrical Attacks.
International Journal of Advancements in Computing Technology, 2013. 5(14): p.86
[20] N. Bisla and P. Chaudhary, "Comparative Study of DWT and DWT-SVD Image Watermarking Techniques," International Journal,
vol. 3, 2013.
[21] I. Daubechies and W. Sweldens, Factoring Wavelet Transforms into Lifting Steps, Journal of Fourier Analysis and Applications 4
(1998), no. 3, 247–269.
[22] M. Ferretti and D. Rizzo, A Parallel Architecture for the 2D Discrete Wavelet Transform with Integer Lifting Scheme, Journal of VLSI
Signal Processing 28 (2001),165–185.
[23] Vinita Gupta and Mr. Atul Barve, “International Journal of Advanced Research in Computer Science and Software Engineering”, A
Review on Image Watermarking and Its Techniques, Volume 4, Issue 1, January 2014.
[24] Manjit Thapa1 and Sandeep Kumar Sood, On Secure Digital Image Watermarking Techniques, Journal of Information Security, 2011,
2, 169-184.
[25] A.N Akansu and R.A.Haddad, “Multiresolution Signal Decomposition: Transforms, Sub bands and Wavelets”, Academic Press Inc.,
1992.
[26] A.T.S Ho, Shen Jun, A.K.K.Chow, and J.Woon, “Robust digital image-in-image watermarking algorithm using the fast Hadamard
Transform,” in Proc .IEEE ISCAS’03, vol 3, May 2003, pp.826-829
[27] Iffat Rehman Ansari, Shahnawaz Uddin, “Signal Denoising Using Discrete Wavelet Transform”, International Journal of Engineering