Secure Storage of Data on Android Based Devices
Full text
Figure
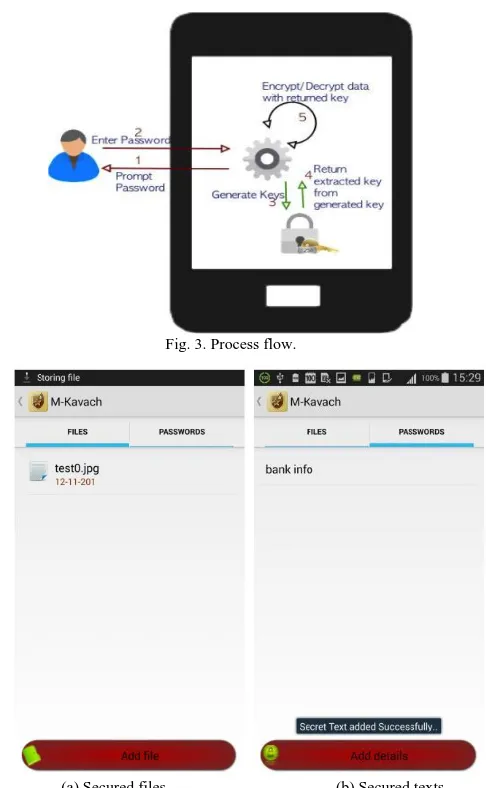
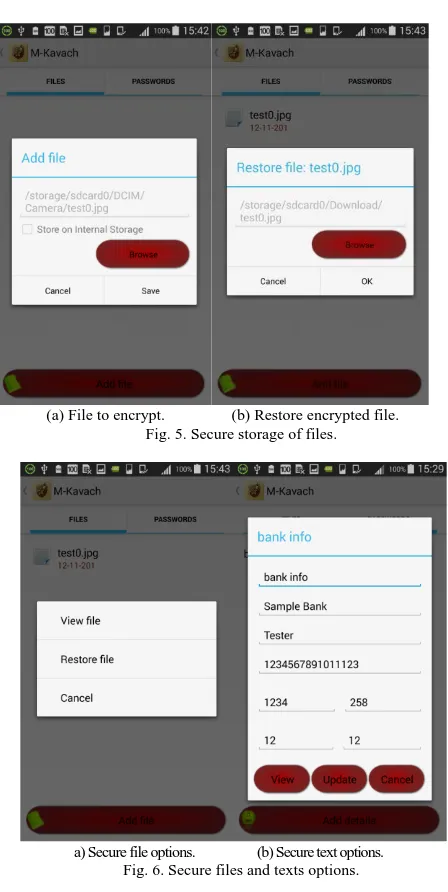
Related documents
tangent of this transformation, shown in Figure 3a, are the actual and perceived angular velocities,
Giant panda population estimates for Wanglang Nature Reserve derived by differentiating individuals from bite sizes of bamboo fragments in feces.. Data were collected during each of
of the GSEs. It is not sufficient for any single GSE to argue that its own financial condition is sound. If one GSE comes under a cloud, others may also. That has been our
Children have been the subjects of medical research for hundreds of years, but the present survey is the first to be conducted with adequate statistical power (the computed a
Results indicated that all the predictors including autonomy, recognition and appreciation, promotion opportunities, and pay incentives turned out to be significantly
Prime enrollees FY2018 51 Value is not significantly different than benchmark Prime enrollees FY2019 41 Significantly lower than benchmark (p < .05) Prime enrollees FY2020
Taking selfies and sharing photos on popular social media platforms like Facebook and Twitter are considered to be one of the biggest contributors to the rise in narcissistic
and LCP olecranon plate Good Fair Fair Fair Excellent Excellent Excellent Good Good Poor Good LOM Ulnar nerve Sx Heterotophic ossification LOM, ulnar nerve Sx Ulnar nerve Sx