1. Implementation of lossless visible watermarking and data hiding using advanced encryption standard algorithm
Full text
Figure
![Fig 1.Illustration of mapping the center pixel of a 3*3 image using Algorithm 1.Only the mapping of the center pixel is shown for clarity; the east and south pixels are depicted as TBD (to be determined) in W [9]](https://thumb-us.123doks.com/thumbv2/123dok_us/1393423.1650779/3.612.146.482.499.698/illustration-mapping-center-algorithm-mapping-clarity-depicted-determined.webp)
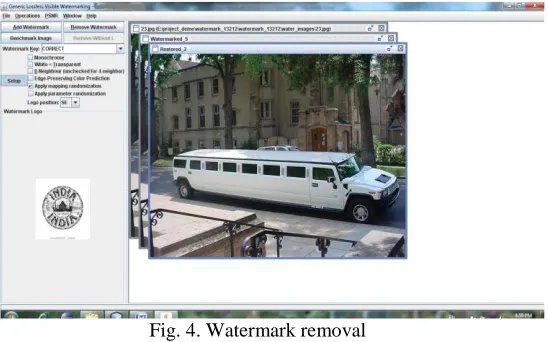

Related documents
Some strategies including SYMRCM permutation, Jacobi scaling before factorization and efficient diagonal perturbation are adopted to improve the robustness and efficiency of
Estimates of linkage disequilibria and their log-likelihood ratio (LR) test statistics for a small subset of RAPD markers genotyped to study the population structure of hickory trees
vivo -derived embryos, displaying cell numbers, embryo volume, H19 and Snrpn. methylation, H19 imprinted expression, and Atp1a1 and Slc2a1 expression
This is a feasibility study which aims to inform the de- sign of a larger trial to investigate a Community Health Intervention through Musical Engagement (CHIME) to help reduce
Thus, the present study investigated the influence of Teachers Performance Appraisal (TPA) policy on effectiveness in curriculum evaluation in public secondary schools in
The presented case exemplifies chronic back pain in a 48 year old woman as symptom of extensive cystic endosalpingiosis.. Endosalpingiosis refers to the presence of ectopic epi-
International Journal of Scientific Research in Computer Science, Engineering and Information Technology CSEIT1835143 | Received 15 May 2018 | Accepted 31 May 2018 | May June 2018 [