La modellazione di sistemi meccanici, applicazioni per il controllo e la misura = Mechanical System Modelling, Applications for Measurement and Control
Full text
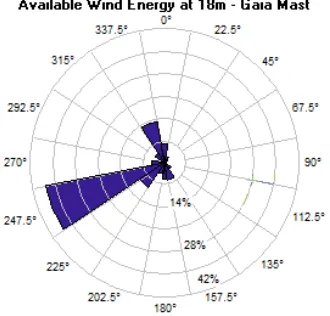
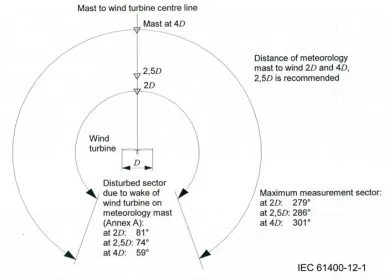
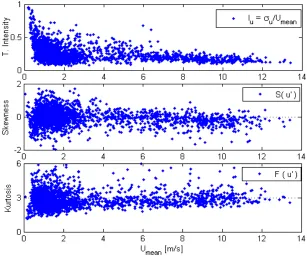
Figure


Related documents
Norma Hart 190 N First Ave Coal City, IL 60416 815-634-2676 Email: normahart1@cbcast.com 1351 Holder Ln Geneva, FL 32732 John Neff.. Am Federation of New
This literature review explored the cross–sectoral evidence regarding alliance, prime and outcome based contracting in order to identify learning which could be applied
By creating both plant-specific agglomeration measures and labour markets at 0.5 kilometres, 5 kilometres and 50 kilometres from each of the 8,313 plants in the sample, it was
In particular, it was an open problem whether subsumption and unsatisfiability were intractable for the language A£t', which extends F £- with unrestricted
6 mm thick AZ91 casting alloy plates were subjected to normal friction stir processing (NFSP, in air) and submerged friction stir processing (SFSP, under water), and microstructures
Single Board Computer (Jetson Nano) Joystick GPS Stereo camera + inbuilt IMU Battery Voltage Transformer Servo Motor controller Speed throttle controller WiFi dongle RC
The main issues have to do with: (1) the dangers of labeling an adolescent as a psychopath; (2) the implications of the PCL: YV for classification, sentencing, and treatment; (3)
In this paper, we extend the work of Niki- forakis et al. [16], which focused on revealing inconsis- tencies to detect user agent spoofers, to consider a much wider range of