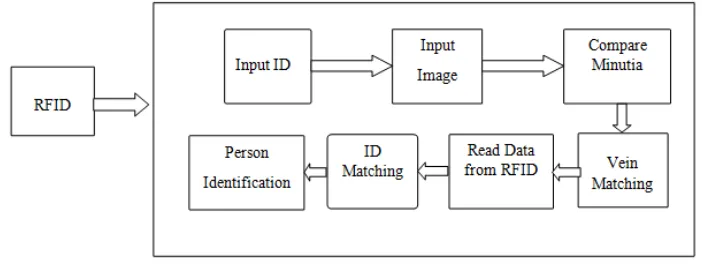
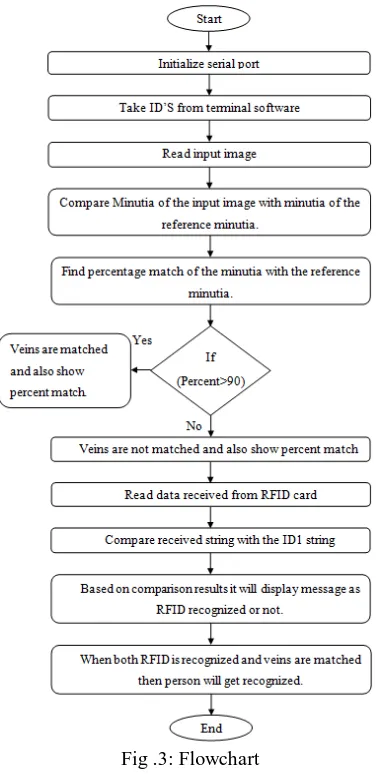
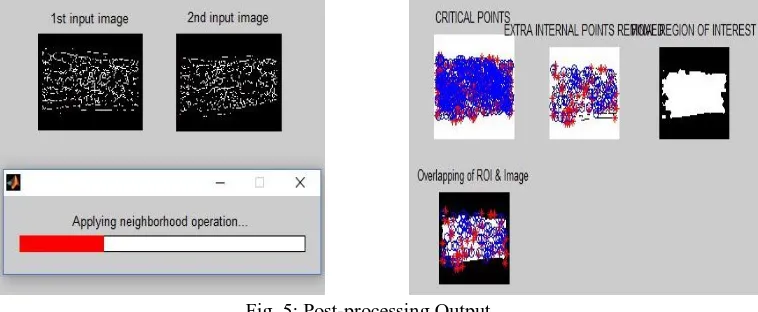
Two Level Authentication for Machines Using RFID & Finger Vein Recognition
Full text
Figure
Related documents
CCTV: closed-circuit television; MOT: multi-object tracking; CNN: convolutional neural networks; ROI: regions of interest; CARoI: context-aware RoI; DA: data association; MHT:
Transformational leadership was measured using a 16-item version of Bass and Avolio’s (1990) multifactor leadership questionnaire (MLQ).These items ask followers to
Objectives of development of this system are to develop a cost effective, notification of potholes and humps and efficient car automation, read the depth and height of potholes and
The plane waves propagation is investigated under the influence of magnetic field to solve the two temperature problem in a two dimensional deformation at the free surface
In an interview at the University of Melbourne, Australia in July 2013 between Richard James and John Clarke, Co-editor of the International Journal of the First Year in
Ground state means that all of the lowest possible energy levels (up to the proper number of electrons for the element) are
In clinicopathological analysis, they also indicated that the nuclear overexpression of SOX4 was observed in tumor cells of hepatocellular carcinoma tissues, which was correlated