An Integrated Cyber Security Risk Management Approach for a Cyber Physical System
Full text
Figure



Related documents
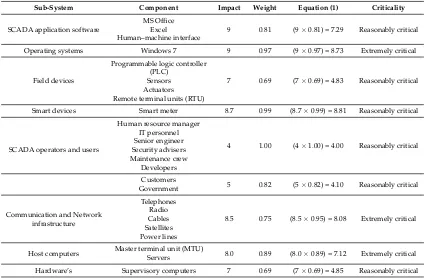
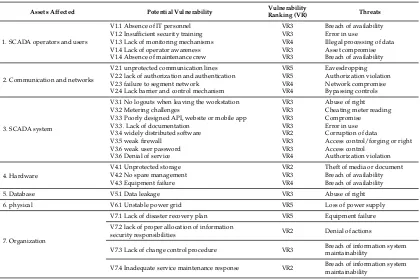
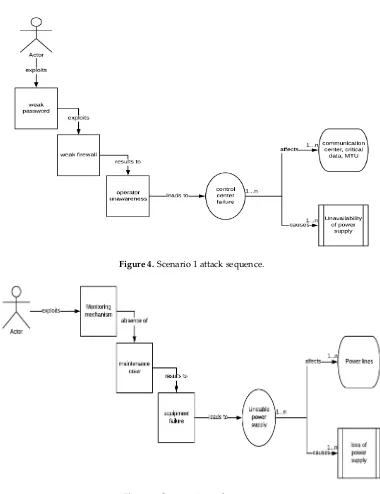
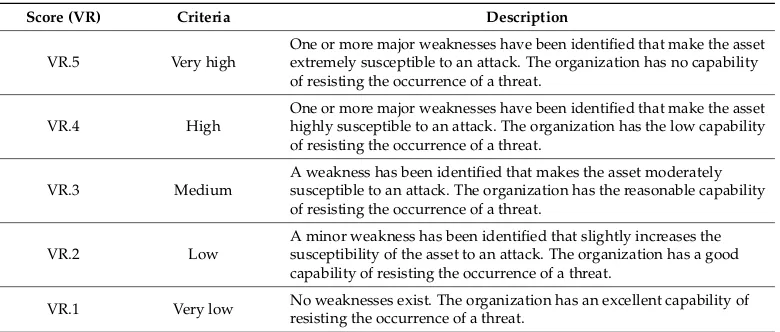
The purpose of Cyber Risk Management is to identify, analyze, and mitigate cyber-security threats and risks to critical information and technology assets and services. Risk
Items 5 and 6 were asked of participants in the control (no attentional instruction) condition, and response options ranged from 1 (not at all) to 5 (very much). Items 7 and 8
потенціалу, до якої поряд з кількісно вимірюваними показниками включено показники якісної оцінки стану регіону, а також методичні
The tool post grinder can shape the receiver every where, except for a small section just above the bolt stop lug, I finish that with files and a rotary tool.. With the grinding
To construct 6-fold symmetric multiple bi-frames, first, we represent the decomposition and reconstruction algorithms by symmetric templates by using the idea of the lifting
hydrothermal treatments caused a certain surface inactivation, marked by decreased 261. surface roughness, increased hydrophobic character and darkened
ryn March’s study on the Solu Khumbu Sherpa almost 40 years ago (1977), community mountain-closure rituals and practices appear to have been defunct at the time of docu-