Security, Trust and Privacy In Cyber (Stpc (Cyber)
Full text
Figure


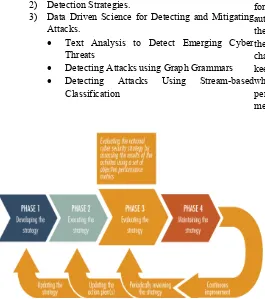

Related documents
For example, according to Armstrong (2006, p.8), “the overall purpose of human resource management is to ensure that the organization is able to achieve success
The argument for a direct link between human resource practices and employee performance in R&D team settings hinges on the idea that high-involvement
We will show that the simple polarized incoherent phase observed in Ref.(25) can be captured by perturbation theory and show that its excited states can be reproduced by
Further research is needed to determine the effects of thinning and carbon prices on the optimal management of other stands that might vary in species composition, growth rates,
Although existing studies have reported positive effects of music on reading skills, no study thus far has focused on music therapy interventions to address the learning needs of
Determination of traffic accident costs in this study was based on the human capital approach where the costs involved fall into three main categories: Human Costs, Property Damage
Prevention Pilot and demonstration projects focused on the recognised road injury risk factors are another key area for activity within the Action Plan. The com- ponents of the
How deep is the ocean if it takes 10 seconds for the sound to echo back to the