Mitigating E-Mail Threats - A Web Content Based Application
Full text
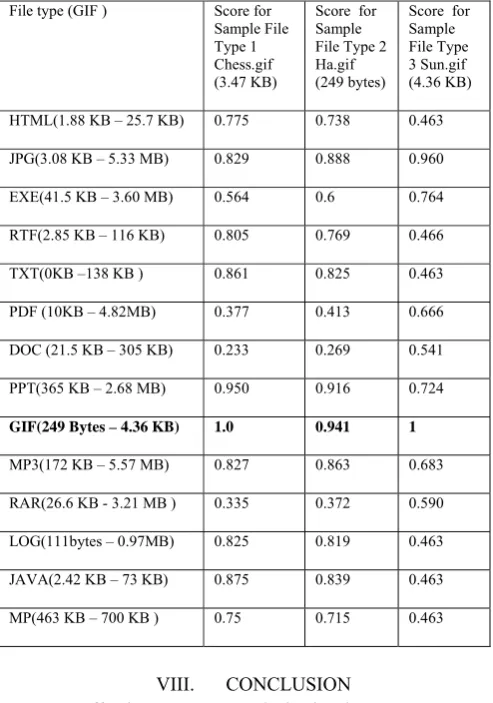
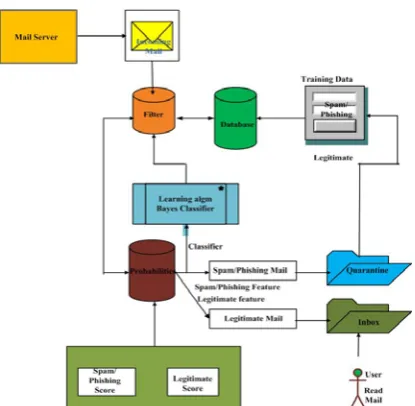
Figure



Related documents
Since the tests for conditions ii) and iii) are conditional on the verification of i), we did not test conditions ii) and iii) for the series that failed the first criterion (i.e.
Opening, replying to, or even clicking a bogus opt-out link in an obvious spam e-mail signals that your e-mail address is active, and more spam will follow.. The only time it is
Ferris, Wayne Gray, Ronald Shadbegian, and Ann Wolverton, “Do Renewable Portfolio Standards Affect Manufacturing Activity Through Higher Electricity Prices?” Presented at IZA
In the left column where the overview of your mailbox is shown there is a mailbox with the name Junk E-Mail.. E-mail marked as Spam by the Surf Spam
pro duction of ethyl al duction of ethyl alcohol for *e.erae purposes( cohol for *e.erae purposes( the ethyl alcohol that is used for. the ethyl alcohol that is used for
FactoryTalk View Studio for Machine Edition software - Configuration software for developing and testing machine-level human machine interface (HMI) applications. Includes
IntesisBox can be configured to notify to the ASCII controller whatever change of value detected for a point by means of spontaneous messages sent through the ASCII
Section E-mail-Based Threats 479 Section Cisco Cloud E-mail Security 479 Section Cisco E-mail Security Appliance 480 Section Mitigation Technology for Web-Based Threats 486