Design of a Secure File transfer System Using Hybrid Encryption Techniques
Full text
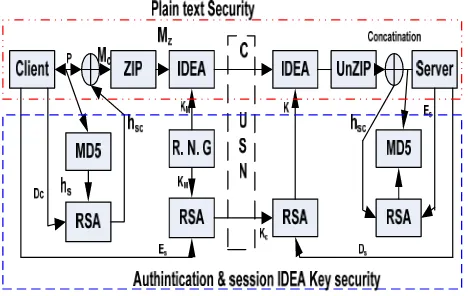
Figure



Related documents
Sun Surety is an insurance company located in South Dakota. Scott Candland is Sun Surety's agent, doing business as Bail Out Fast located in Salt Lake City. Sun Surety,
Using this segmentation, a valid tracking domain is generated and, in combination with anatomi- cally constrained particle filter tractography, allows streamlines to cross the
Fundamentals of CNC Machining A Practical Guide
In this instance you have opened a distance relay characteristic, and you want to test it: the following window is displayed.. In this instance, we have loaded the
The primary purpose of this guide is to provide helpful online resources and useful tips for senior electrical engineering students at Penn State.. The resources in this
curricular needs. Included is a schedule of training sessions, important notes regarding updates to software, and information regarding technology in general at BRPS.
ECLIPSE claiming products available OPV Online Patient Verification. - PVF Patient