The role of individuals’ risk representations in risk management - case-study on lahars in Arequipa (Peru)
Full text
Figure
Related documents
It was decided that with the presence of such significant red flag signs that she should undergo advanced imaging, in this case an MRI, that revealed an underlying malignancy, which
The paper is discussed for various techniques for sensor localization and various interpolation methods for variety of prediction methods used by various applications
Twenty-five percent of our respondents listed unilateral hearing loss as an indication for BAHA im- plantation, and only 17% routinely offered this treatment to children with
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
To resolve the potential effect of H pylori colonisation on hBD1 and hBD2 mRNA expression in the gastric mucosa, semiquan- titative RT-PCR analyses was performed on biopsies
bursts and hence the length of the newly created leader segments as the background electric field
Using key-homomorphic constrained PRFs as constructed in this paper, in Section 5 we construct a scheme for outsourced storage that supports proxy re-encryption and fine-grained
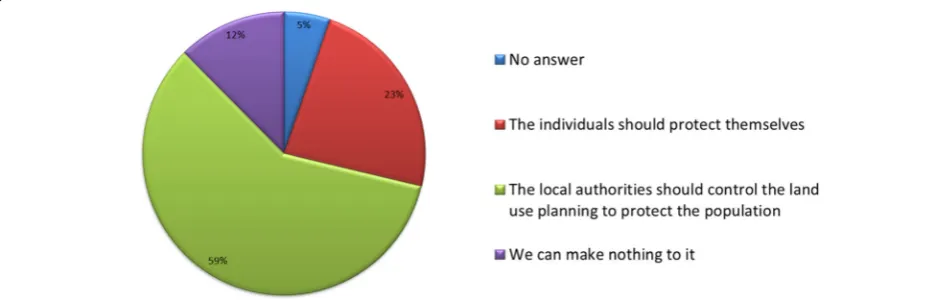
![Fig. 9 Answer to the question: “Here are several suggestions. Which is the one that is closest to your opinion about lahars?” (experience in laharsN = 82 / no experience in lahars N = 118 – all areas) - [Chi2 = (5,44); p = .14; df = 3]](https://thumb-us.123doks.com/thumbv2/123dok_us/9603411.1942688/10.595.55.540.87.300/answer-question-suggestions-closest-opinion-experience-laharsn-experience.webp)