Performance Analysis of DOSN Based on Privacy Preserving and Information Sharing
Full text
Figure

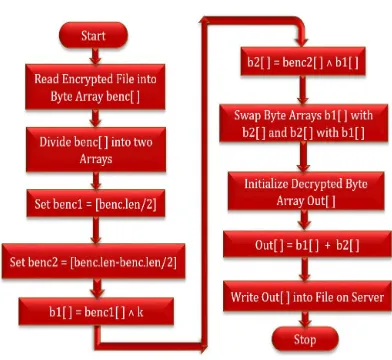

Related documents
The characteristic polynomial of k Trivium-like shift registers in coupling connection is proved to have a factor of (1+ x ) k. So k -order primitive polynomials are defined
The following literature review will consider writing on authentic learning, the arts, different forms of theatre and drama experienced in schools along with: the production for
The GCE A level aggregate score, used as the only measure of academic performance for medical school admission in Sri Lanka, appears to be a weak predictor of performance in a
To measure real earnings management, I rely on two of the proxies of Roychowdhury (2006): abnormal discretionary expenses; and abnormal production costs. In order to
The present study is aimed at investigating the effect of the self-regulatory policy of auditing profession and its influence on standard setting and audit expectation gap (AEG)
the third Era of the State Architectural Style, under the rule of Ameer Muhammad Bahawal Khan Abbassi V (r.1899-1907), managed to introduce a unique architectural vocabulary in
Contreras AL, Malpica A: Angiosarcoma arising in mature cystic teratoma of the ovary: A case report and review of the literature.. den Bakker MA, Ansink AC, Ewing-Graham PC:
The primary purpose of the current study was to determine whether a text message intervention would increase break frequency and length of break from sitting, time spent standing,