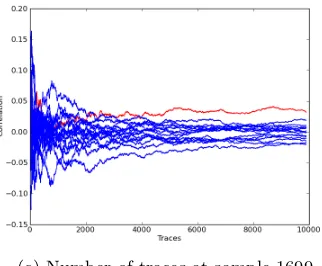
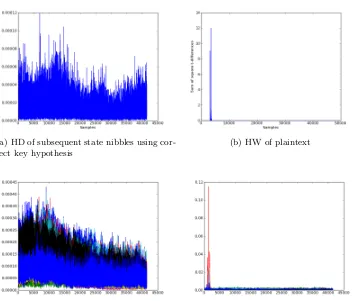
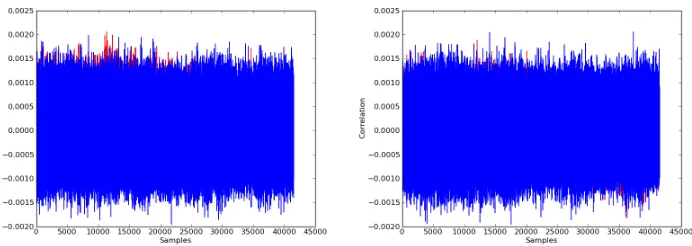
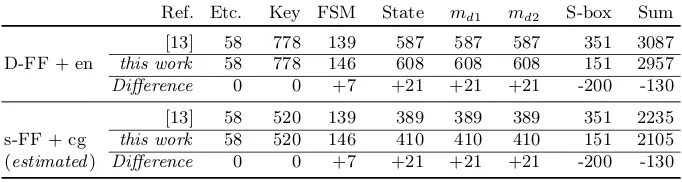
On 3-share Threshold Implementations for 4-bit S-boxes
Full text
Figure
![Fig. 1. Decomposition of an S-box [13]](https://thumb-us.123doks.com/thumbv2/123dok_us/7886609.1308569/4.595.136.477.354.442/fig-decomposition-of-an-s-box.webp)

Related documents
During the thesis work, I measured six different parameters: the number of emergency processes, hash table entry number, caching replacement policy, cache entry
• For a home purchase loan, a refinancing, or a dwelling-secured home improvement loan that you originated, report the spread (difference) between the annual percentage rate
Most algorithms for large item sets are related to the Apri- ori algorithm that will be discussed in Chapter IV-A2. All algorithms and methods are usually based on the same
Here we describe a novel point mutation of an intronic splice acceptor site which results in a complex splicing defect of the CD40 ligand in a patient with XHIM.. In addition to
Make changes to section on agreements to reflect emphasis of agreements in new
To aid preparation and the appraisal discussion appraisees and their appraiser have a snapshot of the period since the last appraisal which shows the following details recorded on
Handling and cleaning the screen surface/ cabinet of the TV set Be sure to unplug the mains lead connected to the TV set from mains socket before cleaning. To avoid
A metadata volume contains information specific to a VPLEX Cluster such as virtual-to-physical mapping information, data about the devices and virtual volumes, system