Faster Cryptographic Hash Function From Supersingular Isogeny Graphs
Full text
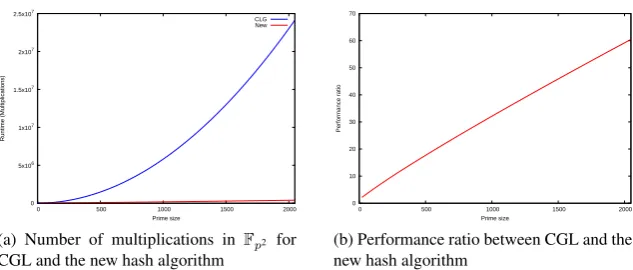
Figure

Related documents
Objectives: To describe the school feeding practice in Nigerian schools and relate the contents of their lunch boxes to risk of having dental caries and determine the
The comparison of bound coherent and bound incoherent scattering cross section for Si and C atom is shown in Table 1.. Bound coherent and incoherent scattering cross section for
Figure 2 compares the prices of 18Ne and 10Ne ring spun yarns (again from 1984 to the present) with the difference in yarn price due to count also being included. While there
Runt and Top Grade liver histology striped bass full data set (N=71 fish) hepatic somatic index versus average steatosis scores. One liver weight was accidentally not collected
Because of fragmenited ins ti tutional arrangements and site-specific conventions of design, the network of urban streams suffers from lack of comprehensive
Factors from employee performance consists EMP as employee performance whereas as factor for different motivational factor consists OC as organizational culture, WE as work
The six antigens described here (the 38-kDa antigen, Mtb8, Mtb11, Mtb48, DPEP, and Mtb81), several of which are incor- porated into the polyproteins TbF6 or TbF10, provide the basis
To develop a system that provides data security in Cloud based IaaS services using encryption algorithm and compression algorithms... Papers presented in