Security Algorithms for Privacy Protection and Security in Aadhaar
Full text
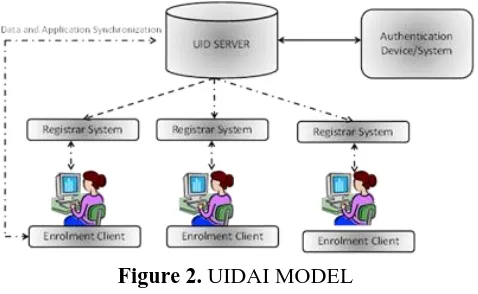
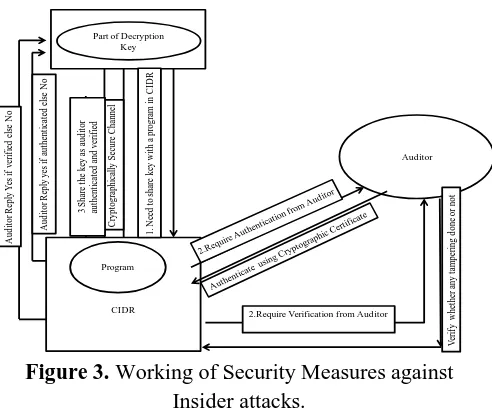
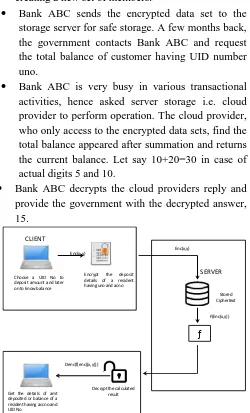
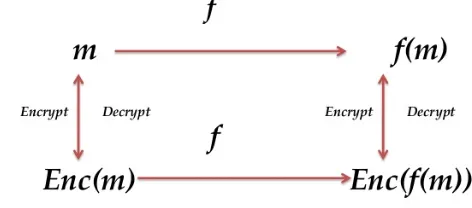
Figure
Related documents
Comparative analysis of CDS between growth in dextrose and LC-FA showed that majority of genes had similar expression lev- els, both at exponential and stationary phases (see Fig.
Interestingly, when FK506, the inhibitory com- petitor for FKBP12 was added together with sirolimus to the bac- terial cultures, the emission of BRET signal was arrested, which
ducreyi inhibit phagocytosis by stimulating the catalytic activity of C-terminal Src kinase (Csk), which itself inhibits Src family protein tyrosine kinases (SFKs) that
Through a combination of bacterial gene regulation and phenotypic studies, plant infection assays, and plant hormone quantifications, we now report that Chp8 (i) is embedded in the
The majority of the subjects in this study were from the border towns ofKelantan and 44.3% were from Kota Bharu itself This can be partly explained by the fact that the Drug
Since a high proportion of the subjects were intravenous drug users (80.0%) and sex workers (77.7%), both factors could be operational among these subjects to produce
Considering that the Chinese have been reported to prefer private medical services 5, they form the largest number of drinkers, i.e., compared to the Indians and Malays who
We examined viruses from planktonic saliva and from subgingival and supragingival biofilms to determine whether there are significant differences in viral community membership by