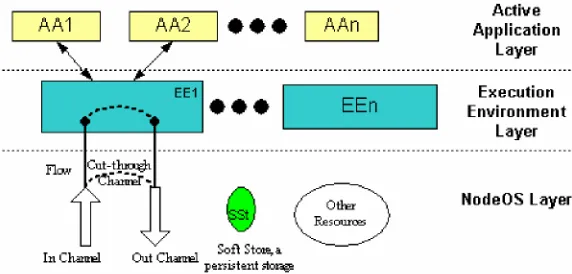
Integrating security services into active network
Full text
Figure

Related documents
Hypothesis 4b: Increased levels of organizational constraints aggregated to the unit-level (Level 2) will be associated with individual-level (Level 1) decreased supervisor-rated
Although both trajectory clustering and segment clustering compute a sequence of segments from a sensor stream, they are different in the following way: Segment
The BSA E-Filing System has identity and authentication management controls, access control, role based security, access auditing, network security and security zones implemented
1777 First Thanksgiving proclaimed by national authority (Continental Congress) for all 13 states on December 18 (many states had individual Days of Thanksgiving earlier that
Color Image Reader Unit-B2, Printer Cover-C1, iR Pedestal (New), Inner 2way Tray-F1, Inner Finisher Additional Tray-A1, Buffer Pass Unit-G1, External 2 Hole Puncher-B1, Copy
Each year, FastCasual.com hosts the Fast Casual Executive Summit – a live business networking and social event where Fast Casual restaurant executives meet up to exchange ideas
In alignment with our findings where the most important service quality dimension was tangibility (physical facilities, equipment, and appearance of personnel)
However, these points are not reliable enough to be used in ICP registration if the capture points are far from each other because two possible sources of errors exist: errors in