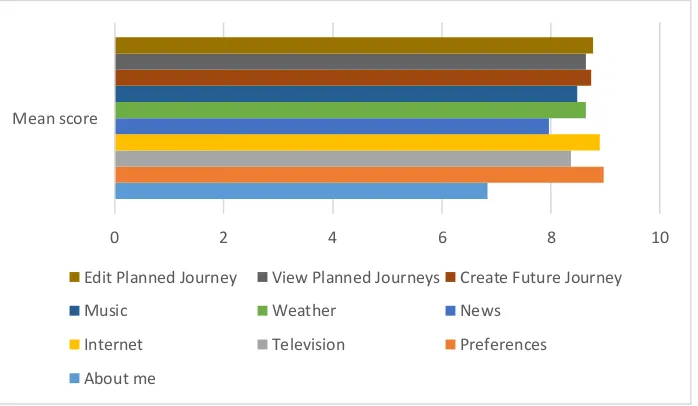
Investigating older adults’ preferences for functions within a human machine interface designed for fully autonomous vehicles
Full text
Figure



Related documents
The proposed approach jointly estimates the non-rigid transformations necessary to register an un- biased mean template (represented as a 7-dimensional hybrid point set com-
With respect to problem behaviors, SSRS parent ratings of students enrolled in full-time, online public schools were significantly lower than national norms across the
Another well known model of risk management is the RISKIT [11], that incorporates a similar process to that proposed by Boehm [3], including the following stages: (a) definition of
Actually, the problem of the “Finding minerals in hyper spectral images is too tough” emerges when a statistic-based classification method is applied to the hyperspectral data..
Our admission control policy for access to processor resources balances the needs of the three classes of tasks: throughput and maximum delay requirements of the real-time tasks,
In this paper, we proposed a novel Contextual Attention Recurrent Architecture (CARA) for Context-Aware Venue Recommendation (CAVR), positioned within five elicited limitations
transient receptor potential vanilloid 1 (TRPV1) channels by negatively charged intracellular lipids: the key role of endogenous phosphoinositides in maintaining channel activity,
We need to have a robust cyber space - our government, businesses, LEAs, residents, etc, must build capabilities to address the challenges of cyber security through development