Fast Remaining Thickness Measurement Using a Laser Source Scanning Technique
Full text
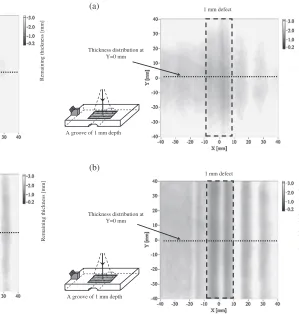
Figure



Related documents
Although the continuum of care has recently been highlighted as central for reproductive, maternal, newborn, and child health (RMNCH), and a means to reduce the burden of maternal
1997-99 Assistant Professor of Finance - School of Business & Economics, Wilfrid Laurier University, Waterloo, Ontario.. 1992-96 Assistant Professor of Finance, School
Writers have suggested increasing the gross private cost graduates face for their education either to: (i) increase tuition fees to give universities more funding to presumably
The minor groove of helix 69 of 23 S rRNA, which forms bridge B2a, interacts with the mi- nor groove of the D stem of P-tRNA (Fig. 6E; interaction g), extending into the A site
All pieces of information collected in the previous phases can be stored in a Working Matrix (see above), typically in one of the software tools already mentioned. Then it
Furthermore, this thesis use the practice of SINOCHEM carrying out comprehensive budget management for reference to illustrate that a good comprehensive budget management system
This comes to a strategy called: Aggressive strategy, which suggests that sub-orbital transportation has highly possibility of becoming efficient emergency response
JME technology provides integral mechanisms that guarantee security properties for mobile devices, defin- ing a security model which restricts access to sensitive functions for

