http://wrap.warwick.ac.uk/
Original citation:
Pu, I. and Gibbons, A. M. (1996) Matricial space-economy with constant access-time. University of Warwick. Department of Computer Science. (Department of Computer Science Research Report). (Unpublished) CS-RR-303
Permanent WRAP url:
http://wrap.warwick.ac.uk/60987
Copyright and reuse:
The Warwick Research Archive Portal (WRAP) makes this work by researchers of the University of Warwick available open access under the following conditions. Copyright © and all moral rights to the version of the paper presented here belong to the individual author(s) and/or other copyright owners. To the extent reasonable and practicable the material made available in WRAP has been checked for eligibility before being made available.
Copies of full items can be used for personal research or study, educational, or not-for-profit purposes without prior permission or charge. Provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way.
A note on versions:
Research
R.port
303
Matricial
Space-Economy
with
Constant
Access-Time
Ida
Pu.
Alan
Gibbons
RR3O3
We describe a particularly simple and practical algorithm
for
economic storag.e of arrays withoutrecourse to the
intricaciei
of perfect hash functions.This
is donewhile
retaining constant accesstime.
The algorithm
performsusefully
over a rangeof
valuesof
x/n
where the notional inputarray contairis
n
entiieswith
x
non-zero elements. Forx
less thanor
equalto
n/k
and oneparticular
settingof
thearray
parameter, we show that the average storagerequired
is
about n (t< +ZO)tl0ft.
For sparse arrays this becomes n/lO.
Department of Computer Science University of Warwick
Coventry
CV4lAL
United KingdomMatricial
Space-Economy
with
Constant
Access-Time
(DRAFT)
Ida
Pu and
Alan
Gibbons
.
Departrrrent of Computer Science, Universitl' of Warwick,
flI{
Abstract
We clescribe a particularly simple and practical algorithm for econonic storage
of arrays rvithout recourse to the intricacies of perfect hasli functions. This is done
rvhile
retaililg
colst,ant access time. The algorithm performs usefuliy over a rangeof values of
rf
n *,here the notional input array coutaius n entries rvith e lloll-zeroelerrelts. For
r (
nfk
and one particular setting of the arral'parametcr. rve sitorvthat the a.verage storage required is about, n(fr + 30)/10[, where n is tire nutrlber of locations of the notional input array. For sparse arra)'s this drops to about n/10.
1
Introduction
In maly
programming applica,tions involving sparse matrices, there is the poterrtial forspace econony
in
matricial storage. For exa,mple, we could storejust
the non-erupty (ornon-zero) elernents along
with
their original rnatricial indices.It
rvould then be atlivial
matter
to find (that
is,
access) any matricia,i element. givenits
indices,in
logarithmic sequentia,ltime
using standarclbinary
search.The penalty
to
be paid
for tlte
space-economyof
suchan algorithm
is
the
lossof
constant access-time.In
this
paper wedescribe
a
particularlv
simple anclpractical algorithrn
to
achieve space-economl' audat the
sametime retain
constant access-time. Moreover)our
deterrninistic sequentialalgorithm cloes
not
have recourseto
the intricacies of perfect hash frrnctionsIf].
Apartfrom
[1], we have been unableto
find
any referenceto
the
problem addressedbv
thispup"r.
The algorithm treats theinput
as thoughit
rvas a one-dimensional al'raY.Trivial
changeswolld
readily vield an algorithm for rna,trices of arbitrar.v dimensiols.In sectiol
2 we clescribe our sirnple algorithm.In
section 3 we obtairt an exa,ct exptessionfor the average storage requirernents of the algorithm and rve qua,ntify this
lbl
a pa,r'ticuiarvalue
of
a1 algorithmic para,meter. Thefinal
sectionis a sunlmaly t,f ottr
results a,nclconclusions.
cs.warwick.ac.uk.Partiallysrrpportedt;vtheEC-]ALCoN{-I,f
2
The algorithm
Imagine
that n
input
items occupythe
loca,tionsof a
notional
arravINPUTI1
'.
?]]a1d
that
there areL
noll-zero elernents. Ouralgorithm
constructs a cornplesseil all'a\'.COMP. ancl
an auxiliary
array,AUX[1..f,1..2].
The
arrays CON'{P andAUX
occupva,vailable stora,ge space rvhereas the elements of
INPUT
are merely sequentially sc.annedby
theinput
device. The elementsof
COMP includethe
non-zero elements ofINPIIT
and the elements of
AUX
allorv any element ofINPLiT to
be deducedin
colstant
time.The array
INPUT
is imaginedto
be dividedfron
the
left
into
equal sized segmerrts oflelgth
swith
(if
sis not a
divisorof
rz) afinal
smaller segment oflength
n-
-sln/-sl. We definethe
t
in
termsof
s,f
:
lnls].
In
general any such segment ofINPUT
willcontain a
nlmber
of leading andtrailing
zeros(or
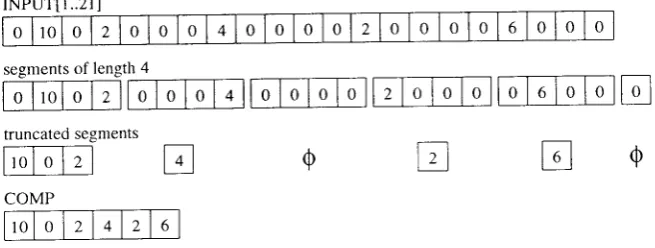
empty elernents). We delete these auricolstruct
COMP by concatenating the truncated segrnents. Figure 1 shorvs an examplefor n
=
21 and s:
4.
Here the array COMP has iength 6'rNPUTI1..21]
0
l0l
0 2 0 0 041010
0 0 2 0010
0 6 0 0 0 segments of length 4 [image:4.595.130.458.322.446.2]6T-'.r-.[f
FFFr.lFFl
[,-t;FF.lFFftF-1tr
Figure 1: The constructiori
of
COMPIn
geleral
rvemight
expectthe length
of
CONIPto
be
nruch lessthan the
lcngth ofII{PUT
especia,Ily,for
example, whenI
is
closeto
r'.
In
this
case manY untrtrncateclsegnelts wil1, on average) contain only empty elernents or exactly one signif.ca,nt elernent.
In
both
cases segtnent truncation does not force the storage of non-significant eletnents ofINPUT in
COMP.The
poteltial
for
space-economy to be had from storing COMP ratherthal
INPIIT
canbe achieve<l rvhile
retailing
constant access-time as we ltow see. Given J we a,re recFriredto
deduceINPUTUI
from COMP by making use of the arrayAUX
which we now defiue.For 1
(
i
<
f , AUXId, 1] is the address of thefirst
elernent of theith
truncated segrnentin
the arravCOMP
(if
the truncated segrnent is enrpt\'. tirenit
is tire atltlress of rvhelesuclr a1 elernent utonld have appeared) ancl
ALlX[r.2] is
the nurnber of leacling zeros inthe
ith
ult1lncatecl
segment.If
the segmentcoltains
onlv zeros) thenthet'are
<or-rntetl a,s ieacling zeros. Figure 2 showsAUX
for the example of figure 1.The algorithm
FincIINPUT[7] clescribecl belorvreturns
thc
valueof
thejth
eltrrnerLt inthe ima,gined array
INPUT
giventhe
all'avs COIvIP andAUX'
In
AlgoritlLmFiDilINpUT[-l], h is the
nurnbcrof the
segrnent frorrrthe
left
<:ontainingINpUTU]. alcl
/
is the
acld.ressof INPLITIj]
in
the
uncompressetlarrav
relo,ti,ttr: tr'ttruncated seg
--r-T----l
I ro | 0 I 2 |
COMP
0
a
A 5 o 7
[image:5.595.185.402.353.484.2]3 A 0 I
Figure
2:
Thematrix
AIIX
for
our examplebeginning
of
the segm,ent conta'iningINPUTU].
NoteAUXIh +
length
of the
truncated
segmentand the length
of the
AUX
irnplementation, where rn is the number of segments.
For each segment
of length
s,
d, the
offsetof
the
the
distancefrom
INPTITI7]to
thebeginning of the the uncompressed segment containing
INPUTU],
canolly
bein
threeareas,
i.e.
0S
rI1
nltz, rvhere nhz is the number of the leading zeroslor nhz<
d<
nhzl
nl
wherent
is the the length of the truncctted segm,entor
nhz*
n,tI
d(
-t. The nurnberof
leaclilg
zerosin
th.e segmentis
storedin
AUX[h,2]
and the lengthof
the tnrncated segmentis
actuallythe
difference between the addressof
COMPfor
thefirst
non-zero element of the segment and of tire following segment,i.e.
AUX[h+
1, 1]-
AUXIh, 1]. A11this
isillustrated in
fieure
3.I I
d<AUXth.2l
r
length of truncated seg.t
1: no. of-
;
AUXIh+1,11-AUX[h,l]
'trailing zeros
ri
I
d<AUXlh,2l+AUXth+ 1 ,1 l-AUXth, I
I
I-=__l
Figure 3:
The algorithm
rnay be implementedin
different wa.vs. We asstrme a block stnrctured stylein
which arrays ma,y be dynamically declared. The implementation rvould be more elegantly expressedin
a langirage which allowed for d1'lamic extension of arrays.Within
our
self-imposed style. rve needto
readin
the data trvice, althoughthis
canlle
a,voidedby
an a,lternative style.Algorithm
Construct
readsin
the data
sequenceand returns
the
compressed arravCOMP
a,ncl auxiiiar'\, ar'r'a,yAUX.
rvherc' AUX[1..nr+
1, 1] containstire
a,rldresses iuCOMP
of tirefirst
non-zero elernent of ea,ch segment and AUX[1 ..m,2) stores the nrrrn-ber of leacling zerosin
eaclL segrnent. AUX[nrf
1,1] stores tirenext
acldre'ssto
the Iast address of COMP.Lile
2 i1p1ts
thelength
of
the
input
sequencesand the length of the
segurents Line3
compltss
thc
numberof
segments.Line 4
clynarnically declaresthe
a,lrxiliarv arrayAUX.
The algolithm
Construct
dealsrvith the data
seqrreuceby
seplnents.
In
eachseg-nelt
(lines
6-
21),
it
storesthe
addressof
the
first
non-zeroeleruclt
irt a
segulent1,11
-
AUXIh,1] is
thein
AUX[1.. m|
1,1] (Line 8),In
line 9-
2I k
counts the leading zeros and/
counts thetrailing
zeros. The lengthof the
truncated segtnentis
q(Line
19) and p isthe
a,tldressin
COMPfor
the fi.rst non-zero element of the next segrnent (Line 20).Line 25 dynamicaliy decla,res the array COMP. Lines 26
-
37 read the data, at the secondtime.
T[is
elters
the tluncated segmentsinto
COMP.That
programme bod-vin
rvhich theinput
isto
be manipulated is imagined to be contained betrveen Lines 37-
38. Thisis
within
the blockin
rvhich the required arrays have scope.Algorithrn
l'indlN PUT[j]Input:
7Output:
INPUTU]I
begin2
h=
[t.l,d=U-i)
rnods
3
itd
<Atrx(h,2) or
d>
AUX(A,2)+ AUX(A+ 1,1)-
AUX(h,1)4
then
INPUTUI:
05
else INPUTUI:
COMPIAUX(A,1)+ d-
AUx(l]' 2)l6
endAlgorithm
CorrstructInput:
input data sequellceOutput:
array.CON'IP ancl AUX1
begin2
read n, s3 ,, :
[3'l4
array
AUX[1..(rn+
1), 1..2]5 p*
16 fori:ltorndo
7
tregin8
AUXIi.1]-P,k-/-0
9
forj=ltosdo
10
begin11
isHead].-
true
12
read input(i.e.INPUT'[(;-
1)s + -rJ)13
if (input=0and
isHead?)thenk-fr+1
14
else isHead}-
false15
if
(input=
0 and -isHead7)then/
- /+
I16
elsei-0
Il
eno18
AUXIi.2]-
r'19
Q--s-(k+/)
20 p-f)+q
2l
end22 AUX[rrr
+
1.l]
-
?r23 end
24 begin
25
array
C:ONIP[1..p- 1]26 p
*
1.restart
read28
begin29
for
j
= I
to AtlX[i,2]
do read inPut30
for
7-
1to
Atlx[i +
1, 1]-
AtlX[f, 1] do31
begin32
read inPut33
COMPhrl-
inPut34
p*PIl
35
end36
for
j
= 1to
s-Atlxli,2]-AUXId+
1,1]+ AI-lX[t,1]doread
input37
end38
."
L.."*t"-tt"
body employiug calls FindINPUTU]39 end
3
Expected
Space
EconomY
In
sectiol 3.1 weobtail
a1 exact algebraic expressioir for the expected lengthofthe
alrayCOMP.
Thel i1
sectiol 3.2,for
aparticular
choice of the variable s. we derive a siurpleexpression
for this
average which nevertheless providesa
closeapproximation.
Tiris isconfirnecl by a conparison itetween plots of the exact and approximate expressions. The
particular
choice of .s=
n fr
is shorvnto
provide a,n algorithm rvith good space ec:ollolrlyfor
sparse rnatrices.3.1
The
average
length of
the
array COMP
We prove three Lernnas rvhich
ultimately
provide an exa,ct expressionfor
the
average length of the array CO\,{P. Given a one-dimensiona,l ari'a.\'segment of iength s containiugk
non-zero elemelts,bv A(,s,k)
we denotetlte
auero,ge lengthof
the reducecl scgmentobta,ined by removing those segment locatious containing leading anci
trailing
zeros. Thef,rst
Lemrna derives an expressionfor
A(-s, A).Lemma1-
For
1(ft(-q.
r(s.r,
t:"(=)
*
('+)
\A.+
1/
\A'+
1/
proof
clearly A(-s.A)(i):,SUni(-s,k)
rvhere,Surn(.s.4)is tire
sumof
rc.clu<:ecl segrnents of all possible distributions of the nol-zero elements over
segrneut. Norv
s-A
Srini(.., k)
=
t(A'+
i)(s
-
(k+
t)
+
1)(ufl;')
i=0
the the
lengths o1 unreihrcecl
because a, reduced segment of length (fr
+
i)
can resideat
(-s-
(k
+
t)
f
1) positrons rntlre segment a1d
in
anv one position there mayA.
(kt1;2
)
segnelts
of thislength.
Wesimplifv this
expression byfirst
taking the surn variablei
completelvinto
the binomial coefficients as follows:(A
+
i)(,s-
(a+
t)
+
1)(ufl;'):
s(k+
x)(k[:r'z )-
(a+
iXA+
t-
lXot-:;')
bnt
(fr+
txk
+
t
-
1)(u[:;'):k(k
-
rxuf')
ancl (A
+l([:;2)
:
(a+t-
1Xu[5')+(r[:;'
):
(A-
lxufll')+(kl:;')
Combining 2, 3 and 4
rvith
l:
s-l s-A s-A
-
A.(l..- '"\,"rt
^t Zr.irlrl't
I (5)r=0
(2)
(3)
(4)
sunz(s, k)
:
s(A-
1)t(nl:l'
)+,
f(
utl;'
Ii=0
i=o\\ie
use the stanclard results:a
\-rlt:
?-,"'
To sirnplifv 5. rve note trsing 6:s-A
(?i11) and
(:
)=
o,if
b<
n (6)lr
r.ittl
):
/r\ N- | r=O
s-A
\-r^'i':2
) =/J' N-z
i=0
s- I
|
{n1,)
J=A- I
(i-l)
a'cl
s-l
-\-r,"/-t-rft
/J,R-t / \N/j=o s-k
\-r('i,r:r.i+1
r/r\ k / \A'+1 /
r=O
(7)
(8) Similarlv:
From 7, 8 anci 5:
strnr(.s,k)
=
s("
-
1)(i)
+.,(;-i
)-
k(k
_1Xi+i
):
(i
)!+#
"+) +
f+)
rvhich is rvirat wasto
be provecl. Noticethat
the proofThrrs
--l(s.A'):..
(t*,;
\^t,,/
is o1ly valicl for s
S k
{
2 because equation 1 wasrvritten
downol
tiris basis. Horvever, rve notir:t:that
the formula gives A(s,k)
=
1 rvhich happensto bc
valid'
If
k
:
0 thcriclearly
A(.s.k):0,
rvhereas the formula, gives(-s).
Compensa,tion urust tirerefore bemacle
for
this factin later
clerivatiols offorrnulas.
nThe
forltula
of the previous Lcruma has been numericallY cirecked for alumber
of cascs.Rrr
exarnple.it
is easl'to
chec.k fromfirst
principlestirat
A(5, 3):
'l
rvhich is rvhat theforrnula also gives.
\\ie
nrirv ernplor.lesult
of Lelrlna
1to fild
an exact expressitxrfor,-lur:(n.r,-s)
rvhichclernotes t,\e rnterage,lelgth
that
the array CONIP rvouldattain
giventhat
INPUT[1..ri],Lemma
2
If
s
is
a diuisor ofn,
thenAue(n.r.s):
'
I
f(,'+2)_ra+)
"
L\'
-.r*r/
uthere
il
=
flf=Or(1_
;=): (""")l(:)
Proof
Clearly
Aue,(n, r:. -s)(l)
:
Sum(n,r,
-")lengths over reduced segments over
all
possibleover the array
INPUT[1..n].
Wefirst
show thatsrr,r(rr.
r..s)fnt
:
'"'f^"',;X:--;)(t'+':r
t#)
+ s(";"
)A =t,
where
Sum(n,r,-s) is
the
sumof
thedistributions of the
rlon-zero elements+,'
("
+2
rr-
s-.rVl
-
ll
.]'+r
/J
m in(r, s )
'l s- u srrfl-sr rr I
Stnn(n,
r,
s): : L
(i X:l-i
)A(.-,A')
(9)o a=l
If
-s is a d.ivisorof n
then there are exactlyn/s
segmcnts. Wecolsider
horv thec
lloll-zero elements are partitioned these segments. Cousider the contribution to.9trriz(rz,r,-s)
from
all
distributions rvhich place &; nou-zero elementsin
theith
segment' 1(
i
<
?\Arriting rn,
:
2,
this
contribution is given by:(r', Xu",
)'''(*"-
)(A(-', /'1)+
A(s, A'z)*
''
'f
A(s, ft',,)) (10 )because.
for
each f.xed internal arrangement ofki
non-zero elernentsin
the tith segnentall possible
ilterna,l
arrangemerrts ofk;
non-zero elernentsin
al1 the 7th segrnents(i
t'
j)
occ1r. Weobtain
ecpation 9by
summing expressiou 10 over all possible pa,rtitions aurlusing the identity:
(a",
)(o',)
(a';):
('r;)
htbz+"'*bi
01
bi(
min(r,
s), 1Norv
slbstituting
for A(s. &) from Lemma 1, and taking accorrnt of the fact (noted at tireencl of the proof
of
Lemma 1)that
the expressionfor A(s,0)
needsto
be corripelsatetlfor.
we obtain:-b
<i<j
rnin( e', s )
=
(-.+2)('])_
z(,+
1)
t
(;X:l--;)# +.,(",")
(11)t'=0
But ,s, 1 1 rstl r
trt-=-tt.rr,
and
rnin(r, s )
\-
ri+l
rr"-f
r-/_ \ A.+1 /t rL t
-ft=0
So
SrLtn(n,t,s)fm
)+1
("j'xr"iii-, )-
("t')(:;i):
(.:+l)-
(:;i)
(.s
+
2)("1)+'(";"
)-
2(( :111 )- (:;i
))now
rnllr n{1,tt
\r*t/
.r+1,r,
and so we
finally
obta,inS'urn(n,rr,
s)/(nr(l))
:
((" +
2)-
21+
)*
(.-*
frorn which the result follon's immediately.
The
formlla
of Lemma 2 ha,s been indepenclently checked for a number of specific cases.Note tlrat rve obta'in Aue(n,1, s)
:
r,
Aue(n',r,2):
r
alcl Aue-(n''2'nl2): +F+4*I
rvhich are easily proved indepenclently.
Space
permitting,
we could lo.lv have combinedthe tn'o
previous Lemmasto find
au expression forAue(n,r..s)
which isnot
subjectto the
restrictiouthat
-c be a divisor of?1.
This is
reaclily cloneby
treating the
array INPLT
a,s consistingof
tlr'o parts. thelrrst
oflength slnl.s)
anci the second of length n-
-s[n/,s]. Thefirst
rnay then handledtirro.gh
Lenna
2 ancl second througir Lemma 1anc1combiletl
to give thc'desired result'Horvever, the
resllt
is suffrciently similarto
that
of Lemma 2for
usto
be content iviththat in
the space available.In
any case Lemma 2 is sufficieut for the algorithmic analvsisprovicled.
i1
section3.2.
For completenesstlie
follorvirtg Lemma does provide a, botrnclorr -{r'r (n..r'..'.1 witlL no lest,rictiorrs on the palanloters'
Lemma
3
For
anltr,s
such that 0 Sr'-s
(
n,r(r, s
\-
/J (13)J-l
r , li-s , , rt ' T- 's
and (",")=(:1
)ll(1 --
,),ju
r?-r
-n_
Aue(n.r,.s)<
l-l
,)
.[]''l +
1\
/
+2)-::Lql||+"{'+:
.r.+r /
\
r
"f?l-'
171'f?1 1.\ .r tt' f,'
J-l
// -.\ -.l n .a ,,
l
.r'+ I_ )ll(1--l
i- ll-lI =t,
n
r\
l-5-jD\
--
|.r+r
/
[(,,
s \_ st-t-l
.'lrl
-l€ s |-.s
-uthere.r
=
fl,l=1(1-Proof
\Ve observe that:Aue(tt..i'. s)
(
Alr
(.'lf
l.
,-..t
If
.s is a divisor ofz,
then erlua,tion holds. Otherrvisc ri'e rtotethat
for each arrangeruetttof non-zero elernents ovcr
INPUTll..n]
il
rvhich there alerat
least trvo such elernents inthe final
segmelt, there a,re alra,ngements overINPt-T11...[]l]
for
whichall
non-zt'ro elernentsin
the
first
lll
segurents are identically allangerllxrt
over thefinal
segmentnay
5e arrangecl to prorluce larger reducecl segrnents. NorvsIt.l it
divisiblt:bv
c an(l so3.2
Quantifying
the
storage
requirements
Here rve show how setting s
=
nlr
provides an algorithrnwith
effective space ecollorny.For
techlical
clarity
weshall
assumethe
formulaof Lemna 2
althoughit
shorrld beclear
that
the
arguments used here would obtain essentially similar resultsif
-s was notrestricted
to
be a divisor of n.Note
that
whatever the values ofn
ancl z,if
.s(
2 the algorithmrvill
give a length of .rfor
the array COMP whichis
optimal.
Tiris
follorvsboth
frorn Lemrna, 2 and frorn theobservatiol
that
uo non-zeto elementsof
theinput
rvill
bervritten
to
CONIPfor
sut:hsmall valles o{ -s. On the a,verage, the
total
storage required by the algorithm is, rvithiuasmalL additive constant,given by
Aue(n,r,..)*2i.
The secondtermis
what the arrayAUX
neecls andfor
-s=
nfs is
2r.
Of
course,z
providesa natural
lorver borrnd forstorage recluired for the problem considered
in
this paper.Rewritine the formula of Lemma 2 and replacing -s
rvith
nf :t, we obtain:2t:n (1J)
Aue(n,
r,
s)-r+1
\Are neecl
al]
upper
boundon
a
to
get
a'uupper bound
for
Aue(n,r.-s).
Herect
:
fli=ot(I-
y)
<
(f
- ])''
l-e-1. If
r )
35then,'ivithin
I%,a
is
closely approximatedby
r-t.
For such va,lues of r; rvefurther
takeH
=
3.
.#
= 2r
ancl2* *
2.
It
then follorvsthat:
Aue(n,e,.s)
=
2n- (1-
e-';(3rz
-
2:t):0.1037rt
*
1'.2642r (15)where rve have taken e
:
2.71828.Taking
-r:
nlr,
the above alalysis shorvsthat
rve have an algorithm rvhich uses (takirrgthe recluirerlelts
of Arte(n,r,nf s)
andAUX
together))about
,s!+
3,,' space'This
isconfirmed
by
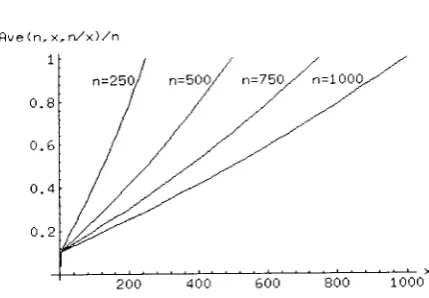
Figures4
and5.
Figure4
plots
A'ue (rr,t,nf
s)fn
aga'inst:r
for
various valuesof n
using th.e eract expressionfor
Aoe(n,r,n,f
s)
givenbv
Leurma2.
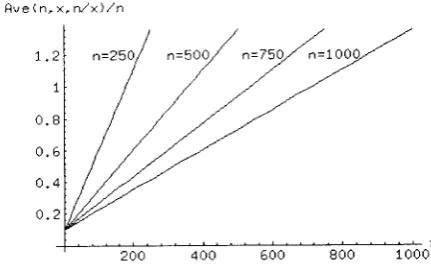
Figure 5provides
the
sa,me plots using the formula of ecluation 15for Aae(n,:t,nf
s).
The similarity
betrveen these figures is rernarkable, particularly for low values ofr.
This providesadditional confidence
for our
claimthat
we have described,for
sparse rna,trices (rvhercn
)
r),
an aigorithm rvhich ot1 avera,ge uses a,bout I0% of the space recluire'ment of theinput
data,.4
Summary and concluding remarks
\\re have describeil a particularll,' sirnple a,ud practical algorithrn
for
t:conouric storage ofarrays
without
recourseto
the
intricaciesof
perfect hashfrrnctions. This
rvas rlone atthe express
intcntiol
of retaining constant a,ccesstime.
The algoritlLm performs usef\lll1'ovef
a
ralrgeof
valuesof
t:f
rt.
For
r I
nf k:,tht:
average storagtlrerpired
is
aboutn(A'*
30)/10i:,
rvhere n,is tire
tiumbcl
of
locationsof
the uotional inPut
trrrav.
Forsl)a1sp irl'Lavs rhis dt'ops ro alrorrt rr/10'
E
Mathematica Graphics: out[7]ffi
U
[image:12.595.187.402.161.310.2]Ave(n.x,n/x)/n
Figure
4:
Plots obtained using the exact explessionfor
Ave(D,x,n/x)\\re
obtailecl
an exact expl'essionfor
tlie
avelage stol'age requirements of the algoritiLrnancl rve c1ua1tificc1 this
fol
a particular value of the parameter s, rtamel-v rvhen .s:
rt l.L-It
is
1ot at all
clearthat
this particular
choice proviclesthe
best performa'ncefol
thealgorithm
althoughthis
choiceis
certainll'uscful. Fultirer
investiga,tions ale l)ecessal\'in
this regard.. \Ve rvould also like to know rvhat the clistribution of thelelgth
of CON'IPover
c
lookslike.
Whetheror not
it
is
sharplv peaked aroundthc
average value is not known.Although economic, the average storage space requirecl by the algorithm is seeruiuglv a
fractiol of
n. It
wo1]cl be preferableif
this
was replacedby a
constanturuitiplc
of
rrwhich provides a natural lower bound.
It
is unclear rvhether an algorithrn as simple and aspractical
as ours can achievethis.
It
certainly
seeulsunlikely
within
the
a'pproachtaken
in
this paper.
This is
because there aredistributions of the
non-zero elelnentsrvhich force a clependence of the length
of
COMPolt n
evenif
additional stlategies aleallowed.
One srich strategymight
employthe
slidingof
the
imposedgrid
along thenotional arrav
INPUT
so asto
minimise the lengthof
COX{Pfor
any particular input.Tiris
strategy cannot avoirlthe
dependenccof
the lengthof CO\{P
on
n
becausr'. ft'rrexalnple,
the 1ol-zero
elerrrents rnay beuniforrnlv tlistributed
at
separating distarlces<tf
.sf2.
For
s: rr/r,
this
guaranteesthat
ca,ch rrulecluccd segruent occupie<lllv
tu'oelements
contribltes
rr/22 elcrnentsto
COIVIP. Other choices of s rnight avoidtlis.
ffi
Mathematica Graphics: out[13]ffi
g
Ave(n.x.n/x)/n
I.2l n=
1
0.8
0.5
o.4
[image:13.595.183.399.174.309.2]o.2
Figure
5:
Plots obtained using the apploximate expressionfor
Ave(n)x,n/x)5
Acknowledgements
\A,'e
thalk
S.
\{uthukrishna,n whose conversation (perhapsunrvittingly)
initiated
theencluiries of
this
paper.References
[1]
Fredman and Komlos and Szemered,"storing
a Sparse Tablewith
O(1) \\rorst CaseAccess Time"
,
Proc. 23thIEEE
Syntposiuln on Foundationsof
Conzputer Scr'ence(FOCS),1983. 165-169.