Mobile Node Security in Wireless Sensor Networks using Three Phase Authentication Scheme
Full text
Figure
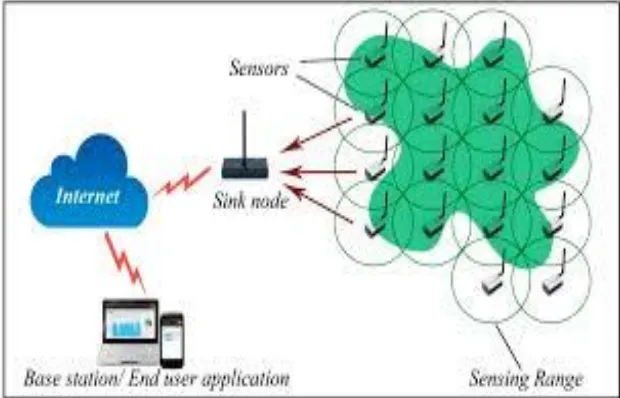

Related documents
As inter-speaker variability among these the two groups was minimal, ranging from 0% to 2% of lack of concord in the 21-40 group and from 41% to 46% in the 71+ generation, we
Considering a range of tax and benefit systems, particularly those having benefit taper rates whereby some benefits are received by income groups other than those at the bottom of
Video Heroes, Saidye Bronfman Centre, curated by Sylvie Gilbert and Gordon Hatt, Montréal, QC Lost in space screened as part of Recent Canadian Performance Video, at Split
Here is the beginning of that hard-driving eighth note time and get down playing style that we associate with rock music today.. To play this style successfully
We all have areas in our lives where we feel stuck, at least one area that we cannot change, but look for what you can change, look for what you can learn, look for what God
effect of government spending on infrastructure, human resources, and routine expenditures and trade openness on economic growth where the types of government spending are
○ If BP elevated, think primary aldosteronism, Cushing’s, renal artery stenosis, ○ If BP normal, think hypomagnesemia, severe hypoK, Bartter’s, NaHCO3,
Taking up this call, this research on Canadian game developers, community or- ganizers, and others involved in indie games suggests that contemporary cultural pro- ducers locate