Energy conscious adaptive security
Full text
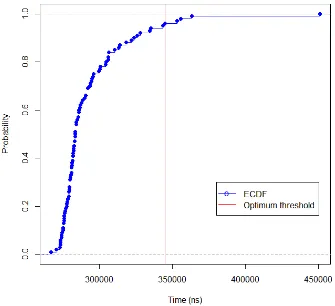
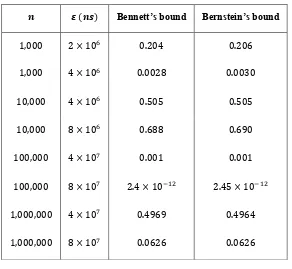
Figure




Related documents
The concept of other often is used the following attributes: students, countries, Erasmus students cultures, things, people, places, nation, languages, foreigners, side of
Aberrant control of these signaling pathways can cause the loss of the somatic distal tip cells (DTCs, which function as the germline stem cell niche) and germline stem cells as
Three is a crowd: A potential exception to an oppositional rule situates itself within the field of praxis research, a process wherein theories are performed or enacted: an
The design of a ( n, d )-multi-party circuit from BGW’s protocol is merely based on the following remark: the d -privacy for a set of n semi-honest players evaluating a function
To this end, we synthesized a small library of diazofluorene analogues with varying electronic properties to probe the MOA and assayed against the ability of the analogue library
Wu, “Half-mode substrate integrated waveguide transverse slot array antennas,” IEEE Transactions on Antennas and Propagation , Vol.. Chen, “45 ◦ linearly polarized resonant slot
Experimental study of the effects of turbine solidity, blade profile, pitch angle, surface roughness, and aspect ratio on the H‐Darrieus wind turbine self‐starting and