Utilising journey mapping and crime scripting to combat cyber crime and cyber warfare attacks
Full text
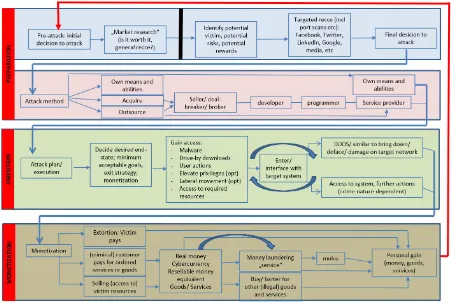
Figure
Related documents
General Graphical LCD 6 buttons Password Protection Measurement Type Supply Voltage AC Supply Voltage DC Day/Night Input Number of Steps Current Transformer Ratio Voltage
Asset utilisation Shareholder Value Shareholder Value Profit Profit Invested Capital Invested Capital Sales Sales Costs Costs Fixed Capital Fixed Capital Working Capital Working
The person who poisoned the three doctors nine years ago was one of the missing twins - the boy who had been shot in the head and saved by Tenma's surgery.. Now an adult, he
A pilot-scale fluidised bed combustor was used to burn biomass and MRFR in mixtures of various propor- tions. The effect of the MRFR waste fraction of the fuel mixture upon
sion of the genera Anema, Digitothyrea, Peccania and Thyrea from the SE Iberian Peninsula and North Africa, the authors, after examination of herbarium specimens of Algerian
Prevention Pilot and demonstration projects focused on the recognised road injury risk factors are another key area for activity within the Action Plan. The com- ponents of the
Besides signal analysis, complex-smoothed transfer functions have been successfully applied for loudspeaker- room response equalization, where the complex-smoothed impulse response
Alternator Engine stop Coolant overheat Hydraulic oil level Auto lubrication Fast-filling Tension Electric lever Emergency engine stop Top valve.. Engine over run Coolant level