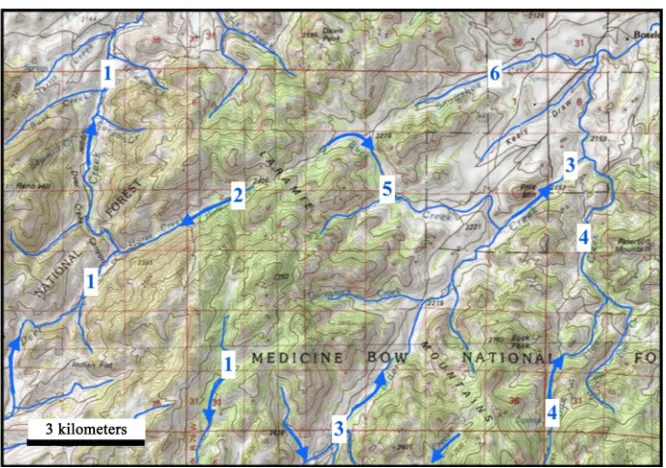
Use of Stream and Dismembered Stream Valleys Now Crossing Wyoming’s Northern Laramie Mountains to Test a Recently Proposed Regional Geomorphology Paradigm, USA
Full text
Figure



Related documents
Filing Complaints with the Federal Communications Commission (FCC) on TRS, Advanced Communications, Hearing Aid Compatibility, Mobile Phone Internet Browsers, Telephone Services
The Roxar Watercut meter can utilize density and flow measurements taken from a Coriolis flow meter in order to provide automatic compensation for changing fluid density and
Thus, assigning young intermediate students piano duos can not only develop their technical and musical skills, but can also build up the communication and collaboration skills
The U.S. Based on a Renewable Fuel Standard that mandates 15 billion gallons of ethanol from corn by 2015, some experts think that will be the upper limit in the long term.
Table 2 shows that automated cataloguing has effective control over the entire cataloguing operation in academic libraries in Oyo State Nigeria.. 39 (100.0%)
This study produces a more relevant indicator of social capital at the national level based on levels of trust (generalized trust and institutional trust), associational
Practice sits across disciplines. Functionalist and disciplinary bound theory will always struggle to
In contrast to other wallet-based solu- tions, TruWallet provides (i) strong protection for users’ credentials and sensitive data by cryptographically binding them to the
